Security management
... • system or data that if compromised would cause a moderate disruption in the business or minor legal or financial ramification, provide further access to other system • The targeted system or data requires a moderate effort to restore • The restoration process is disruptive to the system ...
... • system or data that if compromised would cause a moderate disruption in the business or minor legal or financial ramification, provide further access to other system • The targeted system or data requires a moderate effort to restore • The restoration process is disruptive to the system ...
TELIA YHTEYS KOTIIN MOBIILI SERVICE DESCRIPTION
... The traffic management methods include, for example, restriction of network usage based on court order in order to block access to network services used for unauthorised distribution of content protected by copyright. Such restrictions may be implemented in such a manner that the user’s access to ne ...
... The traffic management methods include, for example, restriction of network usage based on court order in order to block access to network services used for unauthorised distribution of content protected by copyright. Such restrictions may be implemented in such a manner that the user’s access to ne ...
Top Ten Database Threats
... their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus yo ...
... their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus yo ...
Protocols used by the virtual private network.
... Internet Protocol Security (IPsec). The main protocol for VPNs is called Internet Protocol Security (IPsec). It isn't actually a protocol in itself. Instead, it is an entire set of protocols. IPsec works at Layer 3 of the OSI model or above. It is the most common suite of protocols used to secure a ...
... Internet Protocol Security (IPsec). The main protocol for VPNs is called Internet Protocol Security (IPsec). It isn't actually a protocol in itself. Instead, it is an entire set of protocols. IPsec works at Layer 3 of the OSI model or above. It is the most common suite of protocols used to secure a ...
Best Practices for Victim Response and Reporting of Cyber Incidents
... designed to verify that necessary lines of communication exist, that decision-making roles and responsibilities are well understood, and that any technology that may be needed during an actual incident is available and likely to be effective. Deficiencies and gaps identified during an exercise shoul ...
... designed to verify that necessary lines of communication exist, that decision-making roles and responsibilities are well understood, and that any technology that may be needed during an actual incident is available and likely to be effective. Deficiencies and gaps identified during an exercise shoul ...
guidance - Public Intelligence
... designed to verify that necessary lines of communication exist, that decision-making roles and responsibilities are well understood, and that any technology that may be needed during an actual incident is available and likely to be effective. Deficiencies and gaps identified during an exercise shoul ...
... designed to verify that necessary lines of communication exist, that decision-making roles and responsibilities are well understood, and that any technology that may be needed during an actual incident is available and likely to be effective. Deficiencies and gaps identified during an exercise shoul ...
Chapter 19: Malicious Logic - Welcome to nob.cs.ucdavis.edu!
... • Observation: users with execute permission usually have read permission, too – So files with “execute” permission have type “executable”; those without it, type “data” – Executable files can be altered, but type immediately changed to “data” • Implemented by turning off execute permission • Certif ...
... • Observation: users with execute permission usually have read permission, too – So files with “execute” permission have type “executable”; those without it, type “data” – Executable files can be altered, but type immediately changed to “data” • Implemented by turning off execute permission • Certif ...
No Slide Title
... Statement of authority and scope - Defines who in the organization sponsors the security policy, who is responsible for implementing it, and what areas are covered by the policy. Acceptable use policy (AUP) - Defines the acceptable use of equipment and computing services, and the appropriate employe ...
... Statement of authority and scope - Defines who in the organization sponsors the security policy, who is responsible for implementing it, and what areas are covered by the policy. Acceptable use policy (AUP) - Defines the acceptable use of equipment and computing services, and the appropriate employe ...
PP_ch23f
... – Some servers have critical data (Active Directory) – Back up System State to include • Most of Registry, security settings, and more ...
... – Some servers have critical data (Active Directory) – Back up System State to include • Most of Registry, security settings, and more ...
Security - Computer Science Department
... • What threats am I trying to address? • How effective will a given countermeasure be? • What is the trade-off between security, cost, and usability? ...
... • What threats am I trying to address? • How effective will a given countermeasure be? • What is the trade-off between security, cost, and usability? ...
Authentication and Remote Access
... L2TP • Designed for use across all kinds of networks, including ATM and Frame Relay • Can be implemented by both hardware and software • Designed to work with established AAA services such as RADIUS and TACACS+ ...
... L2TP • Designed for use across all kinds of networks, including ATM and Frame Relay • Can be implemented by both hardware and software • Designed to work with established AAA services such as RADIUS and TACACS+ ...
Bots and Botnets - IT Services Technical Notes
... folder, sets hidden, system and read-only attributes for itself and then creates the following startup keys in the Registry… The backdoor monitors Registry changes and re-creates these keys if they are deleted or modified. ...
... folder, sets hidden, system and read-only attributes for itself and then creates the following startup keys in the Registry… The backdoor monitors Registry changes and re-creates these keys if they are deleted or modified. ...
ATLAS® Intelligence Feed
... Each product within the Arbor Networks’ portfolio is designed to address a different problem or audience. However, all of the products can consume the ATLAS Intelligence Feed—though they analyze the information differently. Some of the products analyze NetFlow and some of the products look at networ ...
... Each product within the Arbor Networks’ portfolio is designed to address a different problem or audience. However, all of the products can consume the ATLAS Intelligence Feed—though they analyze the information differently. Some of the products analyze NetFlow and some of the products look at networ ...
Ingen bildrubrik
... with a PIN-on-Card Strong authentication allows secure system administration, even over the Internet. Events and alarms can be received as SMS Events can be monitored with SNMP without affecting system security ...
