Week6LectureNote
... hosts on a single network: • Actual Data • Overhead • A big part of the overhead is broadcasts. • In this context, each network is called a broadcast domain. • Switches forward broadcasts to each device connected to a switch port. • If we can reduce broadcast overhead, it would improve performance o ...
... hosts on a single network: • Actual Data • Overhead • A big part of the overhead is broadcasts. • In this context, each network is called a broadcast domain. • Switches forward broadcasts to each device connected to a switch port. • If we can reduce broadcast overhead, it would improve performance o ...
Call Data Record Generation: Options and Considerations Executive Summary
... system, and is now widely used to collect statistics on IP traffic information. NetFlow has never been an official industry standard 8; however, many would agree that NetFlow has become the unofficial industry standard due to its widespread use. Version 9 of NetFlow RFC 3954 9 forms the basis for th ...
... system, and is now widely used to collect statistics on IP traffic information. NetFlow has never been an official industry standard 8; however, many would agree that NetFlow has become the unofficial industry standard due to its widespread use. Version 9 of NetFlow RFC 3954 9 forms the basis for th ...
3rd Edition: Chapter 4
... A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lo ...
... A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lo ...
GPRS in BSS overview
... • Transactions such as Credit Card checks and a variety of telemetric applications benefit from the fast session set-ups. • GPRS enables efficient use of radio resources by allowing many data users to share the same interface on a statistical basis. •The main benefits of GPRS are that it reserves ra ...
... • Transactions such as Credit Card checks and a variety of telemetric applications benefit from the fast session set-ups. • GPRS enables efficient use of radio resources by allowing many data users to share the same interface on a statistical basis. •The main benefits of GPRS are that it reserves ra ...
A Simple Metric for Ad Hoc Network Adaptation
... placed on all nodes in a resource-constrained network. Coordination of multiple services of the same type would involve complicating communication among the services and is a future extension of this work. Clients utilize a QoS metric that is both suitable and consistent with respect to the service. ...
... placed on all nodes in a resource-constrained network. Coordination of multiple services of the same type would involve complicating communication among the services and is a future extension of this work. Clients utilize a QoS metric that is both suitable and consistent with respect to the service. ...
SEMESTER_2_Chapter_4KEY
... Hop count is used as the metric for path selection. If the hop count for a network is greater than 15, RIP cannot supply a route to that network. Routing updates are broadcast or multicast every 30 seconds, by default. Bandwidth, delay, load and reliability are used to create a composite metric. Rou ...
... Hop count is used as the metric for path selection. If the hop count for a network is greater than 15, RIP cannot supply a route to that network. Routing updates are broadcast or multicast every 30 seconds, by default. Bandwidth, delay, load and reliability are used to create a composite metric. Rou ...
for TCP
... line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash. ...
... line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash. ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... The goal of this paper is to investigate the behaviour of routing convergence. It begins with an explanation of IP addressing. The paper discusses the two routing protocols: Routing Information Protocol (RIP) and Enhanced Interior Gateway Routing Protocol (EIGRP) into great detail. The paper then ex ...
... The goal of this paper is to investigate the behaviour of routing convergence. It begins with an explanation of IP addressing. The paper discusses the two routing protocols: Routing Information Protocol (RIP) and Enhanced Interior Gateway Routing Protocol (EIGRP) into great detail. The paper then ex ...
Remote Access VPN IPsec
... TheGreenBow IPsec VPN Client will probably have a dynamically assign IP address and may or may not be behind a Network Address Translation (NAT) device. As such we must assume that we need NAT traversal and TheGreenBow will be the initiator. In this example the MRD-330 has a 3G subscription that pro ...
... TheGreenBow IPsec VPN Client will probably have a dynamically assign IP address and may or may not be behind a Network Address Translation (NAT) device. As such we must assume that we need NAT traversal and TheGreenBow will be the initiator. In this example the MRD-330 has a 3G subscription that pro ...
Wireless Overview Protocols and Threat Models
... message can be received. If it does not match, the message is discarded.” ...
... message can be received. If it does not match, the message is discarded.” ...
ping - SLAC
... agreement, and verifying it is being met • Choosing routes when more than one is available • Setting expectations: – Deciding which links need upgrading – Deciding where to place collaboration components such as a regional computing center, software development – How well will an application work (e ...
... agreement, and verifying it is being met • Choosing routes when more than one is available • Setting expectations: – Deciding which links need upgrading – Deciding where to place collaboration components such as a regional computing center, software development – How well will an application work (e ...
