Cray XC Series Network
... of the Cray XE6’s torus. Dragonfly is a “direct” network, therefore avoiding the need for external top switches and reducing the number of optical links required for a given global bandwidth. Additionally, its design builds on earlier work showing the value of low-diameter networks constructed from ...
... of the Cray XE6’s torus. Dragonfly is a “direct” network, therefore avoiding the need for external top switches and reducing the number of optical links required for a given global bandwidth. Additionally, its design builds on earlier work showing the value of low-diameter networks constructed from ...
Introduction to MPLS
... Only need to change relevant routers (end points) Coupled with encryption, gives you a secure private internetwork. End-points of tunnels my have features not available in other Internet routers. ...
... Only need to change relevant routers (end points) Coupled with encryption, gives you a secure private internetwork. End-points of tunnels my have features not available in other Internet routers. ...
Layer 3 - Ohio Supercomputer Center
... Terminology: Internet Architecture Stack Layer 4 Layer 4 End-Application Layer ...
... Terminology: Internet Architecture Stack Layer 4 Layer 4 End-Application Layer ...
Msc Jian Li 2013 - Department of Electrical and Computer
... communications because they are designed for general purposes. Compared with other technologies, the latest 4th-generation (4G) wireless technology, the 3rd Generation Partnership Project (3GPP) LTE is a promising option for smart grid WAN [5]. Wi-Fi and ZigBee are standards for short-range wireless ...
... communications because they are designed for general purposes. Compared with other technologies, the latest 4th-generation (4G) wireless technology, the 3rd Generation Partnership Project (3GPP) LTE is a promising option for smart grid WAN [5]. Wi-Fi and ZigBee are standards for short-range wireless ...
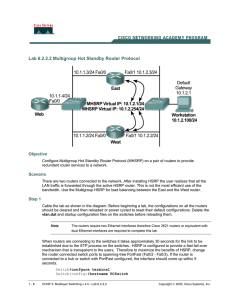
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
Using The New Console
... Your new console offers an impressive array of new features designed to make your workouts more effective and enjoyable. For instance, your new console features a web browser, which your old console did not have. However, some of the buttons on your console may no longer work. ...
... Your new console offers an impressive array of new features designed to make your workouts more effective and enjoyable. For instance, your new console features a web browser, which your old console did not have. However, some of the buttons on your console may no longer work. ...
Brochure: SteelHead Product Family
... on network bandwidth and latency still remain. Users are far away from the data and applications they are trying to access, resulting in inefficient, slower application and data delivery and poor user experience. Deploying SteelHead solutions is a great way to defeat both these problems while also s ...
... on network bandwidth and latency still remain. Users are far away from the data and applications they are trying to access, resulting in inefficient, slower application and data delivery and poor user experience. Deploying SteelHead solutions is a great way to defeat both these problems while also s ...
ICMP
... ICMP Source-Quench • Type 4 • Used when the destination computer is overwhelmed with traffic or traffic from a high speed LAN to a slower WAN connection • Asks senders to reduce the rate at which they are transmitting packets • After congestion subsides, transmission rate is increased • Most Cisco ...
... ICMP Source-Quench • Type 4 • Used when the destination computer is overwhelmed with traffic or traffic from a high speed LAN to a slower WAN connection • Asks senders to reduce the rate at which they are transmitting packets • After congestion subsides, transmission rate is increased • Most Cisco ...
Employing a secure Virtual Private Network (VPN)
... maritime forces provide joint or combined force commanders a range of options for responding to crises. ...
... maritime forces provide joint or combined force commanders a range of options for responding to crises. ...
Chapter 27 PPT
... Router R1 knows about networks 1 and 3 Router R1 does not know about network 2 (no direct connection) Router R2 knows about networks 2 and 3 Router R2 does not know about network 1 (no direct connection) ...
... Router R1 knows about networks 1 and 3 Router R1 does not know about network 2 (no direct connection) Router R2 knows about networks 2 and 3 Router R2 does not know about network 1 (no direct connection) ...
Modeling Optimal Gene Regulatory Networks
... Two graphs G and G0 with the same set of nodes (V = V 0 ) are equivalent if for each Bayesian network B = hG, Θi there exist another Bayesian network B0 = hG0 , Θ0 i such that both B and B0 define the same joint probability distribution and vice versa. ...
... Two graphs G and G0 with the same set of nodes (V = V 0 ) are equivalent if for each Bayesian network B = hG, Θi there exist another Bayesian network B0 = hG0 , Θ0 i such that both B and B0 define the same joint probability distribution and vice versa. ...
Apple Bonjour Services on the Cisco mDNS Enabled Controllers
... access even though they are connected to the same SSID and get and IP address from the same VLAN • Ability to define granular location per wired as well as wireless Bonjour Service(per Access Point or AP Group) In release 8.0 the IT administrators can define how the service instance is shared, which ...
... access even though they are connected to the same SSID and get and IP address from the same VLAN • Ability to define granular location per wired as well as wireless Bonjour Service(per Access Point or AP Group) In release 8.0 the IT administrators can define how the service instance is shared, which ...
3GPP TS 23.517 V8.0.0 (2007-12)
... performed, depending on the entity performing the routing, and depending on the traffic case, on signalling information, configuration data, and/or data base lookup. The NGN IMS, also known as "Core IMS" is a subset of the 3GPP IMS defined in TS 123 002 [10] which is restricted to the session contro ...