... with a PIN-on-Card Strong authentication allows secure system administration, even over the Internet. Events and alarms can be received as SMS Events can be monitored with SNMP without affecting system security ...
3_firewall_m
... Mode or IP Masquerade) • Wherein a large group of internal clients share a single or small group of internal IP addresses for the purpose of hiding their identities or expanding the internal network address space. – Static Translation (also called Port Forwarding) • Wherein a specific internal netwo ...
... Mode or IP Masquerade) • Wherein a large group of internal clients share a single or small group of internal IP addresses for the purpose of hiding their identities or expanding the internal network address space. – Static Translation (also called Port Forwarding) • Wherein a specific internal netwo ...
Threat Awareness and Defense Sec Briefing 51.00
... business information is aggressively targeted. The industries listed above are of strategic interest to the United States because they contribute so greatly to leading-edge, critical technologies. A 1995 report by the National Counterintelligence Center adds that foreign collectors have also exhibit ...
... business information is aggressively targeted. The industries listed above are of strategic interest to the United States because they contribute so greatly to leading-edge, critical technologies. A 1995 report by the National Counterintelligence Center adds that foreign collectors have also exhibit ...
ALTA Assessment Procedures
... a. For the sample of employees tested in Assessment Procedure 3.02 above, test the user access provisioning process to determine if access is approved in accordance with policy prior to granting. o Obtain evidence (invoice/documentation in personnel files, etc.) that 5 year Background Checks were co ...
... a. For the sample of employees tested in Assessment Procedure 3.02 above, test the user access provisioning process to determine if access is approved in accordance with policy prior to granting. o Obtain evidence (invoice/documentation in personnel files, etc.) that 5 year Background Checks were co ...
13:40 A multi-layered approach for today`s
... © 2016 AT&T Intellectual Property. All rights reserved. AT&T, Globe logo, Mobilizing Your World and DIRECTV are registered trademarks and service marks of AT&T Intellectual Property and/or AT&T affiliated companies. All other marks are the property of their respective owners. AT&T Proprietary (Inter ...
... © 2016 AT&T Intellectual Property. All rights reserved. AT&T, Globe logo, Mobilizing Your World and DIRECTV are registered trademarks and service marks of AT&T Intellectual Property and/or AT&T affiliated companies. All other marks are the property of their respective owners. AT&T Proprietary (Inter ...
Application level gateway Firewalls - Mercer University
... for different applications. Both the client and the server connect to these proxies instead of connecting directly to each other. So, any suspicious data or connections are dropped by these proxies. Application level firewalls can look in to individual sessions and decide to drop a packet based on ...
... for different applications. Both the client and the server connect to these proxies instead of connecting directly to each other. So, any suspicious data or connections are dropped by these proxies. Application level firewalls can look in to individual sessions and decide to drop a packet based on ...
Applying the OSI model
... When a client needs a service, it queries the SAP database, which provides the IPX address Users don’t need to know the IPX addresses of other servers & workstations NCP (Netware Core Protocol) Handles requests for services, like printing and file access, between clients & servers Acts as a ...
... When a client needs a service, it queries the SAP database, which provides the IPX address Users don’t need to know the IPX addresses of other servers & workstations NCP (Netware Core Protocol) Handles requests for services, like printing and file access, between clients & servers Acts as a ...
Web Security Security+ Guide to Network Security Fundamentals
... information each time they visits that site, the Web server stores that information in a file on the local computer • Attackers often target cookies because they can contain sensitive information (usernames and other private information) Security+ Guide to Network Security Fundamentals, 2e ...
... information each time they visits that site, the Web server stores that information in a file on the local computer • Attackers often target cookies because they can contain sensitive information (usernames and other private information) Security+ Guide to Network Security Fundamentals, 2e ...
Effective Database Security Database Top 10 Threats
... – Specific mechanisms for specific vulnerabilities – Resource control mechanisms • Timing responses • Sizing responses • Connection control ...
... – Specific mechanisms for specific vulnerabilities – Resource control mechanisms • Timing responses • Sizing responses • Connection control ...
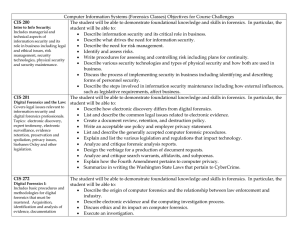
Computer Information Systems (Forensics Classes) Objectives for
... • Describe security technologies used for establishing identity and how security technologies are implemented in corporate networks. • Identify strengths and weaknesses associated with protocols designed to authenticate users. • Describe the technologies that exist at the different TCP/IP layers, in ...
... • Describe security technologies used for establishing identity and how security technologies are implemented in corporate networks. • Identify strengths and weaknesses associated with protocols designed to authenticate users. • Describe the technologies that exist at the different TCP/IP layers, in ...
Generic Template
... preventing legitimate network traffic Attempts to disrupt connections between users and web sites, thereby preventing access to a service Attempts to prevent access to critical infrastructure such as DNS or service provider routers ...
... preventing legitimate network traffic Attempts to disrupt connections between users and web sites, thereby preventing access to a service Attempts to prevent access to critical infrastructure such as DNS or service provider routers ...
KaranOberoi
... Sub-Domain must be added to RootDomain – otherwise there will be no tree adiscon.com ...
... Sub-Domain must be added to RootDomain – otherwise there will be no tree adiscon.com ...