IOSR Journal of Computer Engineering (IOSR-JCE)
... infrastructure to be available at the site, and that some of the devices in the data monitoring and collection network are web-enabled. A web-enabled device has a web server either integrated during the design of the device or added later as an expansion board. To distinguish such a web server from ...
... infrastructure to be available at the site, and that some of the devices in the data monitoring and collection network are web-enabled. A web-enabled device has a web server either integrated during the design of the device or added later as an expansion board. To distinguish such a web server from ...
S-72.423 Telecommunication Systems
... The PSTN is optimized for fixed speech service, statistically distributed, analog subscribers (by using the circuit switching technology that was made available beginning of this century). Support for data traffic "artificially added" by modems ISDN (integrated into exchanges) xDSL (x digital ...
... The PSTN is optimized for fixed speech service, statistically distributed, analog subscribers (by using the circuit switching technology that was made available beginning of this century). Support for data traffic "artificially added" by modems ISDN (integrated into exchanges) xDSL (x digital ...
Presentation ( format)
... Hidden Terminal effect • CSMA inefficient in presence of hidden terminals • Hidden terminals: A and B cannot hear each other because of obstacles or signal attenuation; so, their packets collide at B • Solution? CSMA + RTS/CTS ...
... Hidden Terminal effect • CSMA inefficient in presence of hidden terminals • Hidden terminals: A and B cannot hear each other because of obstacles or signal attenuation; so, their packets collide at B • Solution? CSMA + RTS/CTS ...
Lab I: Internet services. Telnet (SSH), E
... FTP is a reliable, connection-oriented service that uses TCP to transfer files between systems that support FTP. The main purpose of FTP is to transfer files from one computer to another by copying and moving files from servers to clients, and from clients to servers. When files are copied from a se ...
... FTP is a reliable, connection-oriented service that uses TCP to transfer files between systems that support FTP. The main purpose of FTP is to transfer files from one computer to another by copying and moving files from servers to clients, and from clients to servers. When files are copied from a se ...
20070213-boyd
... • Internet2 is leveraged to help provide diagnostic information for “backbone” portion of problem • Create *some* diagnostic tools • Make network data as public as is reasonable • Work on efforts to more widely make performance data available (perfSONAR) • Contribute to ‘base’ perfSONAR development ...
... • Internet2 is leveraged to help provide diagnostic information for “backbone” portion of problem • Create *some* diagnostic tools • Make network data as public as is reasonable • Work on efforts to more widely make performance data available (perfSONAR) • Contribute to ‘base’ perfSONAR development ...
Payload Attribution via Hierarchical Bloom Filters
... Current Forensic Server has 1.3TB of storage with over 3 months worth of data from the edge-router and two subnets Normal bandwidth consumption of network is about a 1 – 2 TB/day Synopses reduces this traffic to about 20GB/day A 4TB Forensic Server will take over operations in July ...
... Current Forensic Server has 1.3TB of storage with over 3 months worth of data from the edge-router and two subnets Normal bandwidth consumption of network is about a 1 – 2 TB/day Synopses reduces this traffic to about 20GB/day A 4TB Forensic Server will take over operations in July ...
20070213-boyd
... • Internet2 is leveraged to help provide diagnostic information for “backbone” portion of problem • Create *some* diagnostic tools • Make network data as public as is reasonable • Work on efforts to more widely make performance data available (perfSONAR) • Contribute to ‘base’ perfSONAR development ...
... • Internet2 is leveraged to help provide diagnostic information for “backbone” portion of problem • Create *some* diagnostic tools • Make network data as public as is reasonable • Work on efforts to more widely make performance data available (perfSONAR) • Contribute to ‘base’ perfSONAR development ...
Users Manual
... motes , which collect and relay data, and a Network Manager that monitors and manages network performance and security, and exchanges data with a host application. SmartMesh networks communicate using a Time Slotted Channel Hopping (TSCH) link layer, pioneered by Linear's Dust Networks group. In a T ...
