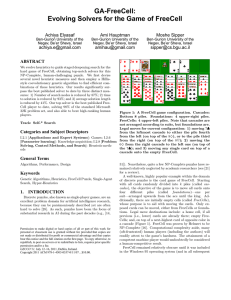
Kernel Estimation and Model Combination in A Bandit Problem with
... For example, before deciding which treatment arm to be assigned to a patient, we can observe the patient prognostic factors such as age, blood pressure or genetic information, and then use such information for adaptive treatment assignment for best outcome. It is worth noting that the consideration ...
... For example, before deciding which treatment arm to be assigned to a patient, we can observe the patient prognostic factors such as age, blood pressure or genetic information, and then use such information for adaptive treatment assignment for best outcome. It is worth noting that the consideration ...
A measure of the local connectivity between graph vertices
... positive definite, a case commonly discussed in numerical linear algebra literature, and, thus, the analysis is nontrivial. With a concurrent scaling of all the vertex values, the algebraic distance between two vertices i and j converges to the absolute difference between the ith and the jth entry o ...
... positive definite, a case commonly discussed in numerical linear algebra literature, and, thus, the analysis is nontrivial. With a concurrent scaling of all the vertex values, the algebraic distance between two vertices i and j converges to the absolute difference between the ith and the jth entry o ...
chapter 1 test bank questions - Department of Computer Science
... 1. Let century_digits be equal to the first two digits of the year. 2. Let year_digits be equal to the last two digits of the year. 3. Let value be equal to year_digits + floor(year_digits / 4) 4. If century_digits equals 18, then add 2 to value, else if century_digits equals 20, then add 6 to value ...
... 1. Let century_digits be equal to the first two digits of the year. 2. Let year_digits be equal to the last two digits of the year. 3. Let value be equal to year_digits + floor(year_digits / 4) 4. If century_digits equals 18, then add 2 to value, else if century_digits equals 20, then add 6 to value ...
Analysis of Algorithms
... These are bounds on running time, not for the problem! The thumbrules for getting the running time are! 1. Throw away all terms other than the most significant one -- Calculus may be needed ! e.g.: which is greater: n log n or n1.001 ?! 2. Throw away the constant factor.! 3. The expression is Θ() of ...
... These are bounds on running time, not for the problem! The thumbrules for getting the running time are! 1. Throw away all terms other than the most significant one -- Calculus may be needed ! e.g.: which is greater: n log n or n1.001 ?! 2. Throw away the constant factor.! 3. The expression is Θ() of ...
Cost-effective Outbreak Detection in Networks Jure Leskovec Andreas Krause Carlos Guestrin
... that, perhaps counterintuitively, a more cost-effective solution can be obtained, by reading smaller, but higher quality, blogs, which our algorithm can find. There are several possible criteria one may want to optimize in outbreak detection. For example, one criterion seeks to minimize detection time ...
... that, perhaps counterintuitively, a more cost-effective solution can be obtained, by reading smaller, but higher quality, blogs, which our algorithm can find. There are several possible criteria one may want to optimize in outbreak detection. For example, one criterion seeks to minimize detection time ...
Lecture Notes for Algorithm Analysis and Design
... and has fairly large constants that neutralize the advantage of the asymptotic improvement unless the numbers are a few thousand bits long. It is however conceivable that such methods will become more relevant as we may need to multiply large keys for cryptographic/security requirements. ...
... and has fairly large constants that neutralize the advantage of the asymptotic improvement unless the numbers are a few thousand bits long. It is however conceivable that such methods will become more relevant as we may need to multiply large keys for cryptographic/security requirements. ...
Global Consistency for Continuous Constraints
... provide relatively poor results when applied to continuous CSPs: they ensure neither completeness nor convergence in the general case (a good insight into the problems encountered can be found in [1]). However, Faltings [5] has shown that some undesirable features of propagation algorithms with inte ...
... provide relatively poor results when applied to continuous CSPs: they ensure neither completeness nor convergence in the general case (a good insight into the problems encountered can be found in [1]). However, Faltings [5] has shown that some undesirable features of propagation algorithms with inte ...
108_01_basics
... Able to tell what an algorithm is and have some understanding why we study algorithms ...
... Able to tell what an algorithm is and have some understanding why we study algorithms ...
Lab 7: Iterative Algorithms Using While Loops
... Part A: Cube Root There are many, many algorithms for computing the cube root of a number. We will use the Newton-Raphson algorithm. Like all iterative algorithms, this algorithm requires an initial estimate for the solution. The estimate is evaluated for accuracy and if the estimate isn’t accurate ...
... Part A: Cube Root There are many, many algorithms for computing the cube root of a number. We will use the Newton-Raphson algorithm. Like all iterative algorithms, this algorithm requires an initial estimate for the solution. The estimate is evaluated for accuracy and if the estimate isn’t accurate ...
Algorithm
In mathematics and computer science, an algorithm (/ˈælɡərɪðəm/ AL-gə-ri-dhəm) is a self-contained step-by-step set of operations to be performed. Algorithms exist that perform calculation, data processing, and automated reasoning.An algorithm is an effective method that can be expressed within a finite amount of space and time and in a well-defined formal language for calculating a function. Starting from an initial state and initial input (perhaps empty), the instructions describe a computation that, when executed, proceeds through a finite number of well-defined successive states, eventually producing ""output"" and terminating at a final ending state. The transition from one state to the next is not necessarily deterministic; some algorithms, known as randomized algorithms, incorporate random input.The concept of algorithm has existed for centuries, however a partial formalization of what would become the modern algorithm began with attempts to solve the Entscheidungsproblem (the ""decision problem"") posed by David Hilbert in 1928. Subsequent formalizations were framed as attempts to define ""effective calculability"" or ""effective method""; those formalizations included the Gödel–Herbrand–Kleene recursive functions of 1930, 1934 and 1935, Alonzo Church's lambda calculus of 1936, Emil Post's ""Formulation 1"" of 1936, and Alan Turing's Turing machines of 1936–7 and 1939. Giving a formal definition of algorithms, corresponding to the intuitive notion, remains a challenging problem.