VoIP
... VPN using GRE Tunnel GRE (Generic Route Encapsulation) is another method of creating a tunnel which can then form a VPN between two sites. The most common use of GRE tunnels is to transport legacy i.e. protocols other than IP across MPLS networks. For example a customer with a fully meshed IPVPN ov ...
... VPN using GRE Tunnel GRE (Generic Route Encapsulation) is another method of creating a tunnel which can then form a VPN between two sites. The most common use of GRE tunnels is to transport legacy i.e. protocols other than IP across MPLS networks. For example a customer with a fully meshed IPVPN ov ...
Chapter 1 - UniMAP Portal
... Need for low-cost, high-speed networks To interconnect local workstations To access local shared resources (printers, storage, servers) Low cost, high-speed communications with low error rate possible using coaxial cable Ethernet is the standard for high-speed wired access to computer networks ...
... Need for low-cost, high-speed networks To interconnect local workstations To access local shared resources (printers, storage, servers) Low cost, high-speed communications with low error rate possible using coaxial cable Ethernet is the standard for high-speed wired access to computer networks ...
Chapter 18 - William Stallings, Data and Computer
... remote access over Internet extranet & intranet connectivity for partners ...
... remote access over Internet extranet & intranet connectivity for partners ...
Document
... Each host assigned to a 32-bit number Called IP address or Internet address Unique to throughout Internet Each datagram contain IP address of source and destination ...
... Each host assigned to a 32-bit number Called IP address or Internet address Unique to throughout Internet Each datagram contain IP address of source and destination ...
Notes: Chptr 1 - UniMAP Portal
... Need for low-cost, high-speed networks To interconnect local workstations To access local shared resources (printers, storage, servers) Low cost, high-speed communications with low error rate possible using coaxial cable Ethernet is the standard for high-speed wired access to computer networks ...
... Need for low-cost, high-speed networks To interconnect local workstations To access local shared resources (printers, storage, servers) Low cost, high-speed communications with low error rate possible using coaxial cable Ethernet is the standard for high-speed wired access to computer networks ...
Chapter 6 outline
... wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers 802.11 access points ...
... wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers 802.11 access points ...
security protocols for wireless sensor network
... • After a certain period of time, the sender will disclose the secret key. • The receiver is responsible for buffering the packet until the secret key has been disclosed. • After disclosure the receiver can authenticate the packet, provided that the packet was received before the key was disclosed. ...
... • After a certain period of time, the sender will disclose the secret key. • The receiver is responsible for buffering the packet until the secret key has been disclosed. • After disclosure the receiver can authenticate the packet, provided that the packet was received before the key was disclosed. ...
Lecture Optical Communications Overview
... Shared use of network infrastructure (e.g. PON network for FTTH & dedicated wavelengths for mobile fronthaul) ...
... Shared use of network infrastructure (e.g. PON network for FTTH & dedicated wavelengths for mobile fronthaul) ...
Chapter 6 Slides
... simple physical topology • Network backbones may follow serial, distributed, collapsed, or parallel topologies • Switching manages the filtering and forwarding of packets between nodes on a network • Ethernet employs a network access method called CSMA/CD • Networks may use one (or a combination) of ...
... simple physical topology • Network backbones may follow serial, distributed, collapsed, or parallel topologies • Switching manages the filtering and forwarding of packets between nodes on a network • Ethernet employs a network access method called CSMA/CD • Networks may use one (or a combination) of ...
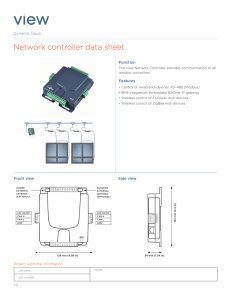
network controller data sheet
... • Operating Temperature: 0°C (32°F) to 60°C (140°F) • Storage Temperature: –20°C (–4°F) to 60°C (140°F) • Relative Humidity: 0 to 90% non–condensing ...
... • Operating Temperature: 0°C (32°F) to 60°C (140°F) • Storage Temperature: –20°C (–4°F) to 60°C (140°F) • Relative Humidity: 0 to 90% non–condensing ...
A Big Test Result - Knowledge Systems Institute
... Network Address (MAC Address) • NIC also has to advertise its own location, or address, to the rest of the network to distinguish it from all the other cards on the network. • A committee of the Institute of Electrical and Electronics Engineers (IEEE) assigns blocks of addresses to each NIC manufac ...
... Network Address (MAC Address) • NIC also has to advertise its own location, or address, to the rest of the network to distinguish it from all the other cards on the network. • A committee of the Institute of Electrical and Electronics Engineers (IEEE) assigns blocks of addresses to each NIC manufac ...
