ppt - CSE Labs User Home Pages
... Quality of Service (QoS)? Name resolution? (is DNS “in the network”?) • Web or media caches? ...
... Quality of Service (QoS)? Name resolution? (is DNS “in the network”?) • Web or media caches? ...
UNB
... Ubiquitous Network Browser (UNB) Masato SAITO Ph.D. candidate, Graduate School of Media and Governance, KEIO University ...
... Ubiquitous Network Browser (UNB) Masato SAITO Ph.D. candidate, Graduate School of Media and Governance, KEIO University ...
Compant Presentation
... called “Xstream IP” suitable for use by Internet Service Providers (ISP), Application Service Providers (ASP) Corporate and Enterprise Users. However this service does not fulfill all our service requirements or market aspirations therefore we are currently in the process of developing a DVB-RCS bas ...
... called “Xstream IP” suitable for use by Internet Service Providers (ISP), Application Service Providers (ASP) Corporate and Enterprise Users. However this service does not fulfill all our service requirements or market aspirations therefore we are currently in the process of developing a DVB-RCS bas ...
QoS Guarantee in Wirless Network
... – How are the data performance metrics (throughput, delay) impacted by the particular motion patterns, – How do the motion patterns impact the data traffic, ...
... – How are the data performance metrics (throughput, delay) impacted by the particular motion patterns, – How do the motion patterns impact the data traffic, ...
Appendix B Network Basics - Austin Community College
... a) By sending high frequency signals that are inaudible to humans over existing telephone lines b) By connecting computers with peripheral devices c) By connecting many home computer devices over one line so that each one can share the Internet connection d) By transmitting radio signals from one co ...
... a) By sending high frequency signals that are inaudible to humans over existing telephone lines b) By connecting computers with peripheral devices c) By connecting many home computer devices over one line so that each one can share the Internet connection d) By transmitting radio signals from one co ...
INTERNET
... the following must be in place: E-mail server: this is a computer on the internet that receives incoming messages and delivers outgoing messages. It allocates a certain amount of storage to hold mail for registered users. E-mail client: this is a program that enables you to read and compose e-mail m ...
... the following must be in place: E-mail server: this is a computer on the internet that receives incoming messages and delivers outgoing messages. It allocates a certain amount of storage to hold mail for registered users. E-mail client: this is a program that enables you to read and compose e-mail m ...
technical summary 2011
... Business case for WSN 802.11p: New standard for wireless vehicular transmission WSN and power consumption: new techniques Diffusion of mobile technologies (1G, 2G, 3G,..) WSN technologies are ready for several applications : ehealth, geographical, etc… Vehicular applications fo 802.11p have been stu ...
... Business case for WSN 802.11p: New standard for wireless vehicular transmission WSN and power consumption: new techniques Diffusion of mobile technologies (1G, 2G, 3G,..) WSN technologies are ready for several applications : ehealth, geographical, etc… Vehicular applications fo 802.11p have been stu ...
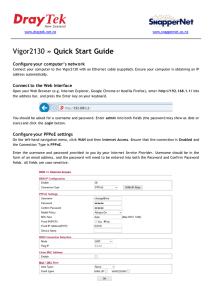
Vigor2130 » Quick Start Guide
... Configure your computer’s network Connect your computer to the Vigor2130 with an Ethernet cable (supplied). Ensure your computer is obtaining an IP address automatically. ...
... Configure your computer’s network Connect your computer to the Vigor2130 with an Ethernet cable (supplied). Ensure your computer is obtaining an IP address automatically. ...
Computer Networking
... •A protocol is nothing more than an ________________________________________________________. •The sender and receiver, and everyone in between, must agree on the rules, the protocol. •Protocol: An agreed form of communications. •TCP/IP is a suite of protocols. •IP (Internet Protocol) is used for se ...
... •A protocol is nothing more than an ________________________________________________________. •The sender and receiver, and everyone in between, must agree on the rules, the protocol. •Protocol: An agreed form of communications. •TCP/IP is a suite of protocols. •IP (Internet Protocol) is used for se ...
PowerPoint File - Regis University: Academic Web Server for Faculty
... associated with an IP address • If the destination address is not in the same network, ARP determines the next hop ...
... associated with an IP address • If the destination address is not in the same network, ARP determines the next hop ...
This Acceptable Use Policy document, including the following list of
... 10. Knowingly engage in any activities designed to harass, or that will cause a denial-ofservice (e.g., synchronized number sequence attacks) to any other user whether on the GOGEBICRANGE.NET, LLC network or on another provider’s network. 11. Using GOGEBICRANGE.NET, LLC’s Services to interfere with ...
... 10. Knowingly engage in any activities designed to harass, or that will cause a denial-ofservice (e.g., synchronized number sequence attacks) to any other user whether on the GOGEBICRANGE.NET, LLC network or on another provider’s network. 11. Using GOGEBICRANGE.NET, LLC’s Services to interfere with ...
IP Transit solution offering high quality connectivity
... All accesses have true bidirectional bandwidth: we do not use traffic shapping or contention within our backbone. If you are operating outside Portugal, connect with us using an international circuit (submarine cable or satellite) from your CPE up to our nearest IP platform node and you will have th ...
... All accesses have true bidirectional bandwidth: we do not use traffic shapping or contention within our backbone. If you are operating outside Portugal, connect with us using an international circuit (submarine cable or satellite) from your CPE up to our nearest IP platform node and you will have th ...
G-Lab Deep: Cross-layer Composition and
... Based on the specific user intent to make an emergency call a workflow of services within the service and network layer must be triggered which together form the emergency call. This workflow may invoke auxiliary services like “get location”, “make a call” and “reserve line” to support the nature of ...
