p1568938335-dutta - Computer Science, Columbia University
... protocols defined by the Internet Engineering Task Force (IETF) to provide security protections such as authentication, privacy protection, and data integrity protection, do not have sufficient capabilities to support seamless mobility. For example, ...
... protocols defined by the Internet Engineering Task Force (IETF) to provide security protections such as authentication, privacy protection, and data integrity protection, do not have sufficient capabilities to support seamless mobility. For example, ...
- SCT Web Site
... through microwave signals o Direct broadcast satellite (DBS)—consumer satellite technology that receives digital TV signals through a reception dish o Requires the computer system to have a special communications device called a network access point—sends and receives data between computer that cont ...
... through microwave signals o Direct broadcast satellite (DBS)—consumer satellite technology that receives digital TV signals through a reception dish o Requires the computer system to have a special communications device called a network access point—sends and receives data between computer that cont ...
SmartConnect WINC1500 Wireless Network Controller
... THIS DOCUMENT, EVEN IF ATMEL HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Atmel makes no representations or warranties with respect to the accuracy or completeness of the contents of this document and reserves the right to make changes to specifications and products descriptions at any time ...
... THIS DOCUMENT, EVEN IF ATMEL HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Atmel makes no representations or warranties with respect to the accuracy or completeness of the contents of this document and reserves the right to make changes to specifications and products descriptions at any time ...
ppt
... rises dramatically and eventually results in slow network response. The exact number of machines that a single Ethernet segment can handle depends upon the applications being used, but it is generally considered that between 40 and 70 users are the limit before network speed is compromised. ...
... rises dramatically and eventually results in slow network response. The exact number of machines that a single Ethernet segment can handle depends upon the applications being used, but it is generally considered that between 40 and 70 users are the limit before network speed is compromised. ...
Chapter 6
... destination, based on the routing information. • Routing Table: – A compilation of all the networks (and sometimes hosts) that the router can reach – Entries in the routing table are known as “routes” and consist of a network address, a “next hop” (the IP address of the next router in the path to th ...
... destination, based on the routing information. • Routing Table: – A compilation of all the networks (and sometimes hosts) that the router can reach – Entries in the routing table are known as “routes” and consist of a network address, a “next hop” (the IP address of the next router in the path to th ...
3rd Edition: Chapter 4
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
Why Security??
... A new course that provides students with in-depth network security education and develop a comprehensive understanding of network security concepts Provides students with knowledge and skills to design and support Network Security Provides an experience-oriented course to prepare for entry-lev ...
... A new course that provides students with in-depth network security education and develop a comprehensive understanding of network security concepts Provides students with knowledge and skills to design and support Network Security Provides an experience-oriented course to prepare for entry-lev ...
COMP211_Topic6_Link
... A caches (saves) IP-toMAC address pair in its ARP table until information becomes old (times out) soft state: information that times out (goes away) unless refreshed ...
... A caches (saves) IP-toMAC address pair in its ARP table until information becomes old (times out) soft state: information that times out (goes away) unless refreshed ...
A Reductionist view of Network Information Theory
... with a “bit pipe” of corresponding capacity. ...
... with a “bit pipe” of corresponding capacity. ...
ChowCyberSecuritySymposiumPoster
... beta test their new MIND network analysis tool. The network status information collected and analyzed by the MIND can be used for selecting proxy server sites. Pick and choose a geographically diverse set of proxy servers for indirect routing is a challenging research problem. SCOLD technologies can ...
... beta test their new MIND network analysis tool. The network status information collected and analyzed by the MIND can be used for selecting proxy server sites. Pick and choose a geographically diverse set of proxy servers for indirect routing is a challenging research problem. SCOLD technologies can ...
Part I: Introduction - University of Massachusetts Amherst
... point and threshold location) EF router needs only 15% add’l buffer to yield same loss rates to low priority traffic as AF ...
... point and threshold location) EF router needs only 15% add’l buffer to yield same loss rates to low priority traffic as AF ...
Pocket Guide - Industrial Networking Solutions
... In 1984 Hirschmann created the first fiber optic ETHERNET network at the University of Stuttgart. In 1990 Hirschmann also invented the ”Redundant ETHERNET Ring“ and finally in 1998 we brought out the HIPER-Ring (Hirschmann Performance Redundancy Ring) in switched ETHERNET. Hirschmann is the only ma ...
... In 1984 Hirschmann created the first fiber optic ETHERNET network at the University of Stuttgart. In 1990 Hirschmann also invented the ”Redundant ETHERNET Ring“ and finally in 1998 we brought out the HIPER-Ring (Hirschmann Performance Redundancy Ring) in switched ETHERNET. Hirschmann is the only ma ...
