CPSC 155a Lecture 3
... IP address, written down in a “dot notation” for “ease” of reading, such as 128.36.229.231 • IP addresses are the universal IDs that are used to name everything • For convenience, each host also has a human-friendly host name. For example, ...
... IP address, written down in a “dot notation” for “ease” of reading, such as 128.36.229.231 • IP addresses are the universal IDs that are used to name everything • For convenience, each host also has a human-friendly host name. For example, ...
Document
... technology to disseminate computational tasks over multiple clients; peers do not have a direct connection to one another. ...
... technology to disseminate computational tasks over multiple clients; peers do not have a direct connection to one another. ...
networks
... • A network allows users to communicate via electronic mail (email) and to send files as attachments. • Users in a network may also teleconference or video conference. ...
... • A network allows users to communicate via electronic mail (email) and to send files as attachments. • Users in a network may also teleconference or video conference. ...
P2P Networks
... Allow a group of computer users (employing the same networking software) to connect with each other to share resources. ...
... Allow a group of computer users (employing the same networking software) to connect with each other to share resources. ...
Plum
... • A network allows users to communicate via electronic mail (email) and to send files as attachments. • Users in a network may also teleconference or video conference. ...
... • A network allows users to communicate via electronic mail (email) and to send files as attachments. • Users in a network may also teleconference or video conference. ...
CPSC 155a Lecture 3
... Efficient sharing of machine resources Sharing of data Parallel computing Human communication ...
... Efficient sharing of machine resources Sharing of data Parallel computing Human communication ...
Tracker
... Peer A selects a subset (following the tit-for-tat and randomization rules) and establishes connections with these five peers. Peer A downloads chunks from peers in peer set and provides them with its own chunks (possible to parallel) ...
... Peer A selects a subset (following the tit-for-tat and randomization rules) and establishes connections with these five peers. Peer A downloads chunks from peers in peer set and provides them with its own chunks (possible to parallel) ...
ITGS
... heavily on a server not only to store files and applications, but run software on a client’s behalf (sometimes including even the OS) – The thin client merely acts as a terminal for accepting input and displaying output • The client only contains enough software to initialize the hardware and networ ...
... heavily on a server not only to store files and applications, but run software on a client’s behalf (sometimes including even the OS) – The thin client merely acts as a terminal for accepting input and displaying output • The client only contains enough software to initialize the hardware and networ ...
Slides
... P2P Definition Distributed systems consisting of interconnected nodes able to self-organize into network topologies with the purpose of sharing resources such as content, CPU cycles, storage and bandwidth, capable of adapting to failures and accommodating transient populations of nodes while mainta ...
... P2P Definition Distributed systems consisting of interconnected nodes able to self-organize into network topologies with the purpose of sharing resources such as content, CPU cycles, storage and bandwidth, capable of adapting to failures and accommodating transient populations of nodes while mainta ...
44_ExploringNetworkProperties
... Define client and protocol and explain the purpose of each. Explain the purpose of the NetBEUI, IPX/SPX, and TCP/IP protocols. Change the client, services, and protocol of a local area network connection in a Windows XP Pro computer. ...
... Define client and protocol and explain the purpose of each. Explain the purpose of the NetBEUI, IPX/SPX, and TCP/IP protocols. Change the client, services, and protocol of a local area network connection in a Windows XP Pro computer. ...
Network - Missouri State University
... between computers while managing security • Packet-switching - dividing a message on a source computer into a number of efficiently sized units called ________, each of which contains the address of the destination computer • Router - an __________ connecting device that examines each packet of data ...
... between computers while managing security • Packet-switching - dividing a message on a source computer into a number of efficiently sized units called ________, each of which contains the address of the destination computer • Router - an __________ connecting device that examines each packet of data ...
DecentralizedP2P - Department of Computer Science
... Query containing keywords is sent out over a TCP connection from ON to its SN For each match the SN returns the IP address and metadata of the matching node SNs will maintain a TCP connection between SNs creating an overlay network Query is sent to one or more of the directly connected nodes between ...
... Query containing keywords is sent out over a TCP connection from ON to its SN For each match the SN returns the IP address and metadata of the matching node SNs will maintain a TCP connection between SNs creating an overlay network Query is sent to one or more of the directly connected nodes between ...
Chapter 3 slides
... together by circuits. ◦ Broadcast: Everything is transmitted to every node. ◦ Circuit switching: local exchange was connected by an automatic switch at the exchange to the pair of wires connected to the other party’s. (Phone) ◦ Packet switching: brought processing and storage. construct a different ...
