02history - Computer Science and Electrical Engineering
... • Based on FLOW-MATIC which had such features as: • Names up to 12 characters, with embedded hyphens • English names for arithmetic operators • Data and code were completely separate • Verbs were first word in every statement • CODASYL committee (Conference on Data Systems Languages) developed a pro ...
... • Based on FLOW-MATIC which had such features as: • Names up to 12 characters, with embedded hyphens • English names for arithmetic operators • Data and code were completely separate • Verbs were first word in every statement • CODASYL committee (Conference on Data Systems Languages) developed a pro ...
Design Patterns (a few) - Department of Computer Science
... undesirable dependences that prevent changing the implementation. ...
... undesirable dependences that prevent changing the implementation. ...
Machine language
... into the hardware of a particular computer • Initially, humans had no choice but to write programs in machine language because other programming languages had not yet been invented ...
... into the hardware of a particular computer • Initially, humans had no choice but to write programs in machine language because other programming languages had not yet been invented ...
Athipathy-Threads-in
... end and at any given time during the runtime of the thread, there is a single point of execution. However, a thread itself is not a program; it cannot run on its own. Rather, it runs within a program. ...
... end and at any given time during the runtime of the thread, there is a single point of execution. However, a thread itself is not a program; it cannot run on its own. Rather, it runs within a program. ...
l06Monads&Interp
... – Its amazing, but the number of different effects that compilers use is really small (on the order of 3-5). These are well studied and it is possible to build libraries of these monadic components, and to reuse them in many different compilers. ...
... – Its amazing, but the number of different effects that compilers use is really small (on the order of 3-5). These are well studied and it is possible to build libraries of these monadic components, and to reuse them in many different compilers. ...
mca_I_0506 - Madhya Pradesh Bhoj Open University
... b. Design a form to store array of integers and write code to search a particular number from array. Q.2a. Describe various elements of Visual Basics IDE. b. How is data control bounded with other control? Give name of properties for binding. Q.3a. What do you mean by Visual Basic Philosophy? b. How ...
... b. Design a form to store array of integers and write code to search a particular number from array. Q.2a. Describe various elements of Visual Basics IDE. b. How is data control bounded with other control? Give name of properties for binding. Q.3a. What do you mean by Visual Basic Philosophy? b. How ...
Chapter 15 Functional Programming
... Expressions are always evaluated in some context and can contain occurrences of the names found in that context. The Haskell evaluator uses the definitions associated with those names as rules for simplifying expressions. Chapter 15: Functional Programming ...
... Expressions are always evaluated in some context and can contain occurrences of the names found in that context. The Haskell evaluator uses the definitions associated with those names as rules for simplifying expressions. Chapter 15: Functional Programming ...
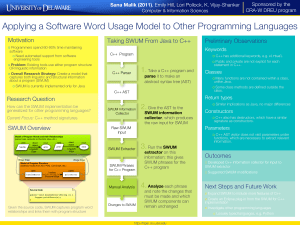
Research Question SWUM Overview Motivation Preliminary
... o C++ also has destructors, which have a similar signature as constructors. ...
... o C++ also has destructors, which have a similar signature as constructors. ...
Text
... You are now in a position to use your knowledge of inequalities from Unit 4 of the Algebra strand to illustrate linear programming with the following case study. Suppose a manufacturer of printed circuits has a stock of 200 resistors, 120 transistors and 150 capacitors and is required to produce two ...
... You are now in a position to use your knowledge of inequalities from Unit 4 of the Algebra strand to illustrate linear programming with the following case study. Suppose a manufacturer of printed circuits has a stock of 200 resistors, 120 transistors and 150 capacitors and is required to produce two ...
A Functional Approach to the Observer Pattern
... If we forget about the getSubject method, which is a common use of the pattern, we can give alternative implementations taking arrows [5] or applicative functors [4] as the effectful world. ...
... If we forget about the getSubject method, which is a common use of the pattern, we can give alternative implementations taking arrows [5] or applicative functors [4] as the effectful world. ...
