1-2
... You intend to place water lilies in the pond in your backyard. A water lily doubles in size every day. From the time you install the first lily until the entire surface of the pond is covered will take 20 days. how long will it take for the pond to be half covered? 19 days ...
... You intend to place water lilies in the pond in your backyard. A water lily doubles in size every day. From the time you install the first lily until the entire surface of the pond is covered will take 20 days. how long will it take for the pond to be half covered? 19 days ...
Distributed Query Processing Basics
... – relational algebra for SQL very well understood – algebra for XQuery mostly understood ...
... – relational algebra for SQL very well understood – algebra for XQuery mostly understood ...
6-21-05_RFID
... receive energy from the reading device (induced in antenna) short range (inches to a few feet) small, relatively inexpensive (eg 10 cents) ...
... receive energy from the reading device (induced in antenna) short range (inches to a few feet) small, relatively inexpensive (eg 10 cents) ...
Clinical Trial Ontology Achieving Consensus
... This FOA will support limited awards, each of which focuses on integrating information between two (or a few very closely related) data sets in a single subject domain. The hope is that the developed vocabularies and ontologies will serve as nucleation points for other researchers in the area to bu ...
... This FOA will support limited awards, each of which focuses on integrating information between two (or a few very closely related) data sets in a single subject domain. The hope is that the developed vocabularies and ontologies will serve as nucleation points for other researchers in the area to bu ...
Accurate and computer efficient modelling of - LaPSI
... Transient faults may be injected at different levels of abstraction by either altering the logic values or momentarily changing the voltage levels and charging states of the struck nodes. Lower level models may be obtained via device-level simulation of the effect of an ionising particle penetrating ...
... Transient faults may be injected at different levels of abstraction by either altering the logic values or momentarily changing the voltage levels and charging states of the struck nodes. Lower level models may be obtained via device-level simulation of the effect of an ionising particle penetrating ...
PolyP | a polytypic programming language extension
... The last function can be rewritten into uncurry (++), and thus we obtain the following function for attening a tree: ...
... The last function can be rewritten into uncurry (++), and thus we obtain the following function for attening a tree: ...
L10: k-Means Clustering
... k = O(n )) number of possible distinct cluster centers. But it could be exponential in k and d (the dimension when Euclidean distance used). • However, usually R = 10 is fine. • Smoothed analysis: if data perturbed randomly slightly, then R = O(n35 k 34 d8 ). This is “polynomial,” but still ridiculo ...
... k = O(n )) number of possible distinct cluster centers. But it could be exponential in k and d (the dimension when Euclidean distance used). • However, usually R = 10 is fine. • Smoothed analysis: if data perturbed randomly slightly, then R = O(n35 k 34 d8 ). This is “polynomial,” but still ridiculo ...
Solving Optimal Timing Problems Elegantly
... maximized, what its best value is as well as that of the argument. Rather than using the standard and somewhat routine examples of profit maximization (in terms of output in the simple case of one variable or the output levels of two or more products in the multivariate case) and production function ...
... maximized, what its best value is as well as that of the argument. Rather than using the standard and somewhat routine examples of profit maximization (in terms of output in the simple case of one variable or the output levels of two or more products in the multivariate case) and production function ...
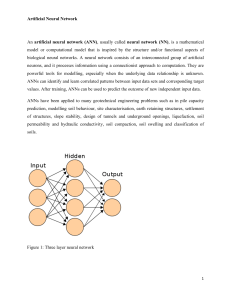
Artificial Neural Network An artificial neural network (ANN)
... Formation of training, testing and validation sets The data set is divided into three distinct sets called training, testing and validation sets. The training set is the largest set and is used by neural network to learn patterns present in the data. The testing set is used to evaluate the generaliz ...
... Formation of training, testing and validation sets The data set is divided into three distinct sets called training, testing and validation sets. The training set is the largest set and is used by neural network to learn patterns present in the data. The testing set is used to evaluate the generaliz ...
large-kin
... Continuing up to level I we get sphere S5 of radius √352ir(1+c/16) that contains the OBB at this level that contains all the 32 OBBs of level i-5 in its ...
... Continuing up to level I we get sphere S5 of radius √352ir(1+c/16) that contains the OBB at this level that contains all the 32 OBBs of level i-5 in its ...
Proof-theoretic semantics for classical mathematics
... express our notion of an ordered pair. Much of my discussion applies equally to constructive mathematics. But the type-theoretic point of view remains, for many people, restricted to the domain of constructive mathematics. The term “classical” is included in the title to indicate that, on the contr ...
... express our notion of an ordered pair. Much of my discussion applies equally to constructive mathematics. But the type-theoretic point of view remains, for many people, restricted to the domain of constructive mathematics. The term “classical” is included in the title to indicate that, on the contr ...