Using HiBeam Screens
... with data servers running on all targets. Each data server gathers data from resources located on their target, i.e., configurations, then relays it to the screen. However, for this network configuration, you need to set the java permissions of the browser used to view the screen to enable unsigned ...
... with data servers running on all targets. Each data server gathers data from resources located on their target, i.e., configurations, then relays it to the screen. However, for this network configuration, you need to set the java permissions of the browser used to view the screen to enable unsigned ...
Wireless Communications: Networking and - Assets
... Communications by voice and physical signaling are common means of interaction between human beings. In the simplest forms, there is an emitting entity of information and a receiving entity of information. As the sources move apart the need for telecommunications appears self-evident. This simple mo ...
... Communications by voice and physical signaling are common means of interaction between human beings. In the simplest forms, there is an emitting entity of information and a receiving entity of information. As the sources move apart the need for telecommunications appears self-evident. This simple mo ...
Wireless Communications: Networking and Management - Beck-Shop
... Communications by voice and physical signaling are common means of interaction between human beings. In the simplest forms, there is an emitting entity of information and a receiving entity of information. As the sources move apart the need for telecommunications appears self-evident. This simple mo ...
... Communications by voice and physical signaling are common means of interaction between human beings. In the simplest forms, there is an emitting entity of information and a receiving entity of information. As the sources move apart the need for telecommunications appears self-evident. This simple mo ...
September 2014 report
... While a small numbers of good quality answers were submitted, many answers were fairly weak. Many candidates also did not answer the question as set; this was particularly true for part c). B5. Imagine you have been appointed to design the network to be deployed in three new buildings on a new unive ...
... While a small numbers of good quality answers were submitted, many answers were fairly weak. Many candidates also did not answer the question as set; this was particularly true for part c). B5. Imagine you have been appointed to design the network to be deployed in three new buildings on a new unive ...
4th ed, Pt8
... the industry-leading PayloadPlus network processor which can handle traffic at 2.5 Gigabit-per-second. Network processors are an emerging and exciting class of semiconductors that combine the speed of a custom-designed chip with the flexibility and programmability of a generalpurpose microprocessor ...
... the industry-leading PayloadPlus network processor which can handle traffic at 2.5 Gigabit-per-second. Network processors are an emerging and exciting class of semiconductors that combine the speed of a custom-designed chip with the flexibility and programmability of a generalpurpose microprocessor ...
Network
... WAN Intercommunication over public networks Typically slower and more expensive than backbone or LAN ...
... WAN Intercommunication over public networks Typically slower and more expensive than backbone or LAN ...
Lecture 1 - Intro
... • An increase of 3 folds is expected by 2019 • Wireless and mobile traffic makes up 54% of global traffic • By 2019, two thirds of global traffic will be generated by non-PC devices (welcome to the IoT) ...
... • An increase of 3 folds is expected by 2019 • Wireless and mobile traffic makes up 54% of global traffic • By 2019, two thirds of global traffic will be generated by non-PC devices (welcome to the IoT) ...
Accounting of a large TCP/IP network with SAS/CPEr software for open systems at Deutsche Telekom AG
... Installation of full commercial accounting and chargeback processes in all departments of the company after deregulation Responsibility of IT users (user groups) for usage of IT resources IT department became a financial service centre, all IT services should be accounted to cost centres. ...
... Installation of full commercial accounting and chargeback processes in all departments of the company after deregulation Responsibility of IT users (user groups) for usage of IT resources IT department became a financial service centre, all IT services should be accounted to cost centres. ...
compnetwrk-print - SNGCE DIGITAL LIBRARY
... user (i.e., application) programs. The machines are connected by a communication subnet. In most wide area networks, the subnet consists of two distinct components: transmission lines and switching elements. Transmission lines move bits between machines. They can be made of copper wire, optical fibe ...
... user (i.e., application) programs. The machines are connected by a communication subnet. In most wide area networks, the subnet consists of two distinct components: transmission lines and switching elements. Transmission lines move bits between machines. They can be made of copper wire, optical fibe ...
Overview of Communications Technologies
... All packets take the same route No packet assembly device to reorder packets Normally layer 2 connection May be permanent or switched Allow guaranteed service quality levels May be used to carry datagram protocols ...
... All packets take the same route No packet assembly device to reorder packets Normally layer 2 connection May be permanent or switched Allow guaranteed service quality levels May be used to carry datagram protocols ...
Before You Begin: Assign Information Classification
... device is needed Easy to troubleshoot, since each host is connected to ...
... device is needed Easy to troubleshoot, since each host is connected to ...