Networking
... Information will only be passed to the centralized network management system if at the request by the central manager or certain predefined error conditions occur on a subnet. See Figure 15-19. SNMP2 works transparently with AppleTalk, IPX, and OSI transport protocols. SNMP2 allows not just monitori ...
... Information will only be passed to the centralized network management system if at the request by the central manager or certain predefined error conditions occur on a subnet. See Figure 15-19. SNMP2 works transparently with AppleTalk, IPX, and OSI transport protocols. SNMP2 allows not just monitori ...
Wang, Ch. 18 - Internet Protocol Addresses
... – 1 bits mark the network prefix – 0 bits mark the host portion – Subnet addressing was in use for a decade before the idea was extended to classless addressing ...
... – 1 bits mark the network prefix – 0 bits mark the host portion – Subnet addressing was in use for a decade before the idea was extended to classless addressing ...
cns-208 citrix netscaler 10.5 essentials for ace
... The objective of the Citrix NetScaler 10.5 Essentials for ACE Migration course is to provide the foundational concepts and advanced skills necessary to migrate from a Cisco ACE ADC to NetScaler, and to implement, configure, secure, monitor, optimize, and troubleshoot a NetScaler system from within a ...
... The objective of the Citrix NetScaler 10.5 Essentials for ACE Migration course is to provide the foundational concepts and advanced skills necessary to migrate from a Cisco ACE ADC to NetScaler, and to implement, configure, secure, monitor, optimize, and troubleshoot a NetScaler system from within a ...
Wireless Router Setup Manual
... router’s SSID, channel, or security settings, you will lose your wireless connection when you click Apply. You must then change the wireless settings of your computer to match the router’s new settings. 6. Configure and test your computers for wireless connectivity. Program the wireless adapter of y ...
... router’s SSID, channel, or security settings, you will lose your wireless connection when you click Apply. You must then change the wireless settings of your computer to match the router’s new settings. 6. Configure and test your computers for wireless connectivity. Program the wireless adapter of y ...
Distributed Denial of Service Attacks
... network domain hosts where attacks originated (most originated from cable ISPs). • ISP Verio set up packet filters on their router so that DDoS packets were not allowed on to the T1 ...
... network domain hosts where attacks originated (most originated from cable ISPs). • ISP Verio set up packet filters on their router so that DDoS packets were not allowed on to the T1 ...
Using Protocols in Computer Networks A.L. Hassan Harith
... The communications systems provide a vehicle of carrying information from one point to another by conditioning it appropriately. The conditioning may include changing the actual shape of the information, or even adding to and removing parts of it. Example of changing the actual shape of the informat ...
... The communications systems provide a vehicle of carrying information from one point to another by conditioning it appropriately. The conditioning may include changing the actual shape of the information, or even adding to and removing parts of it. Example of changing the actual shape of the informat ...
Chapter 4: Advanced Internetworking
... networks (they are usually called service provider networks, and they are operated by private companies rather than the government) Sites are connected to each other in arbitrary ways ...
... networks (they are usually called service provider networks, and they are operated by private companies rather than the government) Sites are connected to each other in arbitrary ways ...
Delivery, and IP Packet Forwarding
... List the three next-hop methods for packet forwarding. List the three next-hop methods for packet forwarding. List the four most basic fields in routing entries. Explain step-by-step how a router forwards an IP packet to the next router (or host). You need to use, in the explanation, the terms: dest ...
... List the three next-hop methods for packet forwarding. List the three next-hop methods for packet forwarding. List the four most basic fields in routing entries. Explain step-by-step how a router forwards an IP packet to the next router (or host). You need to use, in the explanation, the terms: dest ...
Security in Automotive Domain Using Secure Socket Layer
... users and not to any imposter. In this paper there is a detailed description of SSL protocol [5]. Begin with the structure of SSL, its position in the network architecture, the later portion of this paper covers the various communication networks used in cars and an approach to provide secure vehicl ...
... users and not to any imposter. In this paper there is a detailed description of SSL protocol [5]. Begin with the structure of SSL, its position in the network architecture, the later portion of this paper covers the various communication networks used in cars and an approach to provide secure vehicl ...
Performance Analysis of Bus Topology in Fiber Optic
... Optical network uses optical multiplexing and switching technique to increase its capacity. The implementation of time multiplexers, demultiplexers and encoders/decoders at terabits per second is very difficult in networks. Optical network topologies such as bus, star and tree reduces complexity by ...
... Optical network uses optical multiplexing and switching technique to increase its capacity. The implementation of time multiplexers, demultiplexers and encoders/decoders at terabits per second is very difficult in networks. Optical network topologies such as bus, star and tree reduces complexity by ...
networking standards and the osi model
... Organizations (continued) • IAB (Internet Architecture Board) is a technical advisory group of researchers and technical professionals interested in overseeing the Internet’s design and management ...