... Based on the specific user intent to make an emergency call a workflow of services within the service and network layer must be triggered which together form the emergency call. This workflow may invoke auxiliary services like “get location”, “make a call” and “reserve line” to support the nature of ...
Towards the future: What next for Telecom Businesses?
... 250 billion minutes of int’l voice/fax traffic 2.5 trillion minutes of total voice/fax traffic 1’000’000 Gigabits (1 Petabit) per second of Internet traffic Services market of around US$1.1 trillion Equipment market of around US$400 billion ...
... 250 billion minutes of int’l voice/fax traffic 2.5 trillion minutes of total voice/fax traffic 1’000’000 Gigabits (1 Petabit) per second of Internet traffic Services market of around US$1.1 trillion Equipment market of around US$400 billion ...
MetroFi Cupertino - Wireless Internet Institute
... Provisioning of subscribers is fully automated, zero-touch, standards-based system Up to 8 separate secure, private networks can be operated on the same infrastructure Quality of service can support future applications such as Voice over IP and much higher subscriber speeds The Wireless Internet Ins ...
... Provisioning of subscribers is fully automated, zero-touch, standards-based system Up to 8 separate secure, private networks can be operated on the same infrastructure Quality of service can support future applications such as Voice over IP and much higher subscriber speeds The Wireless Internet Ins ...
Overview
... • A free open source utility for network exploration or security auditing. • Designed to rapidly scan large networks, although it works fine against single hosts. ...
... • A free open source utility for network exploration or security auditing. • Designed to rapidly scan large networks, although it works fine against single hosts. ...
Internet - CCIT34VC
... addresses; browsers request the DNS to provide the IP address so that it can locate website or mail server. • Dynamic host configuration protocol server, (DHCP), hqnd out the node number to each device • Active Directory Domain controller, server running AD Dservices; stores directory data & manages ...
... addresses; browsers request the DNS to provide the IP address so that it can locate website or mail server. • Dynamic host configuration protocol server, (DHCP), hqnd out the node number to each device • Active Directory Domain controller, server running AD Dservices; stores directory data & manages ...
Internet 0: Interdevice Internetworking - Publications
... to be able to use them to direct packets properly. The second name is fixed for a particular device. In Ethernet chips these are called MAC (Media Access Control) addresses; blocks of them are assigned to manufacturers to burn into their chips. Since that system would be unwieldy to centrally manage ...
... to be able to use them to direct packets properly. The second name is fixed for a particular device. In Ethernet chips these are called MAC (Media Access Control) addresses; blocks of them are assigned to manufacturers to burn into their chips. Since that system would be unwieldy to centrally manage ...
Gelsen-Net
... performance, ensuring quality of service, and validating service level cloud-hosted applications and meeting SLAs, not only did the company need to be sure their network was performing at premium levels, they required flexibility and visibility into service performance from their datacenters to clie ...
... performance, ensuring quality of service, and validating service level cloud-hosted applications and meeting SLAs, not only did the company need to be sure their network was performing at premium levels, they required flexibility and visibility into service performance from their datacenters to clie ...
Lecture 5
... 1.4 Delay, loss and throughput in packet-switched networks 1.5 Protocol layers, service models 1.6 Networks under attack: security 1.7 History Introduction ...
... 1.4 Delay, loss and throughput in packet-switched networks 1.5 Protocol layers, service models 1.6 Networks under attack: security 1.7 History Introduction ...
Communication Trends and Applications
... Emergence of Internet Appliances • Internet appliances are devices that can be used without explicit programming • The software code necessary will be stored in firmware in the appliances • Functionalities of the appliances could well be chosen with the use of buttons that may resemble the buttons ...
... Emergence of Internet Appliances • Internet appliances are devices that can be used without explicit programming • The software code necessary will be stored in firmware in the appliances • Functionalities of the appliances could well be chosen with the use of buttons that may resemble the buttons ...
a presentation for Company Name date
... as a one-size-fits-all business network. That’s why we offer more than managed IP network solutions — we offer a flexible, customer-centric approach. In designing, building and managing your network, our dedicated project-management and personalized-care teams adapt to meet the needs of your organiz ...
... as a one-size-fits-all business network. That’s why we offer more than managed IP network solutions — we offer a flexible, customer-centric approach. In designing, building and managing your network, our dedicated project-management and personalized-care teams adapt to meet the needs of your organiz ...
IP Convergence - blabs.apnic.net
... responses for each class of service usage You could support both high resilience high quality real time and various profiles of data services, and all points in between within a common switched network platform You only needed a single protocol, a single carriage architecture and a single OSS (and a ...
... responses for each class of service usage You could support both high resilience high quality real time and various profiles of data services, and all points in between within a common switched network platform You only needed a single protocol, a single carriage architecture and a single OSS (and a ...
What is the Internet?
... cables, phone lines, wireless broadcast or satellite. A server may store and forward: web pages e-mail files media ...
... cables, phone lines, wireless broadcast or satellite. A server may store and forward: web pages e-mail files media ...
EECP 0442
... the Internet, your ISP (Internet Service Provider) will assign an IP-address to you. Even if a network is NOT connected to the Internet, it has become custom to use on private networks a range of IP-addresses, which are reserved for private networks (that makes it later possible to connect your priv ...
... the Internet, your ISP (Internet Service Provider) will assign an IP-address to you. Even if a network is NOT connected to the Internet, it has become custom to use on private networks a range of IP-addresses, which are reserved for private networks (that makes it later possible to connect your priv ...