Using Dial-up Networking With Ethernet Capable PLCs
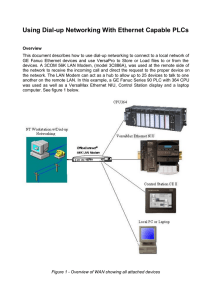
... network do not support DHCP, (such as the CPU364), DHCP was enabled so that a technician with a laptop can just connect to the network without having to first assign him or herself an IP address. Next, connect the ControlStation to the LAN Modem and give it an IP Address of 192.168.1.4, a Subnet Add ...
... network do not support DHCP, (such as the CPU364), DHCP was enabled so that a technician with a laptop can just connect to the network without having to first assign him or herself an IP address. Next, connect the ControlStation to the LAN Modem and give it an IP Address of 192.168.1.4, a Subnet Add ...
08 Common Network Services
... (c) If the server’s host key has been changed, the user is warned that the server may have been compromised 7. Client authenticates itself to server using public key (or another weaker) authentication method (a) Server sends a challenge to client encrypted with the user’s public key stored on the se ...
... (c) If the server’s host key has been changed, the user is warned that the server may have been compromised 7. Client authenticates itself to server using public key (or another weaker) authentication method (a) Server sends a challenge to client encrypted with the user’s public key stored on the se ...
Protocols and Interaction Models for Web Services
... cable through NICs Packets transmitted by one NIC can be received by all others: broadcast communication But, since packets have destination addresses, only destination NIC will (typically) copy the packet to the computer’s main memory ...
... cable through NICs Packets transmitted by one NIC can be received by all others: broadcast communication But, since packets have destination addresses, only destination NIC will (typically) copy the packet to the computer’s main memory ...
Module 2 - Santa Fe College
... By default, new computers typically come with the network cards installed, the proper drivers installed, and the network card is configured to use the Dynamic Host Configuration Protocol (DHCP) to receive TCP/IP configuration information automatically. DHCP gives the configuration settings required ...
... By default, new computers typically come with the network cards installed, the proper drivers installed, and the network card is configured to use the Dynamic Host Configuration Protocol (DHCP) to receive TCP/IP configuration information automatically. DHCP gives the configuration settings required ...
Jarkom2-7Praktikum P..
... Troubleshooting NetBIOS names by using nbtstat NetBIOS over TCP/IP (NetBT) resolves NetBIOS names to IP addresses. TCP/IP provides many options for NetBIOS name resolution, including local cache lookup, WINS server query, broadcast, DNS server query, and Lmhosts and Hosts file lookup. Nbtstat is a u ...
... Troubleshooting NetBIOS names by using nbtstat NetBIOS over TCP/IP (NetBT) resolves NetBIOS names to IP addresses. TCP/IP provides many options for NetBIOS name resolution, including local cache lookup, WINS server query, broadcast, DNS server query, and Lmhosts and Hosts file lookup. Nbtstat is a u ...
Client-Server Architectures and the Internet
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
Multiple Access Protocols Link Layer Addressing
... A’s adapter sends frame R’s adapter receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s MAC address R creates frame containing AA-toto-B IP datagram sends to B Stan Kurkovsky ...
... A’s adapter sends frame R’s adapter receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s MAC address R creates frame containing AA-toto-B IP datagram sends to B Stan Kurkovsky ...
M*N - UCL Computer Science
... whereby data is routed to the "nearest" or "best" destination as viewed by the routing topology ...
... whereby data is routed to the "nearest" or "best" destination as viewed by the routing topology ...
wireless network fixed network
... – Efficient/transparent access to shared files within a mobile environment – Support for disconnected operations while maintaining data consistency – Standard file systems (e.g., NFS) are very inefficient, almost unusable ...
... – Efficient/transparent access to shared files within a mobile environment – Support for disconnected operations while maintaining data consistency – Standard file systems (e.g., NFS) are very inefficient, almost unusable ...
connect - Kittiphan Techakittiroj
... • Clients: need services • Servers: serve the need • Middleware: Connection between Clients & Servers – software: standard, protocol, commercial ...
... • Clients: need services • Servers: serve the need • Middleware: Connection between Clients & Servers – software: standard, protocol, commercial ...
Computer Networks (COMP2322) Assignment Four (95 marks in
... Directly connected net. Route to a gateway Route to a gateway Route to a gateway Route to a gateway Route to a gateway Route to a gateway Default router ...
