V25112115
... MPLS stands for Multiprotocol Label Switching, Multiprotocol because it can be used for any Layer 3 protocol. MPLS is about glueing connectionless IP to a connection oriented Network. MPLS is something between L2 and L3. MPLS is also called Tag Switching MPLS provides a mechanism to avoid hop-by-hop ...
... MPLS stands for Multiprotocol Label Switching, Multiprotocol because it can be used for any Layer 3 protocol. MPLS is about glueing connectionless IP to a connection oriented Network. MPLS is something between L2 and L3. MPLS is also called Tag Switching MPLS provides a mechanism to avoid hop-by-hop ...
Low Carbon London - Isaac Newton Institute
... About UK Power Networks • Since 1 November 2010 UK Power Networks has been owned by the Cheung Kong Group (CKG). • UK Power Networks plans, constructs, operates and maintains three distribution networks in our regulated business. • Altogether, there are 170,000 km of underground cables and overhead ...
... About UK Power Networks • Since 1 November 2010 UK Power Networks has been owned by the Cheung Kong Group (CKG). • UK Power Networks plans, constructs, operates and maintains three distribution networks in our regulated business. • Altogether, there are 170,000 km of underground cables and overhead ...
Chapter 18
... DLCI is 10-bit data link connection identifier C/R bit tells if this is a command or a response. Not used. EA bit tells if this is an extended address FECN - informs destination that congestion is occurring (more later) BECN - informs source that congestion is occurring DE - discard eligible bit (oh ...
... DLCI is 10-bit data link connection identifier C/R bit tells if this is a command or a response. Not used. EA bit tells if this is an extended address FECN - informs destination that congestion is occurring (more later) BECN - informs source that congestion is occurring DE - discard eligible bit (oh ...
thesis_talk_mar5
... Through several metrics, one can translate from network loss to VoIP service availability (no Internet dial-tone) Current results show availability far below five 9’s, but comparable to mobile telephony – Outage statistics are similar in research and ISP ...
... Through several metrics, one can translate from network loss to VoIP service availability (no Internet dial-tone) Current results show availability far below five 9’s, but comparable to mobile telephony – Outage statistics are similar in research and ISP ...
Slide 1
... concept designs that get all your special requires into consideration, working together to achieve, on screen, a realization of your company’s conceptualization of its ...
... concept designs that get all your special requires into consideration, working together to achieve, on screen, a realization of your company’s conceptualization of its ...
06Requirements Captu..
... These requirements lead to a distinction between application that need specific service levels and those that don’t Descriptions of performance requirements for applications will separate specified services from best effort ...
... These requirements lead to a distinction between application that need specific service levels and those that don’t Descriptions of performance requirements for applications will separate specified services from best effort ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... Keywords: Mobile Ad-hoc Network (MANET), AODV, DSR, OLSR, HTTP (Hyper Text Transfer Protocol) Database (DB), Optimized Network Engineering Tool (OPNET) ...
... Keywords: Mobile Ad-hoc Network (MANET), AODV, DSR, OLSR, HTTP (Hyper Text Transfer Protocol) Database (DB), Optimized Network Engineering Tool (OPNET) ...
Click to add title
... How to identify flows, and force each flow to just one of the multiple 10GE lanes? Today: Equal Cost Multi Path -- A way to (almost) randomly assign each flow to one of the 10GE lanes. Dynamically it breaks: all the big flows fight for the same one lane. Performance degrades to 10GE for millisec ...
... How to identify flows, and force each flow to just one of the multiple 10GE lanes? Today: Equal Cost Multi Path -- A way to (almost) randomly assign each flow to one of the 10GE lanes. Dynamically it breaks: all the big flows fight for the same one lane. Performance degrades to 10GE for millisec ...
PowerPoint
... – not widely deployed as LAN technology (no end-to-end connectivity) – no native ATM applications – IP over ATM: overhead – few applications supporting traffic profile definition – addressing scheme not compatible with IP – signalling only in few backbones -> lack of interoperability ...
... – not widely deployed as LAN technology (no end-to-end connectivity) – no native ATM applications – IP over ATM: overhead – few applications supporting traffic profile definition – addressing scheme not compatible with IP – signalling only in few backbones -> lack of interoperability ...
Voice over IP (VoIP)
... of the key steps in the convergence of voice, fax, video, and data communications services. Voice over IP has now been proven feasible; the race is on to adopt standards, design terminals and gateways, and begin the roll-out of services on a global scale. Needless to say, the technical difficulties ...
... of the key steps in the convergence of voice, fax, video, and data communications services. Voice over IP has now been proven feasible; the race is on to adopt standards, design terminals and gateways, and begin the roll-out of services on a global scale. Needless to say, the technical difficulties ...
Multimedia Applications
... Skype is VoIP software; it allows voice calls over the Internet NTT (Japan) over a VoIP service to customers on the NTT network Thammasat Uni may deploy their own VoIP network In the case of NTT and Thammasat, they may use their private IP network, separate from their network attached to the Interne ...
... Skype is VoIP software; it allows voice calls over the Internet NTT (Japan) over a VoIP service to customers on the NTT network Thammasat Uni may deploy their own VoIP network In the case of NTT and Thammasat, they may use their private IP network, separate from their network attached to the Interne ...
Understanding and Testing Gigabit Ethernet Networks
... Another important application for Gigabit Ethernet test equipment is the ability to verify rate limiting or ‘bandwidth throttling’. Gigabit Ethernet networks supply enormous amounts of bandwidth, so much so that some end users may not be able to justify leasing an entire gigabit of bandwidth. In suc ...
