IPv6 Transition Mechanisms and Strategies
... The Care-of-Address is the second IP address that is related to a foreign network, and that changes each time the host attaches to a different physical network (used for routing) A Mobile Host (MH) is allowed to roam to any IP network while other nodes connect using the original home address T ...
... The Care-of-Address is the second IP address that is related to a foreign network, and that changes each time the host attaches to a different physical network (used for routing) A Mobile Host (MH) is allowed to roam to any IP network while other nodes connect using the original home address T ...
Ayodele Damola
... Thanks to my industrial supervisor at Ericsson Mr. Hans Mickelsson first for selecting me for this thesis project and for his continuous help and support along the whole way. Thank you Hans. Thanks to Mr. Jan Söderström for the opportunity to do my project at Ericsson Research. Thanks to Mr. Torbjör ...
... Thanks to my industrial supervisor at Ericsson Mr. Hans Mickelsson first for selecting me for this thesis project and for his continuous help and support along the whole way. Thank you Hans. Thanks to Mr. Jan Söderström for the opportunity to do my project at Ericsson Research. Thanks to Mr. Torbjör ...
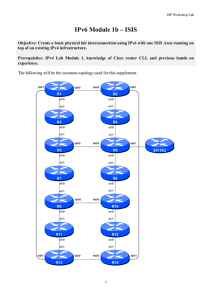
Module 01 - IPv6 ISIS and iBGP
... Nothing will break if IPv6 CEF is not enabled, but more advanced features such as NetFlow will not function without IPv6 CEF being enabled. 3. Disable IPv6 Source Routing. Unless you really believe there is a need for it, source routing should be disabled. This option, enabled by default, allows the ...
... Nothing will break if IPv6 CEF is not enabled, but more advanced features such as NetFlow will not function without IPv6 CEF being enabled. 3. Disable IPv6 Source Routing. Unless you really believe there is a need for it, source routing should be disabled. This option, enabled by default, allows the ...
On the Optimal Path Length for Tor
... Through analysis, simulation, and experiments performed on the live Tor network, we critically evaluate the advantages and disadvantages of two-hop and three-hop paths from security and performance perspectives. In addition, we identify and discuss a variety of open issues related to the security a ...
... Through analysis, simulation, and experiments performed on the live Tor network, we critically evaluate the advantages and disadvantages of two-hop and three-hop paths from security and performance perspectives. In addition, we identify and discuss a variety of open issues related to the security a ...
Business Ready Branch Solutions for Enterprise and Small
... These attributes influence the use of specific features and require special considerations when designing a branch office. For example, if a branch office is connected to the Internet, an IPSec VPN may be required for data privacy between branch and home offices or mobile workers. Another example is ...
... These attributes influence the use of specific features and require special considerations when designing a branch office. For example, if a branch office is connected to the Internet, an IPSec VPN may be required for data privacy between branch and home offices or mobile workers. Another example is ...
ppt
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...
Institutionen för systemteknik Multiple Synchronized Video Streams on IP Network
... applications could use a poorer resolution and a lower frame rate to achieve it's goals. The communication between a camera and an observer depends much on the distance between them and on the contents. If the observer is far away the information will reach the observer with delay, and if the medium ...
... applications could use a poorer resolution and a lower frame rate to achieve it's goals. The communication between a camera and an observer depends much on the distance between them and on the contents. If the observer is far away the information will reach the observer with delay, and if the medium ...
PPT - CS.Duke
... • Start with a full broadcast tree to all links (RPB) • Prune unnecessary links – Hosts interested in G periodically announce membership – If a leaf network does not have any member, sends a prune message to parent • Augment distance vector to propagate groups interested to other routers • Only do s ...
... • Start with a full broadcast tree to all links (RPB) • Prune unnecessary links – Hosts interested in G periodically announce membership – If a leaf network does not have any member, sends a prune message to parent • Augment distance vector to propagate groups interested to other routers • Only do s ...
Towards truly open and commoditized Sdn in openstack
... OK, Questions We Got! Q: What is a truly scalable SDN solution now? ...
... OK, Questions We Got! Q: What is a truly scalable SDN solution now? ...
Networks Oy - Roggeweck.net
... The GGSN is the gateway to external networks. Every connection to a fixed external data network has to go through a GGSN. The GGSN acts as the anchor point in a GPRS data connection even when the subscriber moves to another SGSN during roaming. The GGSN may accept connection request from SGSN that i ...
... The GGSN is the gateway to external networks. Every connection to a fixed external data network has to go through a GGSN. The GGSN acts as the anchor point in a GPRS data connection even when the subscriber moves to another SGSN during roaming. The GGSN may accept connection request from SGSN that i ...
IPSO-6LoWPAN - University of California, Berkeley
... • IP has always done “multi-hop” – Routers connect sub-networks to one another – The sub-networks may be the same or different physical links ...
... • IP has always done “multi-hop” – Routers connect sub-networks to one another – The sub-networks may be the same or different physical links ...
Carrier Ethernet: The next generation network and service
... Through statistical multiplexing and local switching ...
... Through statistical multiplexing and local switching ...
ppt
... • If enough capacity, no congestion, no drops Keep layer (& try next layer) • If not enough capacity, congestion, drops Drop layer (& increase time to next retry) • What about impact on other receivers? ...
