Fitz and Dennis TB ch05 File
... a. which computer sent the TCP packet. b. which application layer program that the packet should be sent c. which application layer process the packet is from. d. the IP address of the source computer. e. the IP address of the destination computer. Answer: C Difficulty: Moderate Reference: p.146-147 ...
... a. which computer sent the TCP packet. b. which application layer program that the packet should be sent c. which application layer process the packet is from. d. the IP address of the source computer. e. the IP address of the destination computer. Answer: C Difficulty: Moderate Reference: p.146-147 ...
bgp header
... • Routers/hosts with default routes rely on other routers to complete the picture. • In general routing information should be: – Consistent, I.e., if packet is sent off in one direction then another direction should not be more optimal – Complete, I.e., should be able to reach all destinations ...
... • Routers/hosts with default routes rely on other routers to complete the picture. • In general routing information should be: – Consistent, I.e., if packet is sent off in one direction then another direction should not be more optimal – Complete, I.e., should be able to reach all destinations ...
Evaluating OSPF
... Connected subnets and Others Link-state advertisements are flooded to all routers when areas are not configured: Issue : LSA flooding -> hampers performance Link-state database is used for storing network topology information Dijkstra’a SPF (Shortest path first) algorithm used to compute shortest ...
... Connected subnets and Others Link-state advertisements are flooded to all routers when areas are not configured: Issue : LSA flooding -> hampers performance Link-state database is used for storing network topology information Dijkstra’a SPF (Shortest path first) algorithm used to compute shortest ...
IPNetworkingUNIT7 - Rhema Impact Ministries
... advertise not only the subnet number but also the subnet mask when advertising routes. • A routing protocol must include subnet masks in its routing updates to support manual route summarization. • Each IP routing protocol is considered to be either classless or classful , based on whether the routi ...
... advertise not only the subnet number but also the subnet mask when advertising routes. • A routing protocol must include subnet masks in its routing updates to support manual route summarization. • Each IP routing protocol is considered to be either classless or classful , based on whether the routi ...
seminar report - School of Information Technology, IIT kharagpur
... The calling party initiates his call in the same way as in a conventional telecommunication network. The first phase of the call is set-up on that network, however, immediately after this the boxes exchange the information required for the second phase. Data they have exchanged and the pre-establish ...
... The calling party initiates his call in the same way as in a conventional telecommunication network. The first phase of the call is set-up on that network, however, immediately after this the boxes exchange the information required for the second phase. Data they have exchanged and the pre-establish ...
7.4 Node-Level Simulators
... from thread-unsafe components. TinyGALS is such a language for TinyOS. One of the key factors that affects component reusability in embedded software is the component composability, especially concurrent composability. In general, when developing a component, a programmer may not anticipate all poss ...
... from thread-unsafe components. TinyGALS is such a language for TinyOS. One of the key factors that affects component reusability in embedded software is the component composability, especially concurrent composability. In general, when developing a component, a programmer may not anticipate all poss ...
6781_MPLS_Lecture2 - Computer Science and Engineering
... • Specifies how frequently the committed rate should be given to CRLSP ...
... • Specifies how frequently the committed rate should be given to CRLSP ...
Network Layer and Data Center Topologies
... aside: graph abstraction is useful in other network contexts, e.g., P2P, where N is set of peers and E is set of TCP connections ...
... aside: graph abstraction is useful in other network contexts, e.g., P2P, where N is set of peers and E is set of TCP connections ...
pdf
... aside: graph abstraction is useful in other network contexts, e.g., P2P, where N is set of peers and E is set of TCP connections ...
... aside: graph abstraction is useful in other network contexts, e.g., P2P, where N is set of peers and E is set of TCP connections ...
CSE331-10
... Increase and Decrease • A value CongestionWindow is used to control the number of unacknowledged transmissions. • This value is increased linearly until timeouts for ACKs are missed. • When timeouts occur, CongestionWindow is decreased by half to reduce the pressure on the network quickly. • The st ...
... Increase and Decrease • A value CongestionWindow is used to control the number of unacknowledged transmissions. • This value is increased linearly until timeouts for ACKs are missed. • When timeouts occur, CongestionWindow is decreased by half to reduce the pressure on the network quickly. • The st ...
Network Architecture Design for Wireless Sensor Nodes
... network and maintaining connectivity in a decentralized manner by forming an ad hoc network. Such WSNs could change their topology dynamically when connectivity among the nodes varies with time due to node mobility. But current, real-world deployment usually consists of stationary sensor nodes. WSNs ...
... network and maintaining connectivity in a decentralized manner by forming an ad hoc network. Such WSNs could change their topology dynamically when connectivity among the nodes varies with time due to node mobility. But current, real-world deployment usually consists of stationary sensor nodes. WSNs ...