... motes , which collect and relay data, and a Network Manager that monitors and manages network performance and security, and exchanges data with a host application. SmartMesh networks communicate using a Time Slotted Channel Hopping (TSCH) link layer, pioneered by Linear's Dust Networks group. In a T ...
Wireless adapter sleep scheduling based on video streaming video?
... the wireless adapter [7], dynamically switching between single and multiple antenna use [8], and also by scheduling the sleep cycles of mobile devices [9]. In the case of our wireless video streaming scenario the most suitable method is the sleep scheduling based power saving technologies, since it ...
... the wireless adapter [7], dynamically switching between single and multiple antenna use [8], and also by scheduling the sleep cycles of mobile devices [9]. In the case of our wireless video streaming scenario the most suitable method is the sleep scheduling based power saving technologies, since it ...
Chapter 13
... NSFNET attached to ARPANET via 1 core router Core had explicit routes to all destinations in NSFNET NSFNET routers knew about local destinations Had default route to non-NSFNET traffic via core ...
... NSFNET attached to ARPANET via 1 core router Core had explicit routes to all destinations in NSFNET NSFNET routers knew about local destinations Had default route to non-NSFNET traffic via core ...
37 - BSNL Durg SSA(Connecting India)
... Advances in technology have dramatically improved the price/performance equation of FSS (Fixed Service Satellite) over the past five years. New VSAT systems are coming online using Ka band technology that promise higher bandwidth rates for lower costs. FSS satellite systems currently in orbit have a ...
... Advances in technology have dramatically improved the price/performance equation of FSS (Fixed Service Satellite) over the past five years. New VSAT systems are coming online using Ka band technology that promise higher bandwidth rates for lower costs. FSS satellite systems currently in orbit have a ...
Simplifying Manageability, Scalability and Host Mobility in
... and a large number of host-devices which can either directly connect to veil-switches or through Ethernet based Wired/Wireless LAN switches. The roles of each of these devices are as follows. vcc. It bootstraps the network by performing the initial vid -assignment to veil-switches. In addition, it a ...
... and a large number of host-devices which can either directly connect to veil-switches or through Ethernet based Wired/Wireless LAN switches. The roles of each of these devices are as follows. vcc. It bootstraps the network by performing the initial vid -assignment to veil-switches. In addition, it a ...
... standard was adopted as IS136. However, the market was in the USA basically. European TDMA standard is GSM nowadays, which is familiar to all. GSM was put into service since 1991. Till the end of 1997, it operated in more than 100 countries, which was actual standard for Europe and Asia. The GSM dig ...
Internet Traffic Patterns
... – The network card of the monitor node runs in promiscuous mode – The monitor node is responsible for capturing and analysing all the data – Can be used at home in a wireless LAN or even with only a dial-up modem ...
... – The network card of the monitor node runs in promiscuous mode – The monitor node is responsible for capturing and analysing all the data – Can be used at home in a wireless LAN or even with only a dial-up modem ...
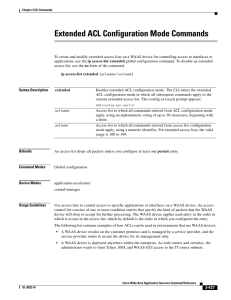
Extended ACL Configuration Mode Commands
... the current condition entries, to delete a specific entry, or to change the order in which the entries will be evaluated. To return to global configuration mode, enter exit at the ACL configuration mode prompt. To create an entry, use a deny or permit keyword and specify the type of packets that you ...
... the current condition entries, to delete a specific entry, or to change the order in which the entries will be evaluated. To return to global configuration mode, enter exit at the ACL configuration mode prompt. To create an entry, use a deny or permit keyword and specify the type of packets that you ...
Communications and Networks
... • A wireless modem uses the cell phone network to connect to the Internet wirelessly from a notebook computer, a smart phone, or other ...