... together by circuits. ◦ Broadcast: Everything is transmitted to every node. ◦ Circuit switching: local exchange was connected by an automatic switch at the exchange to the pair of wires connected to the other party’s. (Phone) ◦ Packet switching: brought processing and storage. construct a different ...
Mobile ICN Applications for an Event with Large Crowds
... This section describes the user applications that are available on the Android devices in the demo to access the NetInf network. Photo Publish and Visual Content Directory The application shown in Figure 1b) is specially designed for a stadium-based event. It allows users to publish locally generate ...
... This section describes the user applications that are available on the Android devices in the demo to access the NetInf network. Photo Publish and Visual Content Directory The application shown in Figure 1b) is specially designed for a stadium-based event. It allows users to publish locally generate ...
PowerPoint format - Computer Science
... • Top three layers are not well-defined, all have to do with application level abstractions such as transformation of different data formats ...
... • Top three layers are not well-defined, all have to do with application level abstractions such as transformation of different data formats ...
computer networks
... • Nodes that gather information they sense. • Can be part of cars or phones, etc.. Or may be small separate devices. • Example: car gather data: location, speed, vibration, and fuel efficiency and upload this information to a database. • Those data can help find potholes, plan trips around congested ...
... • Nodes that gather information they sense. • Can be part of cars or phones, etc.. Or may be small separate devices. • Example: car gather data: location, speed, vibration, and fuel efficiency and upload this information to a database. • Those data can help find potholes, plan trips around congested ...
Here is the Power Point Presentation on Chord
... The node stores the previous node in the ring, it’s predecessor The node stores values for the distributed hash table ...
... The node stores the previous node in the ring, it’s predecessor The node stores values for the distributed hash table ...
Intrusion Detection Mechanisms for Peer-to
... Dr. Chittaranjan Hota (BITS – Pilani, Hyderabad) Dr. V.N. Venkatakrishnan (University of Illinois at Chicago) Dr. Nasir Memon (New York University, Abu Dhabi) ...
... Dr. Chittaranjan Hota (BITS – Pilani, Hyderabad) Dr. V.N. Venkatakrishnan (University of Illinois at Chicago) Dr. Nasir Memon (New York University, Abu Dhabi) ...
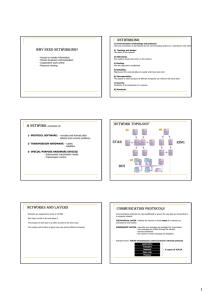
WHY NEED NETWORKING? NETWORKING NETWORK
... be grouped logically, without regard to physical location. ...
... be grouped logically, without regard to physical location. ...
Network Notes - w w w .conta.uom .gr
... • the processors are interconnected and communicate with each other • architecture is multiple computers distributed throughout the system interconnected through networks using communications lines ...
... • the processors are interconnected and communicate with each other • architecture is multiple computers distributed throughout the system interconnected through networks using communications lines ...
Java Developer
... peer-to-peer system is a dynamic environment which may consist of a very large number of nodes such as millions of nodes, which typically join and leave the system continuously. In the past few years, a number of P2P simulation software’s have been developed such as NeuroGrid, PeerSim, SeeraPis, and ...
... peer-to-peer system is a dynamic environment which may consist of a very large number of nodes such as millions of nodes, which typically join and leave the system continuously. In the past few years, a number of P2P simulation software’s have been developed such as NeuroGrid, PeerSim, SeeraPis, and ...
Peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or work loads between peers. Peers are equally privileged, equipotent participants in the application. They are said to form a peer-to-peer network of nodes.Peers make a portion of their resources, such as processing power, disk storage or network bandwidth, directly available to other network participants, without the need for central coordination by servers or stable hosts. Peers are both suppliers and consumers of resources, in contrast to the traditional client-server model in which the consumption and supply of resources is divided. Emerging collaborative P2P systems are going beyond the era of peers doing similar things while sharing resources, and are looking for diverse peers that can bring in unique resources and capabilities to a virtual community thereby empowering it to engage in greater tasks beyond those that can be accomplished by individual peers, yet that are beneficial to all the peers.While P2P systems had previously been used in many application domains, the architecture was popularized by the file sharing system Napster, originally released in 1999. The concept has inspired new structures and philosophies in many areas of human interaction. In such social contexts, peer-to-peer as a meme refers to the egalitarian social networking that has emerged throughout society, enabled by Internet technologies in general.