Chapter 3 Control Methods
... Problem: Guessing Numbers Write a program that randomly generates an integer between 0 and 100, inclusive. The program prompts the user to enter a number continuously until the number matches the randomly generated number. For each user input, the program tells the user whether the input is too low ...
... Problem: Guessing Numbers Write a program that randomly generates an integer between 0 and 100, inclusive. The program prompts the user to enter a number continuously until the number matches the randomly generated number. For each user input, the program tells the user whether the input is too low ...
MapReduce on Multi-core
... MapReduce framework the programmer is only concerned with expressing a given problem or computation in a functional programming model. Once these functions are defined by the programmer, the runtime system takes the responsibility of automatically parallelising it on the given hardware architecture. ...
... MapReduce framework the programmer is only concerned with expressing a given problem or computation in a functional programming model. Once these functions are defined by the programmer, the runtime system takes the responsibility of automatically parallelising it on the given hardware architecture. ...
03slide
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
The Racket Manifesto - Brown University Department of Computer
... (underlined) to create a function application; otherwise it signals an error. On export, call is renamed to #%app, meaning when another module specifies this module as its language, the compiler uses the call syntax to elaborate the module’s function applications, e.g., ...
... (underlined) to create a function application; otherwise it signals an error. On export, call is renamed to #%app, meaning when another module specifies this module as its language, the compiler uses the call syntax to elaborate the module’s function applications, e.g., ...
03Selection
... To format output using the System.out.printf method (§3.16). To examine the rules governing operator precedence and associativity (§3.17). To get user confirmation using confirmation dialogs (§3.18). To apply common techniques to debug errors (§3.19). Liang, Introduction to Java Programming, Ninth E ...
... To format output using the System.out.printf method (§3.16). To examine the rules governing operator precedence and associativity (§3.17). To get user confirmation using confirmation dialogs (§3.18). To apply common techniques to debug errors (§3.19). Liang, Introduction to Java Programming, Ninth E ...
Chapter 3 Control Methods
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
- CSE@IIT Delhi
... Let's say you turn state's evidence and need to "get on the lamb." If you wait /too long, what will happen? You'll end up on the sheep You'll end up on the cow You'll end up on the goat You'll end up on the emu ...
... Let's say you turn state's evidence and need to "get on the lamb." If you wait /too long, what will happen? You'll end up on the sheep You'll end up on the cow You'll end up on the goat You'll end up on the emu ...
Chapter 3 Control Methods
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
Lecture10
... Makes the subnet structure of a network invisible outside the organization’s private network. External Internet does not need to know internal subnet structure. To reach any host, external routers only need to know the path to the “gateway” router for the entire subnetwork. Subnetting reduces the si ...
... Makes the subnet structure of a network invisible outside the organization’s private network. External Internet does not need to know internal subnet structure. To reach any host, external routers only need to know the path to the “gateway” router for the entire subnetwork. Subnetting reduces the si ...
11slide_Exception_Handling
... To explore the advantages of using exception handling (§14.2). To distinguish exception types: Error (fatal) vs. Exception (nonfatal) and checked vs. unchecked (§14.3). To declare exceptions in a method header (§14.4.1). To throw exceptions in a method (§14.4.2). To write a try-catch block to handle ...
... To explore the advantages of using exception handling (§14.2). To distinguish exception types: Error (fatal) vs. Exception (nonfatal) and checked vs. unchecked (§14.3). To declare exceptions in a method header (§14.4.1). To throw exceptions in a method (§14.4.2). To write a try-catch block to handle ...
JAVA-Selections
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
03slide
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
... To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operator precedence and associativity ...
JSJS - Project Proposal
... for assigning values to identifiers to express the concept of all values being immutable more emphatically. • Everything is an Expression Every statement in JSJS is an expression that evaluates to a result of some type, exactly like in OCaml. We will also provide a Unit type, to allow for side-effec ...