CCIE Security Written Exam Study Guide
... quality and value. Each book is authored with attention to detail, undergoing strenuous development that involves input from a variety of technical experts. For technical support on this book, please visit: www.securityie.com Readers’ feedback is a natural part of this process. If you have any comme ...
... quality and value. Each book is authored with attention to detail, undergoing strenuous development that involves input from a variety of technical experts. For technical support on this book, please visit: www.securityie.com Readers’ feedback is a natural part of this process. If you have any comme ...
Engineering elastic traffic in TCP-based networks: processor sharing and effective service times
... Research & Technology, Thales Nederland B.V., Huizen, The Netherlands Department of Stochastics, Amsterdam, The Netherlands 3 VU University Amsterdam, Department of Matlhematics, The Netherlands 2 CWI, ...
... Research & Technology, Thales Nederland B.V., Huizen, The Netherlands Department of Stochastics, Amsterdam, The Netherlands 3 VU University Amsterdam, Department of Matlhematics, The Netherlands 2 CWI, ...
Unit 2 - Intan Viona
... a computer system without the owner's informed consent. Adware or advertisingsupported software is any software package which automatically plays, displays, or downloads advertisements to a computer after the software is installed on it or while the application is being used. Some types of adware ar ...
... a computer system without the owner's informed consent. Adware or advertisingsupported software is any software package which automatically plays, displays, or downloads advertisements to a computer after the software is installed on it or while the application is being used. Some types of adware ar ...
What is the Access Grid?
... variety of modes. In the Access Grid environment, VNC allows a speaker to share his/her podium laptop with Access Grid display systems which can then project it at remote nodes. This is useful when a speaker wishes to give real-time demonstrations or present PowerPoint slides that include "fancy" fe ...
... variety of modes. In the Access Grid environment, VNC allows a speaker to share his/her podium laptop with Access Grid display systems which can then project it at remote nodes. This is useful when a speaker wishes to give real-time demonstrations or present PowerPoint slides that include "fancy" fe ...
Performance Analysis of Artificial Neural Network Intrusion
... Anomaly detection identifies abnormal behavior. It requires the prior construction of profiles for normal behavior of users, hosts or networks; therefore, historical data are collected over a period of normal operation. IDSs monitor current event data and use a variety of measures to distinguish bet ...
... Anomaly detection identifies abnormal behavior. It requires the prior construction of profiles for normal behavior of users, hosts or networks; therefore, historical data are collected over a period of normal operation. IDSs monitor current event data and use a variety of measures to distinguish bet ...
White Paper: GPS SpiderNET - Take it to the MAX
... work correction information to rover users so that they may derive positions with a higher accuracy than with conventional RTK. Until the release of RTCM 3.0, there will have been no official internationally accepted standard for network RTK corrections. Prior to the release of RTCM 3.0, two approac ...
... work correction information to rover users so that they may derive positions with a higher accuracy than with conventional RTK. Until the release of RTCM 3.0, there will have been no official internationally accepted standard for network RTK corrections. Prior to the release of RTCM 3.0, two approac ...
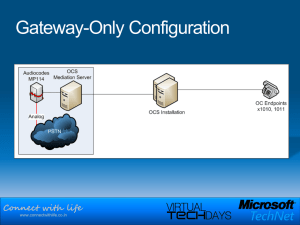
Connect with life
... The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsof ...
... The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsof ...
The Cloud in Caspian Region
... To eliminate the disruption between content and access in Caspian region TTK focuses its efforts on: Increasing the network capabilities to transmit IP traffic to major partners in CIS countries Improvement of IP connectivity with global ISP Development of own & partner data centers in Russia ...
... To eliminate the disruption between content and access in Caspian region TTK focuses its efforts on: Increasing the network capabilities to transmit IP traffic to major partners in CIS countries Improvement of IP connectivity with global ISP Development of own & partner data centers in Russia ...
tutorial13
... possibility to distribute the networking load on them between a group of servers – Candidate applications could be: Web browsers, remote login, file transfer, mail applications ...
... possibility to distribute the networking load on them between a group of servers – Candidate applications could be: Web browsers, remote login, file transfer, mail applications ...
Mobile Network Layer
... typically mobile IP cannot be used together with firewalls, special set-ups are needed (such as reverse tunneling) ...
... typically mobile IP cannot be used together with firewalls, special set-ups are needed (such as reverse tunneling) ...