... Organizations (continued) • IAB (Internet Architecture Board) is a technical advisory group of researchers and technical professionals interested in overseeing the Internet’s design and management ...
Networking BASICS
... Multichannel Multipoint Distribution Service (MMDS) uses lowfrequency signals that can travel farther, are less susceptible to interference from rain and fog, and are better able to penetrate buildings than high-frequency LMDS signals. MMDS can send data signals at 1.5 Mbps downstream and 300 Kbps u ...
... Multichannel Multipoint Distribution Service (MMDS) uses lowfrequency signals that can travel farther, are less susceptible to interference from rain and fog, and are better able to penetrate buildings than high-frequency LMDS signals. MMDS can send data signals at 1.5 Mbps downstream and 300 Kbps u ...
00208r1P802-15_TG3-MAC-LAYER-PRES - IEEE-SA
... TDMA protocol at the MAC layer. It provides for real-time transport of a number of real-time data streams while offering the advantages of quick time to market via the use of proven technology and low system cost due to the use of simple receivers and transmitters. It also provides for the low power ...
... TDMA protocol at the MAC layer. It provides for real-time transport of a number of real-time data streams while offering the advantages of quick time to market via the use of proven technology and low system cost due to the use of simple receivers and transmitters. It also provides for the low power ...
Introduction to Operating Systems
... • “Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and (with appropriate hardware) can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet also supports plugins ...
... • “Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and (with appropriate hardware) can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet also supports plugins ...
Phone-glish - Women With Disabilities Australia
... Ethernet is the name of the most commonly used type of Local Area Network (LAN). Ethernet LANs are used in offices to link computers together using wires. See also WiFi. The plug for an Ethernet cable looks like the one for your home phone but is just a bit bigger. ...
... Ethernet is the name of the most commonly used type of Local Area Network (LAN). Ethernet LANs are used in offices to link computers together using wires. See also WiFi. The plug for an Ethernet cable looks like the one for your home phone but is just a bit bigger. ...
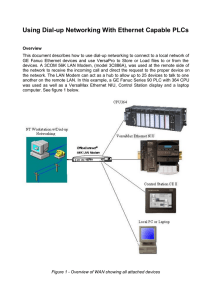
Using Dial-up Networking With Ethernet Capable PLCs
... The configuration starts with the dial-up PC. If Dial-up Networking is not already installed on the PC you will need to install it now before proceeding. Once installed, create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentica ...
... The configuration starts with the dial-up PC. If Dial-up Networking is not already installed on the PC you will need to install it now before proceeding. Once installed, create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentica ...
Hijacking Label Switched Networks in the Cloud
... Renesys reported a major BGP hijacking in 2013 - Belaruse and Iceland ISP’s possibly compromised - A software bug blamed ...
... Renesys reported a major BGP hijacking in 2013 - Belaruse and Iceland ISP’s possibly compromised - A software bug blamed ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... network of individual cells known as base stations where each station covers a small geographical area which is part of a uniquely identified location area. If the coverage area of these base stations is integrated, a cellular network provides radio coverage over a much wider area. The group of thes ...
... network of individual cells known as base stations where each station covers a small geographical area which is part of a uniquely identified location area. If the coverage area of these base stations is integrated, a cellular network provides radio coverage over a much wider area. The group of thes ...
IPO-10
... A fixed bandwidth connection between an ingress port and an egress port across the optical transport network. Optical Connection Behavior Defined by its Attributes: identification-based: unique connection ID, contract ID, user group ID, source and destination identifiers (address, port, channel ...
... A fixed bandwidth connection between an ingress port and an egress port across the optical transport network. Optical Connection Behavior Defined by its Attributes: identification-based: unique connection ID, contract ID, user group ID, source and destination identifiers (address, port, channel ...
ppt
... • Broadcast – FF:FF:FF:FF:FF:FF is “everybody” • Range of addresses allocated to multicast • Adapter maintains list of multicast groups node is interested in ...
... • Broadcast – FF:FF:FF:FF:FF:FF is “everybody” • Range of addresses allocated to multicast • Adapter maintains list of multicast groups node is interested in ...
Presentazione di PowerPoint
... belonging to religious / philosophical / political / workers organization ...
... belonging to religious / philosophical / political / workers organization ...
3rd Edition: Chapter 4 - International Institute of
... Advertises some or all prefixes learnt from eBGP Advertises ISP’s customer prefixes (For example a network that is recently allocated to some customer) These are not directly connected but form a fully connected logical graph ...
... Advertises some or all prefixes learnt from eBGP Advertises ISP’s customer prefixes (For example a network that is recently allocated to some customer) These are not directly connected but form a fully connected logical graph ...