Section 2
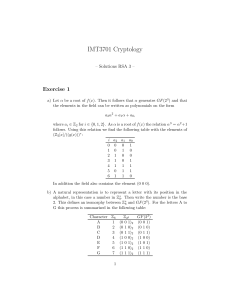
... For an affine cipher y (ax b) (mod 26) , an enemy must know the multiplicative parameter a and additive parameter b in order to decipher and break a message. Once a and b are known, x a 1 ( y b) (mod 26) can be computed and the message broken. Two methods of attack can be used to attempt to ...
... For an affine cipher y (ax b) (mod 26) , an enemy must know the multiplicative parameter a and additive parameter b in order to decipher and break a message. Once a and b are known, x a 1 ( y b) (mod 26) can be computed and the message broken. Two methods of attack can be used to attempt to ...
Answers- Lines and slope
... Therefore the equation is given by y – 4 = -2(x-0) or y - 4 = -2x or 2x + y =4 16. A car cost $20,000 and depreciates linearly at the rate of $3000 per year. Find the equation of linear depreciation and the value of the car 5 years from now. Solution: y= mx + b is the equation of linear depreciation ...
... Therefore the equation is given by y – 4 = -2(x-0) or y - 4 = -2x or 2x + y =4 16. A car cost $20,000 and depreciates linearly at the rate of $3000 per year. Find the equation of linear depreciation and the value of the car 5 years from now. Solution: y= mx + b is the equation of linear depreciation ...
part 1
... taking the letters and the interpretations according to the generally established conventions, are inexact or do not make sense, but from which we can deduce exact results in modifying and altering them according to fixed rules either the equations themselves or the symbols which comprise them. The ...
... taking the letters and the interpretations according to the generally established conventions, are inexact or do not make sense, but from which we can deduce exact results in modifying and altering them according to fixed rules either the equations themselves or the symbols which comprise them. The ...
Computability of Heyting algebras and Distributive Lattices
... element such that every element has a (unique) pseudocomplement. Note that a pseudocomplemented lattice must also have a greatest element, 0∗ (by definition of the pseudocomplement). A Boolean algebra B is one example of a pseudocomplemented lattice, where x∗ is the complement of x for every x ∈ B. ...
... element such that every element has a (unique) pseudocomplement. Note that a pseudocomplemented lattice must also have a greatest element, 0∗ (by definition of the pseudocomplement). A Boolean algebra B is one example of a pseudocomplemented lattice, where x∗ is the complement of x for every x ∈ B. ...
Slides
... a nontrivial divisor p and v is a k -th power, then k is divisible by p . To test for divisibility by power of divisors we use GCD with derivative. More precisely, if v is divisible by p than N and L have common factor, that is Res(N , L ) = 0. This works if ψ is not a logarithm. For k ≥ 3 we get se ...
... a nontrivial divisor p and v is a k -th power, then k is divisible by p . To test for divisibility by power of divisors we use GCD with derivative. More precisely, if v is divisible by p than N and L have common factor, that is Res(N , L ) = 0. This works if ψ is not a logarithm. For k ≥ 3 we get se ...
Introduction to representation theory
... Representation theory was born in 1896 in the work of the German mathematician F. G. Frobenius. This work was triggered by a letter to Frobenius by R. Dedekind. In this letter Dedekind made the following observation: take the multiplication table of a finite group G and turn it into a matrix XG by r ...
... Representation theory was born in 1896 in the work of the German mathematician F. G. Frobenius. This work was triggered by a letter to Frobenius by R. Dedekind. In this letter Dedekind made the following observation: take the multiplication table of a finite group G and turn it into a matrix XG by r ...