IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... Emerging of wireless CDMA telephony in the 1980swith tremendous benefits of CDMA such as a merit of Spread Spectrum (SS) pushes some researchers to transfer principles and advantages of CDMA into optical communication networks [1, 2, 3].The first experiment that demonstrates the feasibility of imple ...
... Emerging of wireless CDMA telephony in the 1980swith tremendous benefits of CDMA such as a merit of Spread Spectrum (SS) pushes some researchers to transfer principles and advantages of CDMA into optical communication networks [1, 2, 3].The first experiment that demonstrates the feasibility of imple ...
ppt
... More flexible (different path for each flow) Can reserve bandwidth at connection setup Easier for hardware implementations ...
... More flexible (different path for each flow) Can reserve bandwidth at connection setup Easier for hardware implementations ...
Bridges
... + Arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing prots) + Provide firewall protection against broadcast storms - Require IP address configuration (not plug and play) - Require higher processing bandwidth Bridges do well in small (few hundred hosts) whil ...
... + Arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing prots) + Provide firewall protection against broadcast storms - Require IP address configuration (not plug and play) - Require higher processing bandwidth Bridges do well in small (few hundred hosts) whil ...
What is TCP Connection Forwarding? Why should I perform TCP
... a way that maximizes resources and minimizes points of failure. Good network design often includes redundant hardware and data paths to ensure high availability, creating multiple paths from one network node to another so that no single failure along the way blocks communication between them. If ach ...
... a way that maximizes resources and minimizes points of failure. Good network design often includes redundant hardware and data paths to ensure high availability, creating multiple paths from one network node to another so that no single failure along the way blocks communication between them. If ach ...
An end-to-end network slicing framework for 5G wireless
... In late 4G and early 5G, the wireless industry started to vertically slice big mobile broadband network into multiple virtual networks to serve vertical industries and applications in a more cost efficient manner. Each network slice can have different network architecture, and different application ...
... In late 4G and early 5G, the wireless industry started to vertically slice big mobile broadband network into multiple virtual networks to serve vertical industries and applications in a more cost efficient manner. Each network slice can have different network architecture, and different application ...
An Extended AODV Protocol for VoIP HuiYao Zhang Marek E. Bialkowski
... adverse properties of the wireless channel, dynamic topology and the lack of central administration. Because of these limitations, there is a challenge to meet the Quality of Service (QoS) of VoIP in terms of packet delivery ratio (PDR) and end-to-end (E2E) delay that has to be within an acceptable ...
... adverse properties of the wireless channel, dynamic topology and the lack of central administration. Because of these limitations, there is a challenge to meet the Quality of Service (QoS) of VoIP in terms of packet delivery ratio (PDR) and end-to-end (E2E) delay that has to be within an acceptable ...
Authentication Key - Pravin Shetty > Resume
... amount of information reaching a network-capable program. The above is an advantage because those programs are general in nature and are likely to be trusting and can ...
... amount of information reaching a network-capable program. The above is an advantage because those programs are general in nature and are likely to be trusting and can ...
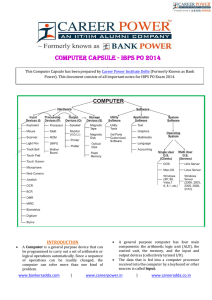
COMPUTER CAPSULE - IBPS PO 2014 . INTRODUCTION
... The set of instructions, which control the sequence of operations, are known as Program. It is a sequence of instructions, written to perform a specified task with a computer. A Software instructs the computer what to do and how to do it. It is a set of instructions that tells the computer about the ...
... The set of instructions, which control the sequence of operations, are known as Program. It is a sequence of instructions, written to perform a specified task with a computer. A Software instructs the computer what to do and how to do it. It is a set of instructions that tells the computer about the ...
1p - Villanova Computer Science
... • Propagate valid signals as well as collisions • Do not have hardware (MAC) addresses ...
... • Propagate valid signals as well as collisions • Do not have hardware (MAC) addresses ...
The Transport Layer
... 2. Reduce packet count to reduce software overhead. 3. Minimize context switches. 4. Minimize copying. 5. You can buy more bandwidth but not lower delay. 6. Avoiding congestion is better than recovering from it. 7. Avoid timeouts. ...
... 2. Reduce packet count to reduce software overhead. 3. Minimize context switches. 4. Minimize copying. 5. You can buy more bandwidth but not lower delay. 6. Avoiding congestion is better than recovering from it. 7. Avoid timeouts. ...
A Comparative Analysis of Different Routing Scheme in Opportunistic Network Minakshi
... usefulness of networks encountering regular and extended durable partitions. OPPNETs are expected to manage situations including heterogeneity of guidelines, irregular network between nearby nodes. The key issue of directing for OPPNET is to locate an entrepreneurial availability between the nodes a ...
... usefulness of networks encountering regular and extended durable partitions. OPPNETs are expected to manage situations including heterogeneity of guidelines, irregular network between nearby nodes. The key issue of directing for OPPNET is to locate an entrepreneurial availability between the nodes a ...
HRG Series DVR Helpful Network Setup Tips
... Forward a range of 10 port values for any given DVR, even if the DVR isn’t using all of them. It’s possible that future DVR firmware versions might make use of additional ports. Forwarding a range of 10 port values will leave "room" to accommodate those future port numbers. For example, forward rang ...
... Forward a range of 10 port values for any given DVR, even if the DVR isn’t using all of them. It’s possible that future DVR firmware versions might make use of additional ports. Forwarding a range of 10 port values will leave "room" to accommodate those future port numbers. For example, forward rang ...