... Another important application for Gigabit Ethernet test equipment is the ability to verify rate limiting or ‘bandwidth throttling’. Gigabit Ethernet networks supply enormous amounts of bandwidth, so much so that some end users may not be able to justify leasing an entire gigabit of bandwidth. In suc ...
Class 13 - Oct. 16 - Circuit Switching
... • Traditional circuit-switched model is hierarchical, sometimes supplemented with peer-to-peer trunks • Newer circuit-switched networks are dynamically routed: all nodes are peer-topeer, making routing more complex CSCI 465 Data Communications & Networks ...
... • Traditional circuit-switched model is hierarchical, sometimes supplemented with peer-to-peer trunks • Newer circuit-switched networks are dynamically routed: all nodes are peer-topeer, making routing more complex CSCI 465 Data Communications & Networks ...
Juniper Networks M-series : Product Overview
... early detection, random early detection, and packet marking. ...
... early detection, random early detection, and packet marking. ...
View
... Is a variation of star Not every device plugs directly into the central hub. The majority of devices connect to secondary hub that in turn is connected to the central hub The advantages and disadvantages of tree topology are generally the same as those of star. The addition of secondary hubs ...
... Is a variation of star Not every device plugs directly into the central hub. The majority of devices connect to secondary hub that in turn is connected to the central hub The advantages and disadvantages of tree topology are generally the same as those of star. The addition of secondary hubs ...
ppt
... • Free BSD with 200 byte UDP traffic at 50 packets/second (G.711 compatible), Nov 27th, 2001 for 2.5 days - have more data but it all looks similar Verify no loss at last hops DAGs provide GPS timestamps ...
... • Free BSD with 200 byte UDP traffic at 50 packets/second (G.711 compatible), Nov 27th, 2001 for 2.5 days - have more data but it all looks similar Verify no loss at last hops DAGs provide GPS timestamps ...
IP Tutorial - Electrical Engineering Department
... Name to Address: Example dns.internic.net replies with a referral to dns.aspca.org at a.b.c.d coyote.acme.com sends a query to dns.aspca.org for roadrunner.aspca.org ...
... Name to Address: Example dns.internic.net replies with a referral to dns.aspca.org at a.b.c.d coyote.acme.com sends a query to dns.aspca.org for roadrunner.aspca.org ...
Introduction. The telecommunications service market
... UMTS supports wide range of applications that posses different quality of service (QoS) requirements. Applications and services can be divided to different groups, depending on QoS requirements. Four traffic classes can been identified: Conversational class (very delay-sensitive traffic) Streami ...
... UMTS supports wide range of applications that posses different quality of service (QoS) requirements. Applications and services can be divided to different groups, depending on QoS requirements. Four traffic classes can been identified: Conversational class (very delay-sensitive traffic) Streami ...
Lan, Lan design and networking - Community College of Rhode Island
... they often handle signaling and encoding they are also layer 1 devices. Bridges and switches are considered Layer 2 devices because they use Layer 2 (MAC Address) information to make decisions on whether or not to forward packets. Routers are considered Layer 3 devices because they use Layer 3 (netw ...
... they often handle signaling and encoding they are also layer 1 devices. Bridges and switches are considered Layer 2 devices because they use Layer 2 (MAC Address) information to make decisions on whether or not to forward packets. Routers are considered Layer 3 devices because they use Layer 3 (netw ...
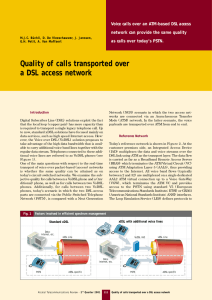
Quality of calls transported over a DSL access network
... Reference Network Today’s reference network is shown in Figure 2. At the customer premises side, an Integrated Access Device (IAD) multiplexes the data and voice streams over the DSL link using ATM as the transport layer. The data flow is carried as far as a Broadband Remote Access Server (BRAS) whi ...
... Reference Network Today’s reference network is shown in Figure 2. At the customer premises side, an Integrated Access Device (IAD) multiplexes the data and voice streams over the DSL link using ATM as the transport layer. The data flow is carried as far as a Broadband Remote Access Server (BRAS) whi ...
Overview of High Speed Network Technologies
... The link capacity is shared among several simultaneous communications. The delay in each node is meaningful due to the waiting time of the packets in the queues. It is not well-suited for isochronous transmission. It is very proper for bursty traffic as that one generated by data computer networks. ...
... The link capacity is shared among several simultaneous communications. The delay in each node is meaningful due to the waiting time of the packets in the queues. It is not well-suited for isochronous transmission. It is very proper for bursty traffic as that one generated by data computer networks. ...
PacketCable Multimedia architecture and Digital
... transport layer to view how the signal is being encapsulated. The physical layer must be up and running for everything else to work, but only looking at the physical layer does not provide much data about the underlying layers and the applications that are running there. Without testing the underlyi ...
... transport layer to view how the signal is being encapsulated. The physical layer must be up and running for everything else to work, but only looking at the physical layer does not provide much data about the underlying layers and the applications that are running there. Without testing the underlyi ...
Optimizing Matrix Multiply - Dipartimento di Matematica
... • Routing algorithm (path used): • Example in 2D torus: all east-west then all north-south (avoids deadlock). • Switching strategy: • Circuit switching: full path reserved for entire message, like the telephone. • Packet switching: message broken into separatelyrouted packets, like the post office. ...
... • Routing algorithm (path used): • Example in 2D torus: all east-west then all north-south (avoids deadlock). • Switching strategy: • Circuit switching: full path reserved for entire message, like the telephone. • Packet switching: message broken into separatelyrouted packets, like the post office. ...