... Directly connected net. Route to a gateway Route to a gateway Route to a gateway Route to a gateway Route to a gateway Route to a gateway Default router ...
packet-switched - University Of Worcester
... physical network through to screen display, this was the MINIMUM number OSI committee could agree on helpful for efficient client-server communication across different networks, with different protocols ...
... physical network through to screen display, this was the MINIMUM number OSI committee could agree on helpful for efficient client-server communication across different networks, with different protocols ...
notes - Academic Csuohio
... A client broadcasts to 255.255.255.255 The source IP address is set to 0.0.0.0 if client does not know its own IP address yet Port number: 67 for server, 68 for client Requires manual configuration of tables mapping IP address to Ethernet address at the BOOTP server ...
... A client broadcasts to 255.255.255.255 The source IP address is set to 0.0.0.0 if client does not know its own IP address yet Port number: 67 for server, 68 for client Requires manual configuration of tables mapping IP address to Ethernet address at the BOOTP server ...
apache
... It has the general format of directives and their values separated by spaces. Lines beginning with '#' are ignored so are blank lines. Directives can be made more specific to files, directories, conditionals, etc using sections which have a format similar to html tags viz:
Spe ...
... It has the general format of directives and their values separated by spaces. Lines beginning with '#' are ignored so are blank lines. Directives can be made more specific to files, directories, conditionals, etc using sections which have a format similar to html tags viz:
ppt
... Easy to renumber (one number) Only need one IP Breaks transparency (need to add functionality for each new protocol) Hard for outside hosts to access inside – Ex: what if two different Quake3 servers inside? – Need non-standard ports that clients know about ...
... Easy to renumber (one number) Only need one IP Breaks transparency (need to add functionality for each new protocol) Hard for outside hosts to access inside – Ex: what if two different Quake3 servers inside? – Need non-standard ports that clients know about ...
3rd Edition: Chapter 4
... hard-coded by system admin in a file Windows: control-panel->network->configuration>tcp/ip->properties UNIX: /etc/rc.config ...
... hard-coded by system admin in a file Windows: control-panel->network->configuration>tcp/ip->properties UNIX: /etc/rc.config ...
Network Security
... All exams are closed-book and extremely time limited. Exams consist of numerical and may be multiple-choice (truefalse) questions. ...
... All exams are closed-book and extremely time limited. Exams consist of numerical and may be multiple-choice (truefalse) questions. ...
Java Remote Method Invocation
... We still have to deal with the parameters and return values, i.e. convert them into an appropriate format Call this conversion marshalling ...
... We still have to deal with the parameters and return values, i.e. convert them into an appropriate format Call this conversion marshalling ...
Understand Computer Network V
... • IP addresses that can be used by companies and individuals are divided into three classes: Class A, Class B, and Class C, based on the number of possible IP addresses in each network within each class. • The group of IP addresses assigned to an organization are unique to all other IP addresses on ...
... • IP addresses that can be used by companies and individuals are divided into three classes: Class A, Class B, and Class C, based on the number of possible IP addresses in each network within each class. • The group of IP addresses assigned to an organization are unique to all other IP addresses on ...
DoS Attacks On Wireless Voice Over IP Systems
... • Utilise a timer when a station sends a deauthentication frame to the access point. Within a certain time period if the station sends data frames to the AP then it will not deauthenticate the station and assume an attack has occurred. • Week form of protection which is not practical to implement. H ...
... • Utilise a timer when a station sends a deauthentication frame to the access point. Within a certain time period if the station sends data frames to the AP then it will not deauthenticate the station and assume an attack has occurred. • Week form of protection which is not practical to implement. H ...
The Internet Network layer: IP Addressing
... All masks are applied, one by one, to the destination address, but no matching network address is found. When it reaches the end of the table, the module gives the next-hop router’s address 180.70.65.200 and interface number m2 to ARP (link-layer protocol). This is probably an out-going packet that ...
... All masks are applied, one by one, to the destination address, but no matching network address is found. When it reaches the end of the table, the module gives the next-hop router’s address 180.70.65.200 and interface number m2 to ARP (link-layer protocol). This is probably an out-going packet that ...
Lecture (Network)
... Recipe ❒ To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. ...
... Recipe ❒ To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. ...