Slides 2 - USC Upstate: Faculty
... BGP (Border Gateway Protocol): the de facto inter-domain routing protocol “glue that holds the Internet together” ...
... BGP (Border Gateway Protocol): the de facto inter-domain routing protocol “glue that holds the Internet together” ...
Ethernet: An Introduction Carrier Sense Multiple Access with
... sending frames because the network interface layer (hardware) does not understand IP addresses. Mapping between a protocol (IP address) and a hardware (Ethernet address) is called address resolution. A host or a router uses address resolution when it needs to send to another computer on the same phy ...
... sending frames because the network interface layer (hardware) does not understand IP addresses. Mapping between a protocol (IP address) and a hardware (Ethernet address) is called address resolution. A host or a router uses address resolution when it needs to send to another computer on the same phy ...
module03-ipaddrV2
... Broadcast address – Host number is all ones, e.g., 128.143.255.255 – Broadcast goes to all hosts on the network – Often ignored due to security concerns ...
... Broadcast address – Host number is all ones, e.g., 128.143.255.255 – Broadcast goes to all hosts on the network – Often ignored due to security concerns ...
Smart Gird Energy Training Coalition
... removed. Different brands and different models of devices can also use the same charger. • Renders the design and fabrication of much smaller devices without the attachment of batteries. • Provides better product durability (e.g., waterproof and dustproof) for contact-free devices. • Enhances flexib ...
... removed. Different brands and different models of devices can also use the same charger. • Renders the design and fabrication of much smaller devices without the attachment of batteries. • Provides better product durability (e.g., waterproof and dustproof) for contact-free devices. • Enhances flexib ...
Moodle-5 - Willingdon College, Sangli
... occurs. When the network is busy collision occurs several times. These number of collision are minimized by using certain mechanics. Carrier sensing is one of the mechanism that listen to the network before transmit its data. If the required device is busy then computer stops transmitting until the ...
... occurs. When the network is busy collision occurs several times. These number of collision are minimized by using certain mechanics. Carrier sensing is one of the mechanism that listen to the network before transmit its data. If the required device is busy then computer stops transmitting until the ...
PowerPoint 演示文稿 - Sun Yat
... arrows on the path meet either head-to-tail or tail-to-tail at the node and this node is in Z the arrows meet head-to-head at the node, and neither the node, nor any of its descendants, is in Z ...
... arrows on the path meet either head-to-tail or tail-to-tail at the node and this node is in Z the arrows meet head-to-head at the node, and neither the node, nor any of its descendants, is in Z ...
MOBILE/WIRELESS NETWORKS
... Solves issue with topologically correct sender addresses Still inefficient since all packets (forward and reverse) go through home agent ...
... Solves issue with topologically correct sender addresses Still inefficient since all packets (forward and reverse) go through home agent ...
Policy enforcement in Peer-to-Peer networks using open
... systems every nodes can share the resource of each other resources without intervention of server, [10] so computer can behave either as server or client depending on resource share request. Despite these advantage p2p systems comes with many inherent security flaws because of its working structure. ...
... systems every nodes can share the resource of each other resources without intervention of server, [10] so computer can behave either as server or client depending on resource share request. Despite these advantage p2p systems comes with many inherent security flaws because of its working structure. ...
Assessment of the Power Series Routing Algorithm in Translucent
... We used a version of the SIMTON simulator [10] for translucent networks to assess the network performance both in the planning and in the operation phases. The SIMTON simulator uses the physical layer model proposed by Pereira et al. [9] that quantifies the OSNR degradation and the pulse broadening ...
... We used a version of the SIMTON simulator [10] for translucent networks to assess the network performance both in the planning and in the operation phases. The SIMTON simulator uses the physical layer model proposed by Pereira et al. [9] that quantifies the OSNR degradation and the pulse broadening ...
FYI on Questions and Answers-Answers to Commonly asked" New
... How do I find out if a site has a computer on the Internet? Frankly, it’s almost impossible to find out if a site has a computer on the Internet by querying some Internet service itself. The most reliable way is to ask someone at the site you are interested in contacting. It is sometimes possible to ...
... How do I find out if a site has a computer on the Internet? Frankly, it’s almost impossible to find out if a site has a computer on the Internet by querying some Internet service itself. The most reliable way is to ask someone at the site you are interested in contacting. It is sometimes possible to ...
Network Access Control for Mobile Ad Hoc Network
... Proposed Scheme - outline • Basic idea – Cryptography-oriented (using group key) – Authenticate all the packets with a networkwide access control (group session) key. – Any “bogus” packet that has incorrect authentication information will be filtered out immediately. – As a result, illegitimate node ...
... Proposed Scheme - outline • Basic idea – Cryptography-oriented (using group key) – Authenticate all the packets with a networkwide access control (group session) key. – Any “bogus” packet that has incorrect authentication information will be filtered out immediately. – As a result, illegitimate node ...
(PPT, 172KB)
... upon the data that is transmitted between nodes in the network, the nodes that are at higher levels in the hierarchy will be required to perform more processing operations on behalf of other nodes than the nodes that are lower in the hierarchy. Such a type of network topology is very useful and high ...
... upon the data that is transmitted between nodes in the network, the nodes that are at higher levels in the hierarchy will be required to perform more processing operations on behalf of other nodes than the nodes that are lower in the hierarchy. Such a type of network topology is very useful and high ...