CA320 - Computability & Complexity
... standard types belong to Ord except function types and some abstract types. Show Types belonging to this class can be displayed as strings. Again most Haskell standard types belong to Show except function types. Read Contains all the type that can be taken in as a string and converted into a type. A ...
... standard types belong to Ord except function types and some abstract types. Show Types belonging to this class can be displayed as strings. Again most Haskell standard types belong to Show except function types. Read Contains all the type that can be taken in as a string and converted into a type. A ...
Ppt - Computer Science and Electrical Engineering
... – Included some advanced data type features such as » Floating point, used twos complement and hidden bits ...
... – Included some advanced data type features such as » Floating point, used twos complement and hidden bits ...
Research on teaching of Java Exception Handling
... into teaching process, and simplify the complex ideas. Additionally how to make students understand Java language’s exception handling mechanism thoroughly, and even apply the main idea solving problems learned from Java lessons to many other ways in life. 3. methods of solving the problems 3. 1 Cla ...
... into teaching process, and simplify the complex ideas. Additionally how to make students understand Java language’s exception handling mechanism thoroughly, and even apply the main idea solving problems learned from Java lessons to many other ways in life. 3. methods of solving the problems 3. 1 Cla ...
Comparison of Erlang Runtime System and Java Virtual Machine
... ERTS works by executing an intermediate representation of erlang source code, also known as BEAM code. As mentioned there’s no specification for the generated instructions, though a few unofficial documents are available[2]. Quite unlike the Java programming language Erlang is a functional programmi ...
... ERTS works by executing an intermediate representation of erlang source code, also known as BEAM code. As mentioned there’s no specification for the generated instructions, though a few unofficial documents are available[2]. Quite unlike the Java programming language Erlang is a functional programmi ...
Chapter 6
... Unicode between 0 and FFFF in hexadecimal (65535 in decimal). To generate a random character is to generate a random integer between 0 and 65535 using the following expression: (note that since 0 <= Math.random() < 1.0, you have to add 1 to 65535.) (int)(Math.random() * (65535 + 1)) Liang, Introduct ...
... Unicode between 0 and FFFF in hexadecimal (65535 in decimal). To generate a random character is to generate a random integer between 0 and 65535 using the following expression: (note that since 0 <= Math.random() < 1.0, you have to add 1 to 65535.) (int)(Math.random() * (65535 + 1)) Liang, Introduct ...
Chapter 4 Methods
... Unicode between 0 and FFFF in hexadecimal (65535 in decimal). To generate a random character is to generate a random integer between 0 and 65535 using the following expression: (note that since 0 <= Math.random() < 1.0, you have to add 1 to 65535.) (int)(Math.random() * (65535 + 1)) Liang, Introduct ...
... Unicode between 0 and FFFF in hexadecimal (65535 in decimal). To generate a random character is to generate a random integer between 0 and 65535 using the following expression: (note that since 0 <= Math.random() < 1.0, you have to add 1 to 65535.) (int)(Math.random() * (65535 + 1)) Liang, Introduct ...
Pointers to Functions - CS
... Spend the time to find out What is wrong? Minimal settings that lead to the error? Reproduce the wrong behavior! Preferably on a small example ...
... Spend the time to find out What is wrong? Minimal settings that lead to the error? Reproduce the wrong behavior! Preferably on a small example ...
C Sharp (programming language)
C# (pronounced as see sharp) is a multi-paradigm programming language encompassing strong typing, imperative, declarative, functional, generic, object-oriented (class-based), and component-oriented programming disciplines. It was developed by Microsoft within its .NET initiative and later approved as a standard by Ecma (ECMA-334) and ISO (ISO/IEC 23270:2006). C# is one of the programming languages designed for the Common Language Infrastructure.C# is intended to be a simple, modern, general-purpose, object-oriented programming language. Its development team is led by Anders Hejlsberg. The most recent version is C# 6.0, which was released on July 20, 2015.