... • A wireless modem uses the cell phone network to connect to the Internet wirelessly from a notebook computer, a smart phone, or other ...
Heterogeneous wireless network management
... while maintaining a desired QoS. During program execution communication interfaces are placed in low-power states depending upon their acces patterns and application performance needs. The techniques developed to date for the enhancement of heterogeneous networks concentrate on improving their acces ...
... while maintaining a desired QoS. During program execution communication interfaces are placed in low-power states depending upon their acces patterns and application performance needs. The techniques developed to date for the enhancement of heterogeneous networks concentrate on improving their acces ...
Chapter 09-Communication and Network
... • A wireless modem uses the cell phone network to connect to the Internet wirelessly from a notebook computer, a smart phone, or other ...
... • A wireless modem uses the cell phone network to connect to the Internet wirelessly from a notebook computer, a smart phone, or other ...
TCP/IP Networking Basics
... Single IP Address Operation Using NAT In the past, if multiple computers on a LAN needed to access the Internet simultaneously, you had to obtain a range of IP addresses from the ISP. This type of Internet account is more costly than a single-address account typically used by a single user with a mo ...
... Single IP Address Operation Using NAT In the past, if multiple computers on a LAN needed to access the Internet simultaneously, you had to obtain a range of IP addresses from the ISP. This type of Internet account is more costly than a single-address account typically used by a single user with a mo ...
Internet History and Architecture - ECSE
... 3. [7 pts] How does IP solve the internetworking problems of heterogeneity and scale ? Discuss how the issues of address resolution, address space aggregation, and fragmentation arise, and how they relate to the above problems? IP uses the overlay approach to internetworking. By this we mean that i ...
... 3. [7 pts] How does IP solve the internetworking problems of heterogeneity and scale ? Discuss how the issues of address resolution, address space aggregation, and fragmentation arise, and how they relate to the above problems? IP uses the overlay approach to internetworking. By this we mean that i ...
DZ21798800
... communications only. Ex.: An iPod, iPad, Android cell phone, a NetBook or any hardware device that may need to connect wirelessly for that matter Box: The USB to Wi-Fi Bridge. This is the unit which is the subject of development. Cylinder: A sample USB device connected on USB port to Box. Ex.: A cam ...
... communications only. Ex.: An iPod, iPad, Android cell phone, a NetBook or any hardware device that may need to connect wirelessly for that matter Box: The USB to Wi-Fi Bridge. This is the unit which is the subject of development. Cylinder: A sample USB device connected on USB port to Box. Ex.: A cam ...
an architectural survey
... Broadly speaking, programmable networks denote networks that can tune itself, or reconfigure itself, through a software-based adaptation - typically managed through an application programmer interface (API). Incorporation of functionality in software allows networks to innovate at the rate of softwa ...
... Broadly speaking, programmable networks denote networks that can tune itself, or reconfigure itself, through a software-based adaptation - typically managed through an application programmer interface (API). Incorporation of functionality in software allows networks to innovate at the rate of softwa ...
Slides - Sigmobile
... RSS measurements taken on each TDMA frame Control packets used to measure RSS Link RSS used to compute SIR threshold per PHY rate Measurement complexity reduced to O (N ) ...
... RSS measurements taken on each TDMA frame Control packets used to measure RSS Link RSS used to compute SIR threshold per PHY rate Measurement complexity reduced to O (N ) ...
IOSR Journal of Electronics and Communication Engineering (IOSRJECE)
... 1.1 Why Would I Need a Router? For most home users, they may want to set-up a LAN (local Area Network) or WLAN (wireless LAN) and connect all computers to the Internet without having to pay a full broadband subscription service to their ISP for each computer on the network. In many instances, an ISP ...
... 1.1 Why Would I Need a Router? For most home users, they may want to set-up a LAN (local Area Network) or WLAN (wireless LAN) and connect all computers to the Internet without having to pay a full broadband subscription service to their ISP for each computer on the network. In many instances, an ISP ...