Microsoft`s Disk Operating System CS-550
... regardless of whether they need it or not. (Flynn, McHoes, 1996) Program files with an .EXE extension include a header which specifies the minimum and maximum memo ry required to run the program. If the maximum memory is available, DOS allocates it to the process. If the minimum is not available, th ...
... regardless of whether they need it or not. (Flynn, McHoes, 1996) Program files with an .EXE extension include a header which specifies the minimum and maximum memo ry required to run the program. If the maximum memory is available, DOS allocates it to the process. If the minimum is not available, th ...
Lecture 11
... spaces). The list structure may be contiguous or linked. The lists are stored starting in a fixed block within the partition (for uniform access at boot time), and may chain into other blocks. ...
... spaces). The list structure may be contiguous or linked. The lists are stored starting in a fixed block within the partition (for uniform access at boot time), and may chain into other blocks. ...
Computer components
... 3. With Windows, user commands are usually entered via a mouse click. How does the user enter a command on a table PC like the iPad or a smartphone like the iPhone? 4. When it is turned on, a computer executes a small bootstrap program that checks to see the hardware is working correctly and loads t ...
... 3. With Windows, user commands are usually entered via a mouse click. How does the user enter a command on a table PC like the iPad or a smartphone like the iPhone? 4. When it is turned on, a computer executes a small bootstrap program that checks to see the hardware is working correctly and loads t ...
Operating Systems and File Management Learning Steps LAP CC
... f) These utilities allow you to find, rename, copy, move, and delete files and folders. In addition they allow you to perform file management activities with more than one file at a time. The way that data is actually stored is referred to as the 7._______________________ storage model. g) Before a ...
... f) These utilities allow you to find, rename, copy, move, and delete files and folders. In addition they allow you to perform file management activities with more than one file at a time. The way that data is actually stored is referred to as the 7._______________________ storage model. g) Before a ...
Department of CSE
... 8. What is kernel? 9. Explain system call and system boot. 10. What is system programming? 11. What are the different services provided by an operating system? UNIT-II 12. What are the five activities of an OS with regards to file management? 13. What is the main advantage for an OS designer of usin ...
... 8. What is kernel? 9. Explain system call and system boot. 10. What is system programming? 11. What are the different services provided by an operating system? UNIT-II 12. What are the five activities of an OS with regards to file management? 13. What is the main advantage for an OS designer of usin ...
Master boot record
... Separation of the operating system (OS) and program files from user files. This allows image backups (or clones) to be made of only the operating system and installed software. Having a separate area for operating system virtual memory swapping/paging. Keeping frequently used programs and data near ...
... Separation of the operating system (OS) and program files from user files. This allows image backups (or clones) to be made of only the operating system and installed software. Having a separate area for operating system virtual memory swapping/paging. Keeping frequently used programs and data near ...
Operating System Structures
... Since main memory (primary storage) is volatile and too small to accommodate all data and programs permanently, the computer system must provide secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The o ...
... Since main memory (primary storage) is volatile and too small to accommodate all data and programs permanently, the computer system must provide secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The o ...
solutions - CIS @ UPenn
... con - more internal fragmentation, worse locality of reference smaller pages: pro - reduces internal fragmentation, better with locality ofreference con - bigger page table, more page faults, overhead in reading/writing of pages 3. Describe the three possible states of a process? Answer: Running: ac ...
... con - more internal fragmentation, worse locality of reference smaller pages: pro - reduces internal fragmentation, better with locality ofreference con - bigger page table, more page faults, overhead in reading/writing of pages 3. Describe the three possible states of a process? Answer: Running: ac ...
Sai Uday Kiran Ravi`s presentation on Application Security on
... from the operating system in that VM. Mechanism behind Overshadow: Controls memory mappings to present different views of memory pages depending on the execution context. When an application accesses its own memory, access ...
... from the operating system in that VM. Mechanism behind Overshadow: Controls memory mappings to present different views of memory pages depending on the execution context. When an application accesses its own memory, access ...
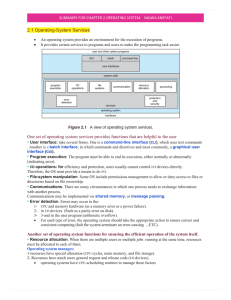
Summary for chapter 2 OPERATING SYSTEM nAJWA kNEFATI
... The functions that make up an API typically invoke the actual system calls . EX: Function CreateProcess () (create a new process) actually invokes the NTCreateProcess () system call in the Windows kernel. Why would an application programmer prefer programming according to an API rather than invoking ...
... The functions that make up an API typically invoke the actual system calls . EX: Function CreateProcess () (create a new process) actually invokes the NTCreateProcess () system call in the Windows kernel. Why would an application programmer prefer programming according to an API rather than invoking ...
Korea Univ Real-Time Systems
... Real-time property • Job should be done within a time limit Aerospace applications, Car control systems, Medical gadgets are critical in terms of time constraint – Otherwise, it could lead to catastrophe such as loss of life ...
... Real-time property • Job should be done within a time limit Aerospace applications, Car control systems, Medical gadgets are critical in terms of time constraint – Otherwise, it could lead to catastrophe such as loss of life ...
1. design principle
... pages in the computer’s memory. I/O Manager manages all input and output for the operating system, including cache manager, file system drivers, hardware device drivers, and network device drivers. Win32K window manager and GDI - Functions from Win32k.sys for graphics support and communication w ...