... performed, depending on the entity performing the routing, and depending on the traffic case, on signalling information, configuration data, and/or data base lookup. The NGN IMS, also known as "Core IMS" is a subset of the 3GPP IMS defined in TS 123 002 [10] which is restricted to the session contro ...
Network Node v1.1 Protocol Document
... Exchange Network evolves during its initial implementation. For example, the documents discuss and describe UDDI and other Registries as integral parts of the Network. Their use is implicit in the Protocol and Specification, but currently no official registries exist but they do merit discussion in ...
... Exchange Network evolves during its initial implementation. For example, the documents discuss and describe UDDI and other Registries as integral parts of the Network. Their use is implicit in the Protocol and Specification, but currently no official registries exist but they do merit discussion in ...
AL35218220
... independent directed acyclic graphs (IDAGs) and developed a methodology for resilient multipath routing using two IDAGs. Through simulations, we showed that the IDAGs approach performs significantly better than the independent trees approach in terms of increasing number of paths offered. We propose ...
... independent directed acyclic graphs (IDAGs) and developed a methodology for resilient multipath routing using two IDAGs. Through simulations, we showed that the IDAGs approach performs significantly better than the independent trees approach in terms of increasing number of paths offered. We propose ...
Chapter 1 - Introduction
... Router R1 knows about networks 1 and 3 Router R1 does not know about network 2 (no direct connection) Router R2 knows about networks 2 and 3 Router R2 does not know about network 1 (no direct connection) ...
... Router R1 knows about networks 1 and 3 Router R1 does not know about network 2 (no direct connection) Router R2 knows about networks 2 and 3 Router R2 does not know about network 1 (no direct connection) ...
ATCP: TCP for Mobile Ad Hoc Networks
... TCP periodically generates probe packets while in persist mode. When, eventually, the receiver is connected to the sender, it responds to these probe packets with a duplicate ACK (or a data packet). This removes TCP from persist mode and moves ATCP back into normal state. Benefits of ATCP How does t ...
... TCP periodically generates probe packets while in persist mode. When, eventually, the receiver is connected to the sender, it responds to these probe packets with a duplicate ACK (or a data packet). This removes TCP from persist mode and moves ATCP back into normal state. Benefits of ATCP How does t ...
4.2 Risk Assessment
... VMware® ESX Server installs directly on server hardware, or “bare metal”, and inserts a virtualisation layer between the hardware and the operating system. ESX Server partitions a physical server into multiple secure and portable virtual machines that can run side by side on the same physical server ...
... VMware® ESX Server installs directly on server hardware, or “bare metal”, and inserts a virtualisation layer between the hardware and the operating system. ESX Server partitions a physical server into multiple secure and portable virtual machines that can run side by side on the same physical server ...
Routing Protocol vs. Routed Protocol
... • A router is a type of internetworking device that passes data packets between networks, based on Layer 3 addresses. • A router has the ability to make intelligent decisions regarding the best path for delivery of data on the network. ...
... • A router is a type of internetworking device that passes data packets between networks, based on Layer 3 addresses. • A router has the ability to make intelligent decisions regarding the best path for delivery of data on the network. ...
IOSR Journal of Computer Science (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP 64-71 www.iosrjournals.org
... Multicast is one of those networking concepts that's relatively simple, though hard to explain without some background . But let me assure you, it's worth the effort to understand. Multicasting is a technical term that means that you can send a piece of data (a packet) to multiple sites at the same ...
... Multicast is one of those networking concepts that's relatively simple, though hard to explain without some background . But let me assure you, it's worth the effort to understand. Multicasting is a technical term that means that you can send a piece of data (a packet) to multiple sites at the same ...
cs2307-computer networks lab manual
... destination machines, the UDP protocol number and the byte count for the UDP segment. The pseudo-header helps to find undelivered packets or packets that arrive at the wrong address. However the pseudo-header violates the protocol hierarchy because the IP addresses which are used in it belong to the ...
... destination machines, the UDP protocol number and the byte count for the UDP segment. The pseudo-header helps to find undelivered packets or packets that arrive at the wrong address. However the pseudo-header violates the protocol hierarchy because the IP addresses which are used in it belong to the ...
IPSO-6LoWPAN - University of California, Berkeley
... RFC 2463 ICMPv6 - Internet Control Message Protocol for IPv6 RFC 2765 Stateless IP/ICMP Translation Algorithm (SIIT) RFC 3068 An Anycast Prefix for 6to4 Relay Routers RFC 3307 Allocation Guidelines for IPv6 Multicast Addresses RFC 3315 DHCPv6 - Dynamic Host Configuration Protocol for IPv6 RFC 3484 D ...
... RFC 2463 ICMPv6 - Internet Control Message Protocol for IPv6 RFC 2765 Stateless IP/ICMP Translation Algorithm (SIIT) RFC 3068 An Anycast Prefix for 6to4 Relay Routers RFC 3307 Allocation Guidelines for IPv6 Multicast Addresses RFC 3315 DHCPv6 - Dynamic Host Configuration Protocol for IPv6 RFC 3484 D ...
Nortel Secure Network Access 2.0 802.1X
... and the Network Access Protection (NAP) concurrently. These components interoperate, allowing customers to enforce security policies for network access using both NSNA and NAP. This architecture allows deployment of NAP clients with or without a Windows 2008 Server based Network Policy Server (NPS) ...
... and the Network Access Protection (NAP) concurrently. These components interoperate, allowing customers to enforce security policies for network access using both NSNA and NAP. This architecture allows deployment of NAP clients with or without a Windows 2008 Server based Network Policy Server (NPS) ...