Slides 05
... What is the advantage of a JComboBox over a set of radio buttons? What is the disadvantage? Answer: If you have many options, a set of radio buttons takes up a large area. A combo box can show many options without using up much space. But the user cannot see the options as easily. ...
... What is the advantage of a JComboBox over a set of radio buttons? What is the disadvantage? Answer: If you have many options, a set of radio buttons takes up a large area. A combo box can show many options without using up much space. But the user cannot see the options as easily. ...
Programming with Multiple Paradigms in Lua - DI PUC-Rio
... of full continuations, Lua offers one-shot continuations in the form of stackfull coroutines [6]. (Efficient implementations of coroutines are much simpler than efficient implementations of full continuations and most uses of continuations can be done with coroutines/one-shot continuations.) As an a ...
... of full continuations, Lua offers one-shot continuations in the form of stackfull coroutines [6]. (Efficient implementations of coroutines are much simpler than efficient implementations of full continuations and most uses of continuations can be done with coroutines/one-shot continuations.) As an a ...
Chapter 9
... All data and programs are ultimately just zeros and ones » each digit can have one of two values, hence binary » bit is one binary digit » byte is a group of eight bits Text files: the bits represent printable characters » one byte per character for ASCII, the most common code » for example, Java so ...
... All data and programs are ultimately just zeros and ones » each digit can have one of two values, hence binary » bit is one binary digit » byte is a group of eight bits Text files: the bits represent printable characters » one byte per character for ASCII, the most common code » for example, Java so ...
ASP - User pages
... Internet allows for client-server systems Programs can be invoked on either/both clients and servers: – Client side includes Java Applets, ActiveX components with JScript or VBScript. – Server side includes CGI and ASP ...
... Internet allows for client-server systems Programs can be invoked on either/both clients and servers: – Client side includes Java Applets, ActiveX components with JScript or VBScript. – Server side includes CGI and ASP ...
THE TAXONOMY OF BUGS 1. SYNOPSIS What are the possible
... bugs and their severity is only one component. The details of how this is done is the subject of another book; but it’s enough to say that many organizations have designed and use satisfactory, quantitative, quality metrics. Because bugs and their symptoms play a significant role in such metrics, as ...
... bugs and their severity is only one component. The details of how this is done is the subject of another book; but it’s enough to say that many organizations have designed and use satisfactory, quantitative, quality metrics. Because bugs and their symptoms play a significant role in such metrics, as ...
Chapter 18 Networking
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
9781285081953_PPT_ch12
... of Exception Handling (cont’d.) • Java’s object-oriented, error-handling technique – Statements of the program that do the “real” work are placed together, where their logic is easy to follow – Unusual, exceptional events are grouped and moved out of the way ...
... of Exception Handling (cont’d.) • Java’s object-oriented, error-handling technique – Statements of the program that do the “real” work are placed together, where their logic is easy to follow – Unusual, exceptional events are grouped and moved out of the way ...
43slide - SIUE Computer Science
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
Programming Concepts
... • In this case, the class trying to access those variables is TestMyPoint2. • The modifier private allows the creator of the class to hide data members from the outside world. • Doing this is crucial to the data encapsulation concept in Object-Oriented Programming (OOP). (not intend to elaborate on ...
... • In this case, the class trying to access those variables is TestMyPoint2. • The modifier private allows the creator of the class to hide data members from the outside world. • Doing this is crucial to the data encapsulation concept in Object-Oriented Programming (OOP). (not intend to elaborate on ...
Objectives
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
Chapter 18 Networking
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
... centralized database is usually heavily loaded because it requires extensive data manipulation and processing. In some situations, data processing is handled by the client and business rules are stored on the client side. It is preferable to use a middle tier as a buffer between a client and the dat ...
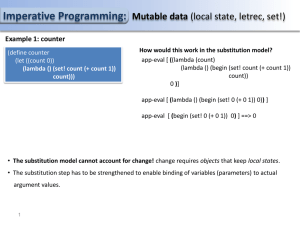
PS14
... (make-let (list (list 'action action) (list 'condition condition)) (list (make-letrec (list (list 'iter (make-lambda (list) (list (make-if (make-application 'condition (list) ) (make-begin (list (make-application 'action (list)) (make-application 'iter (list)))) ...
... (make-let (list (list 'action action) (list 'condition condition)) (list (make-letrec (list (list 'iter (make-lambda (list) (list (make-if (make-application 'condition (list) ) (make-begin (list (make-application 'action (list)) (make-application 'iter (list)))) ...
Chapter 1
... • There are different editions of the JDK: – Java SE - Java2 Standard Edition. – Java EE - Java2 Enterprise Edition. – Java ME - Java2 Micro Edition. ...
... • There are different editions of the JDK: – Java SE - Java2 Standard Edition. – Java EE - Java2 Enterprise Edition. – Java ME - Java2 Micro Edition. ...
- RehanCodes
... Encourage team members to find faults in code A fault must be considered a normal and accepted event The team as whole will develop an ethos, group identity Modules will “belong” to the team as whole A group of up to 10 egoless programmers constitutes a ...
... Encourage team members to find faults in code A fault must be considered a normal and accepted event The team as whole will develop an ethos, group identity Modules will “belong” to the team as whole A group of up to 10 egoless programmers constitutes a ...
SIP APPLICATION SERVERS & WeSIP
... • CPL stands for CALL PROCESSING LANGUAGE • XML call behaviour scripting • Protocol Agnostic • Loaded and executed in a container ...
... • CPL stands for CALL PROCESSING LANGUAGE • XML call behaviour scripting • Protocol Agnostic • Loaded and executed in a container ...
Chapter 12
... control immediately passes to one of the catch blocks; typically, a catch block does one of the following: – Completely handles the exception – Partially processes the exception; in this case, the catch block either rethrows the same exception or throws another exception for the calling environment ...
... control immediately passes to one of the catch blocks; typically, a catch block does one of the following: – Completely handles the exception – Partially processes the exception; in this case, the catch block either rethrows the same exception or throws another exception for the calling environment ...
Java applications
... two major types of applications – Computer simulations – Graphical user interfaces (GUIs) • Not all object-oriented programs are written to use a GUI ...
... two major types of applications – Computer simulations – Graphical user interfaces (GUIs) • Not all object-oriented programs are written to use a GUI ...
The Racket Manifesto - Brown University Department of Computer
... Programming is a form of problem solving. A proper approach uses the language of the domain to state the problem and to articulate solution processes. In support of this mode of programming, Racket helps programmers create and quickly deploy new languages. In particular, the mechanisms for creating ...
... Programming is a form of problem solving. A proper approach uses the language of the domain to state the problem and to articulate solution processes. In support of this mode of programming, Racket helps programmers create and quickly deploy new languages. In particular, the mechanisms for creating ...
Semantics in Declarative System
... requirements within the context of a problem domain (the implicit context) • Declarative systems do not specify how requirements are implemented to build working systems. Declarative systems only define the requirements • Declarative systems document requirements in specialized vocabularies and can ...
... requirements within the context of a problem domain (the implicit context) • Declarative systems do not specify how requirements are implemented to build working systems. Declarative systems only define the requirements • Declarative systems document requirements in specialized vocabularies and can ...