1 Mapping the Internet Topology Traceroute A Basic Tool for
... • Data is obtained from DIMES – Community-based infrastructure, using almost 1000 active measuringg software agents g – Agents follow a script and perform ~2 probes per minute (ICMP/UDP traceroute, ping) – Most agents measure from a single AS (vp) ...
... • Data is obtained from DIMES – Community-based infrastructure, using almost 1000 active measuringg software agents g – Agents follow a script and perform ~2 probes per minute (ICMP/UDP traceroute, ping) – Most agents measure from a single AS (vp) ...
a simple yet effective method to prune dense layers
... Using large and oversized networks in these tasks is a common practice. Such oversized networks can easily overfit on the training dataset while having poor generalization on the testing data (Sabo & Yu (2008)). A rule of thumb for obtaining useful generalization is to use the smallest number of par ...
... Using large and oversized networks in these tasks is a common practice. Such oversized networks can easily overfit on the training dataset while having poor generalization on the testing data (Sabo & Yu (2008)). A rule of thumb for obtaining useful generalization is to use the smallest number of par ...
Addressing the Network IPv4 - Chapter 6
... There are many subnet calculators, but you will not be able to use them in exams. Start with the biggest subnet and work down to the smallest. Make sure the subnets are valid sizes with ...
... There are many subnet calculators, but you will not be able to use them in exams. Start with the biggest subnet and work down to the smallest. Make sure the subnets are valid sizes with ...
How many ways to 0wn the Internet? Towards Viable Worm
... • Automatic responses are critical to stop worms – Sapphire could not be slowed by human response – See “How to 0wn ...” and Moore et al, “Internet Quarantine” ...
... • Automatic responses are critical to stop worms – Sapphire could not be slowed by human response – See “How to 0wn ...” and Moore et al, “Internet Quarantine” ...
Canon WFT-E1 (A) Wireless File Transmitter Network Support Guide
... stages 1 & 2 within the Wireless Network Properties and Filezilla FTP server. The target server address should be should match the address of the PC’s wireless transmitter (dongle) in this case it is 192.168.0.10. The port number should match the port number we opened in the FTP server, in this case ...
... stages 1 & 2 within the Wireless Network Properties and Filezilla FTP server. The target server address should be should match the address of the PC’s wireless transmitter (dongle) in this case it is 192.168.0.10. The port number should match the port number we opened in the FTP server, in this case ...
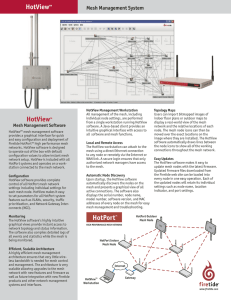
HotViewTM HotView™
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
01101044
... for guiding and helping to make this thesis report. This thesis gives us the chance of visiting different government and nongovernmental organizations and working with real life, which helped us to acquire clear insight about the real life systems. It was a thoroughly enjoyable experience. ...
... for guiding and helping to make this thesis report. This thesis gives us the chance of visiting different government and nongovernmental organizations and working with real life, which helped us to acquire clear insight about the real life systems. It was a thoroughly enjoyable experience. ...
Firewall and Proxy Server
... firewall rules allow it. As packets arrive they are filtered by their type, source address, destination address, and port information contained in each packet Many network routers have the ability to perform some firewall services. Filtering firewalls can be thought of as a type of router ...
... firewall rules allow it. As packets arrive they are filtered by their type, source address, destination address, and port information contained in each packet Many network routers have the ability to perform some firewall services. Filtering firewalls can be thought of as a type of router ...
Important Questions for (CS) Board Examination-2016-17
... 2 (d) “Bhartiya Connectivity Association” is planning to spread their offices in four major cities in India to provide regional IT infrastructure support in the field of Education & Culture. The company has planned to setup their head office in New Delhi in three locations and have named their New D ...
... 2 (d) “Bhartiya Connectivity Association” is planning to spread their offices in four major cities in India to provide regional IT infrastructure support in the field of Education & Culture. The company has planned to setup their head office in New Delhi in three locations and have named their New D ...
manual de fabricante del cablerouter Technicolor TC7210
... Support Web pages and private DHCP server for status monitoring. ...
... Support Web pages and private DHCP server for status monitoring. ...
Design Philosophy
... site hosting the rack, InstaGENI will also provide Network Address Translation (NAT) so that outgoing traffic can reach the public Internet. Both the control node and the experiment nodes will have separately-routed iLO cards for node control. It is strongly recommended that the control node iLO car ...
... site hosting the rack, InstaGENI will also provide Network Address Translation (NAT) so that outgoing traffic can reach the public Internet. Both the control node and the experiment nodes will have separately-routed iLO cards for node control. It is strongly recommended that the control node iLO car ...