PROTOCOLS COMPARISON IN AD HOC NETWORKS
... one could turn on 15 laptop computers, each with the same kind of infrared data communications adapter, and hope that they could form a network among themselves [1]. This feature is also useful even if the laptops were stationary. In ad hoc networks, most of the discussion focuses on the following a ...
... one could turn on 15 laptop computers, each with the same kind of infrared data communications adapter, and hope that they could form a network among themselves [1]. This feature is also useful even if the laptops were stationary. In ad hoc networks, most of the discussion focuses on the following a ...
InfiniBand - FSU Computer Science
... • Up/Down routing does not work directly – Need information about the incoming interface and the destination and Infiniband only uses destination – Potential solution: » find all possible paths » remove all possible down link following up links in each node » find one output port for each destinatio ...
... • Up/Down routing does not work directly – Need information about the incoming interface and the destination and Infiniband only uses destination – Potential solution: » find all possible paths » remove all possible down link following up links in each node » find one output port for each destinatio ...
Constrained Optical Multicast Routing
... Knowledge of the physical topology – more efficient multicast routing is possible Light splitting is more efficient than copying packets Avoid the electronic processing bottleneck Support of coding format and bit-rate transparency across both unicast and multicast ...
... Knowledge of the physical topology – more efficient multicast routing is possible Light splitting is more efficient than copying packets Avoid the electronic processing bottleneck Support of coding format and bit-rate transparency across both unicast and multicast ...
network
... phase it requires that a virtual connection from the source host to the destination host is set up before any data is sent Typically wait full RTT (Round Trip Time) for connection setup before sending first data packet ...
... phase it requires that a virtual connection from the source host to the destination host is set up before any data is sent Typically wait full RTT (Round Trip Time) for connection setup before sending first data packet ...
Session_14
... and maintain an ad hoc network. • AODV allows mobile nodes to obtain routes quickly for new destinations, and does not require nodes to maintain routes to destinations that are not in active communication. • AODV allows mobile nodes to respond to link breakages and changes in network topology in a t ...
... and maintain an ad hoc network. • AODV allows mobile nodes to obtain routes quickly for new destinations, and does not require nodes to maintain routes to destinations that are not in active communication. • AODV allows mobile nodes to respond to link breakages and changes in network topology in a t ...
CCNA 1 Module 11 TCP/IP Transport and Application Layers
... not been manually configured with a default gateway, it can learn of available routers through the process of router discovery. • This process begins with the host sending a router solicitation message to all routers, using the multicast address 224.0.0.2 as the destination address or using broadcas ...
... not been manually configured with a default gateway, it can learn of available routers through the process of router discovery. • This process begins with the host sending a router solicitation message to all routers, using the multicast address 224.0.0.2 as the destination address or using broadcas ...
P2P_Computing
... Then sends a PING message to discover other nodes PONG message are sent in reply from hosts offering connections with the new node Direct connection are then made ...
... Then sends a PING message to discover other nodes PONG message are sent in reply from hosts offering connections with the new node Direct connection are then made ...
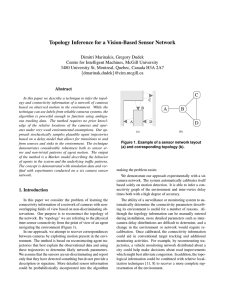
Topology Inference for a Vision-Based Sensor Network
... Motion in the environment can be exploited to calibrate a network of cameras. Most efforts using this technique have focused on sensor self-localization. Stein [13], for example, considered recovering a rough planar alignment of the location and orientation of the individual cameras. Using a least-m ...
... Motion in the environment can be exploited to calibrate a network of cameras. Most efforts using this technique have focused on sensor self-localization. Stein [13], for example, considered recovering a rough planar alignment of the location and orientation of the individual cameras. Using a least-m ...
CloudTrax Network Planning Guide
... While any network should be able to handle a high number of users simply browsing the web, just a few users sharing files or streaming video can quickly use up all available bandwidth. CloudTrax helps to manage this by setting per-user download and upload limits, as well as providing the ability to ...
... While any network should be able to handle a high number of users simply browsing the web, just a few users sharing files or streaming video can quickly use up all available bandwidth. CloudTrax helps to manage this by setting per-user download and upload limits, as well as providing the ability to ...
Submitted version - QMRO Home
... Equations (1) to (5) are quoted from [14] which utilize the GPS information of each node in the MANET. After introducing LET into route selection algorithm, the ad hoc network can proactively avoid selecting routes that may experience potential link breaks during the call lifetime. In the simulation ...
... Equations (1) to (5) are quoted from [14] which utilize the GPS information of each node in the MANET. After introducing LET into route selection algorithm, the ad hoc network can proactively avoid selecting routes that may experience potential link breaks during the call lifetime. In the simulation ...