... for assigning values to identifiers to express the concept of all values being immutable more emphatically. • Everything is an Expression Every statement in JSJS is an expression that evaluates to a result of some type, exactly like in OCaml. We will also provide a Unit type, to allow for side-effec ...
Programming with Multiple Paradigms in Lua - DI PUC-Rio
... where variables live in activation records allocated in an array-based stack. – It is amenable to a one-pass compiler that generates code on the fly, without intermediate representations. ...
... where variables live in activation records allocated in an array-based stack. – It is amenable to a one-pass compiler that generates code on the fly, without intermediate representations. ...
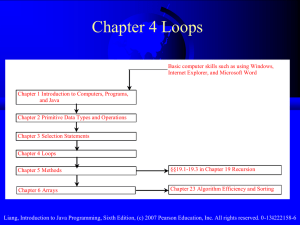
Chapter 4
... Liang, Introduction to Java Programming, Sixth Edition, (c) 2007 Pearson Education, Inc. All rights reserved. 0-13-222158-6 ...
... Liang, Introduction to Java Programming, Sixth Edition, (c) 2007 Pearson Education, Inc. All rights reserved. 0-13-222158-6 ...
Chapter 3 Control Methods
... Liang, Introduction to Java Programming, Sixth Edition, (c) 2007 Pearson Education, Inc. All rights reserved. 0-13-222158-6 ...
... Liang, Introduction to Java Programming, Sixth Edition, (c) 2007 Pearson Education, Inc. All rights reserved. 0-13-222158-6 ...
TCP/UDP Sockets
... – (family, string_ptr, address_ptr) – Convert IP address string to network byte ordered 32 or 128 bit value – 1 on success, -1 on failure, 0 on invalid input ...
... – (family, string_ptr, address_ptr) – Convert IP address string to network byte ordered 32 or 128 bit value – 1 on success, -1 on failure, 0 on invalid input ...
04-support
... In some programming environments some of the patterns are very well supported Understanding the low-level details behind these structures is important for effectively using them Describing these structures as patterns provides guidance for implementing them from scratch Combine patterns in different ...
... In some programming environments some of the patterns are very well supported Understanding the low-level details behind these structures is important for effectively using them Describing these structures as patterns provides guidance for implementing them from scratch Combine patterns in different ...
int
... you. In general, a for loop may be used if the number of repetitions is known, as, for example, when you need to print a message 100 times. A while loop may be used if the number of repetitions is not known, as in the case of reading the numbers until the input is 0. A do-while loop can be used to r ...
... you. In general, a for loop may be used if the number of repetitions is known, as, for example, when you need to print a message 100 times. A while loop may be used if the number of repetitions is not known, as in the case of reading the numbers until the input is 0. A do-while loop can be used to r ...
Language of the Month
... Ruby – An Overview Ruby is a multi-paradigm programming language designed for ease of use and programmer happiness Ruby borrows concepts from scripting languages like perl, object oriented languages like SmallTalk, and functional languages like Lisp Ruby was created by Yukihiro “matz” Matsumo ...
... Ruby – An Overview Ruby is a multi-paradigm programming language designed for ease of use and programmer happiness Ruby borrows concepts from scripting languages like perl, object oriented languages like SmallTalk, and functional languages like Lisp Ruby was created by Yukihiro “matz” Matsumo ...
Chapter 17
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
17slide
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
ppt
... generally we have tuple types with any number of components. The components can be extracted by means of projection functions. Product types more often appear as record types, which attach a label or field name to each component. Example (Ada): ...
... generally we have tuple types with any number of components. The components can be extracted by means of projection functions. Product types more often appear as record types, which attach a label or field name to each component. Example (Ada): ...
ppt
... generally we have tuple types with any number of components. The components can be extracted by means of projection functions. Product types more often appear as record types, which attach a label or field name to each component. Example (Ada): ...
... generally we have tuple types with any number of components. The components can be extracted by means of projection functions. Product types more often appear as record types, which attach a label or field name to each component. Example (Ada): ...