... • If enough capacity, no congestion, no drops Keep layer (& try next layer) • If not enough capacity, congestion, drops Drop layer (& increase time to next retry) • What about impact on other receivers? ...
chapter 1 the nETWORK and its elements
... a shorthand for internetworking; later RFCs repeat this use, so the word started out as an adjective rather than the noun it is today. As interest in wide spread networking grew and new applications for it were developed, the Internet's technologies spread throughout the rest of the world. The netwo ...
... a shorthand for internetworking; later RFCs repeat this use, so the word started out as an adjective rather than the noun it is today. As interest in wide spread networking grew and new applications for it were developed, the Internet's technologies spread throughout the rest of the world. The netwo ...
VPN et IPSec
... public administrative entity. By contrast, a “private” facility is one where access is restricted to a defined set of entities, and third parties cannot gain access. Typically, the private resource is managed by the entities who have exclusive right of access. Examples of this type of private networ ...
... public administrative entity. By contrast, a “private” facility is one where access is restricted to a defined set of entities, and third parties cannot gain access. Typically, the private resource is managed by the entities who have exclusive right of access. Examples of this type of private networ ...
GlobeSurfer® II 1.8 - 7.2 - 7.2 S
... Your session will automatically time-out after a few minutes of inactivity. If you try to operate the management console after the session has expired the Login screen will appear and you will have to reenter your user name and password before proceeding. This feature helps to prevent unauthorized u ...
... Your session will automatically time-out after a few minutes of inactivity. If you try to operate the management console after the session has expired the Login screen will appear and you will have to reenter your user name and password before proceeding. This feature helps to prevent unauthorized u ...
Word - ITU
... are storing the contents in local hard drive. We can call this approach as subscriber-based timeshifting service. However, if we consider some cases in which it is not appropriate to save the contents locally. For example, if the IPTV terminal is PDA, the size of hard drive is limited. The network-b ...
... are storing the contents in local hard drive. We can call this approach as subscriber-based timeshifting service. However, if we consider some cases in which it is not appropriate to save the contents locally. For example, if the IPTV terminal is PDA, the size of hard drive is limited. The network-b ...
3. issues on ip multicast-based push - EECG Toronto
... on the server, lower response times, and scalability for an increasing number of receivers. But if we look at the approach from a network point view, an obvious shortfall is that CMP requires that the connecting a server with its clients is multicast capable as does AMP. We will address the issues r ...
... on the server, lower response times, and scalability for an increasing number of receivers. But if we look at the approach from a network point view, an obvious shortfall is that CMP requires that the connecting a server with its clients is multicast capable as does AMP. We will address the issues r ...
MP-IST-062-18
... which was to develop new standards of interoperability of communication networks and, apart of the interfaces, described some additional issues that are important in providing information transfer between technologically different domains. Routing in heterogeneous networks is one of the main standar ...
... which was to develop new standards of interoperability of communication networks and, apart of the interfaces, described some additional issues that are important in providing information transfer between technologically different domains. Routing in heterogeneous networks is one of the main standar ...
An Overview of the Wireless Intrusion Detection System
... requirements as well as other unique features specific to WLAN intrusion and detection of exploitation. ...
... requirements as well as other unique features specific to WLAN intrusion and detection of exploitation. ...
Optimal choice of the buffer size in the Internet routers
... problem in the TCP/IP network design. The first proposed rule of thumb for the choice of the router buffer size was to choose the buffer size equal to the Bandwidth-Delay Product (BDP) of the outgoing link [17]. This recommendation is based on very approximative considerations and it can be justifie ...
... problem in the TCP/IP network design. The first proposed rule of thumb for the choice of the router buffer size was to choose the buffer size equal to the Bandwidth-Delay Product (BDP) of the outgoing link [17]. This recommendation is based on very approximative considerations and it can be justifie ...
address address address address
... Unicast packets use the host address of the destination device as the destination address and can be routed through an internetwork. –Broadcast and multicast, however, use special addresses as the destination address. –Broadcasts are generally restricted to the local network. –Multicast traffic ma ...
... Unicast packets use the host address of the destination device as the destination address and can be routed through an internetwork. –Broadcast and multicast, however, use special addresses as the destination address. –Broadcasts are generally restricted to the local network. –Multicast traffic ma ...
riku kaura-aho scalable iot traffic generation system
... estimated that up to 50 billion devices will be connected to the internet by 2020 and most of the growth comes from Internet of Things (IoT). Along with growth, new IoT devices will use network in more diverse ways and new specialized networking technologies are needed to fulfill new requirements. F ...
... estimated that up to 50 billion devices will be connected to the internet by 2020 and most of the growth comes from Internet of Things (IoT). Along with growth, new IoT devices will use network in more diverse ways and new specialized networking technologies are needed to fulfill new requirements. F ...
Lecture-9 on 10/22/2009 - Computer Science and Engineering
... Some of these slides are adapted from various sources/individuals including but not limited to the slides from the text books by Kurose and Ross, digital libraries such as IEEE/ACM digital libraries and slides from Prof. Vahdat. Use of these slides other than for pedagogical purpose for CSE 124, may ...
... Some of these slides are adapted from various sources/individuals including but not limited to the slides from the text books by Kurose and Ross, digital libraries such as IEEE/ACM digital libraries and slides from Prof. Vahdat. Use of these slides other than for pedagogical purpose for CSE 124, may ...