... pages in the computer’s memory. I/O Manager manages all input and output for the operating system, including cache manager, file system drivers, hardware device drivers, and network device drivers. Win32K window manager and GDI - Functions from Win32k.sys for graphics support and communication w ...
Introduction to Operating Systems
... Figure 2.2: Running Many Programs At Once Well, now things are getting a little more interesting. Even though we have only one processor, somehow all four of these programs seem to be running at the same time! How does this magic happen?4 It turns out that the operating system, with some help from t ...
... Figure 2.2: Running Many Programs At Once Well, now things are getting a little more interesting. Even though we have only one processor, somehow all four of these programs seem to be running at the same time! How does this magic happen?4 It turns out that the operating system, with some help from t ...
Run Standard Diagnostic Tests
... 1. Missing boot files — they may have been deleted by the user. 2. A virus has caused damage to the boot files or has corrupted the file system or Master Boot Record (MBR). 3. A common mistake is a floppy disk being left in the drive. 4. Cables not connected to hard disk drive properly. ...
... 1. Missing boot files — they may have been deleted by the user. 2. A virus has caused damage to the boot files or has corrupted the file system or Master Boot Record (MBR). 3. A common mistake is a floppy disk being left in the drive. 4. Cables not connected to hard disk drive properly. ...
Virtual Machine Monitors
... Virtualizing the User/Kernel Boundary Both the guest OS and applications run in (physical) user-mode This is necessary so that privileged instructions trap into the VMM ...
... Virtualizing the User/Kernel Boundary Both the guest OS and applications run in (physical) user-mode This is necessary so that privileged instructions trap into the VMM ...
System Software
... Microsoft was taken to court in the United States for anti-competitive conduct in making Internet Explorer 4.0 (and a non-standard JVM) non-removable parts of Windows 98 In 2004 the European Commission ruled that Microsoft broke EU competition law in tying Windows Media Player to its operating syste ...
... Microsoft was taken to court in the United States for anti-competitive conduct in making Internet Explorer 4.0 (and a non-standard JVM) non-removable parts of Windows 98 In 2004 the European Commission ruled that Microsoft broke EU competition law in tying Windows Media Player to its operating syste ...
Week 5 - Portland State University
... applications? Space sharing the memory among applications? Space sharing the disk among users? Time sharing access to the disk? Time sharing access to the network? Protection of applications from each other? Protection of user data from other users? Protection of hardware/devices? Pr ...
... applications? Space sharing the memory among applications? Space sharing the disk among users? Time sharing access to the disk? Time sharing access to the network? Protection of applications from each other? Protection of user data from other users? Protection of hardware/devices? Pr ...
I/O Management and Disk Scheduling (Chapter 10)
... bytes or characters or in large blocks. • Data representation: Different data-encoding schemes are used by different devices, includes differences in character code and parity conventions. • Error conditions: The nature of errors, the way in which they are reported, their consequences, and the avail ...
... bytes or characters or in large blocks. • Data representation: Different data-encoding schemes are used by different devices, includes differences in character code and parity conventions. • Error conditions: The nature of errors, the way in which they are reported, their consequences, and the avail ...
PPT - DC214
... Estimate unused pages: count in working set and keep a global count of estimate When memory starts to become scarce replace rather than add pages when fault occurs in working set with significant unused pages ...
... Estimate unused pages: count in working set and keep a global count of estimate When memory starts to become scarce replace rather than add pages when fault occurs in working set with significant unused pages ...
Chapter I Introduction
... Protecting users’ files • Key idea is to prevent users’ programs from directly accessing the disk • Will require I/O operations to be performed by the kernel • Make them privileged instructions that only the kernel can execute ...
... Protecting users’ files • Key idea is to prevent users’ programs from directly accessing the disk • Will require I/O operations to be performed by the kernel • Make them privileged instructions that only the kernel can execute ...
Modern Trends Used In Operating Systems For High Speed
... are translated to a physical page. When a process references an address from another logical page it is too fetched into the vacant memory space of physical page and become a part of these likely references. VM enables each process to behave as it has access to the complete memory space. To itself s ...
... are translated to a physical page. When a process references an address from another logical page it is too fetched into the vacant memory space of physical page and become a part of these likely references. VM enables each process to behave as it has access to the complete memory space. To itself s ...
Low-level formatting or physical formatting
... Among the partitions, one partition can hold a copy of the OS‘s executable code, while another holds user files. (b) The second step is logical formatting .The operating system stores the initial file-system data structures onto the disk. These data structures may include maps of free and allocated ...
... Among the partitions, one partition can hold a copy of the OS‘s executable code, while another holds user files. (b) The second step is logical formatting .The operating system stores the initial file-system data structures onto the disk. These data structures may include maps of free and allocated ...
System Calls,Kernel Mode, and Process
... A user program can’t access data belonging to the operating system or other user programs! ...
... A user program can’t access data belonging to the operating system or other user programs! ...
Linux-Spr-2001-sect-1-group
... – Mechanism for dealing with contiguous blocks of pages mapped to contiguous blocks of page frames. • Buddy system is used where the kernel keeps a list of contiguous page frame groups of a fixed size. • Groups can have 1, 2, 4, 8, 16, or 32 page frames. • Groups split and merged using buddy algorit ...
... – Mechanism for dealing with contiguous blocks of pages mapped to contiguous blocks of page frames. • Buddy system is used where the kernel keeps a list of contiguous page frame groups of a fixed size. • Groups can have 1, 2, 4, 8, 16, or 32 page frames. • Groups split and merged using buddy algorit ...