Lenovo RackSwitch G8124-E Application Guide
... Note: Before using this information and the product it supports, read the general information in the Safety information and Environmental Notices and User Guide documents on the Lenovo Documentation CD and the Warranty Information document that comes with the product. ...
... Note: Before using this information and the product it supports, read the general information in the Safety information and Environmental Notices and User Guide documents on the Lenovo Documentation CD and the Warranty Information document that comes with the product. ...
TigerSwitch 10/100/1000 Management Guide
... The standard limited warranty can be upgraded to a Limited Lifetime* warranty by registering new products within 30 days of purchase from SMC or its Authorized Reseller. Registration can be accomplished via the enclosed product registration card or online via the SMC web site. Failure to register wi ...
... The standard limited warranty can be upgraded to a Limited Lifetime* warranty by registering new products within 30 days of purchase from SMC or its Authorized Reseller. Registration can be accomplished via the enclosed product registration card or online via the SMC web site. Failure to register wi ...
Lenovo Flex System Fabric EN4093R 10Gb Scalable Switch
... Lenovo Flex System Fabric EN4093R 10Gb Scalable Switch ...
... Lenovo Flex System Fabric EN4093R 10Gb Scalable Switch ...
Presentation
... The root of a tree is a TRILL switch or a link (pseudonode) determined by a separate election and represented by nickname. The ingress RBridge picks the tree, puts the tree root nickname in the “egress nickname” slot, and sets the M bit in the TRILL Header. ...
... The root of a tree is a TRILL switch or a link (pseudonode) determined by a separate election and represented by nickname. The ingress RBridge picks the tree, puts the tree root nickname in the “egress nickname” slot, and sets the M bit in the TRILL Header. ...
Brocade ICX 7450 Switch Data Sheet
... mesh together into a single logical switch and share advanced Layer 2/3 services, delivering lower price-per-port functionality without compromising performance. •• Scale-out networking: Integrates highperformance, fixed form-factor switches to create a single distributed logical switch that is inde ...
... mesh together into a single logical switch and share advanced Layer 2/3 services, delivering lower price-per-port functionality without compromising performance. •• Scale-out networking: Integrates highperformance, fixed form-factor switches to create a single distributed logical switch that is inde ...
NetDefend Family Overview & Strategy
... and Server Load Balance to provide customers continuous Internet connection and smooth network services mechanism. ...
... and Server Load Balance to provide customers continuous Internet connection and smooth network services mechanism. ...
nvOS Introduction 5 Introduction to nvOS Fabric
... Pluribus Netvisor uses the concept of Fabric-Cluster to describe the interconnectivity of devices into a single logical network. The concept of a virtual network (VNET) describes is a “slice” of resources that apply to a single entity with assigned resources within the fabric. The VNET contains serv ...
... Pluribus Netvisor uses the concept of Fabric-Cluster to describe the interconnectivity of devices into a single logical network. The concept of a virtual network (VNET) describes is a “slice” of resources that apply to a single entity with assigned resources within the fabric. The VNET contains serv ...
FortiGate System Administration Guide
... U.S. and other jurisdictions, and other Fortinet names herein may also be registered and/ or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under id ...
... U.S. and other jurisdictions, and other Fortinet names herein may also be registered and/ or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under id ...
Magnum Network Software – DX
... Copyright 2009 by GarrettCom. Printed in the US. All rights reserved. This manual may not be reproduced or disclosed in whole or in part by any means without the written consent of GarrettCom DynaStar is a trademark of GarrettCom. All other trademarks mentioned in this document are the property of t ...
... Copyright 2009 by GarrettCom. Printed in the US. All rights reserved. This manual may not be reproduced or disclosed in whole or in part by any means without the written consent of GarrettCom DynaStar is a trademark of GarrettCom. All other trademarks mentioned in this document are the property of t ...
Cisco TrustSec�5.0 - Systemmerkblatt
... mobile devices accessing network services and company data. ...
... mobile devices accessing network services and company data. ...
IBM Flex System EN2092 1Gb Ethernet Scalable Switch Application
... Chapter 7. 802.1X Port-Based Network Access Control Extensible Authentication Protocol over LAN . . . . . EAPoL Authentication Process . . . . . . . . . . . EAPoL Message Exchange . . . . . . . . . . . . EAPoL Port States . . . . . . . . . . . . . . . . Guest VLAN . . . . . . . . . . . . . . . . . . ...
... Chapter 7. 802.1X Port-Based Network Access Control Extensible Authentication Protocol over LAN . . . . . EAPoL Authentication Process . . . . . . . . . . . EAPoL Message Exchange . . . . . . . . . . . . EAPoL Port States . . . . . . . . . . . . . . . . Guest VLAN . . . . . . . . . . . . . . . . . . ...
Netvisor nvOS Configuration Guide
... Networks switches with some expertise in the following areas: Network administration Storage administration Server administration Application delivery administration Network security administration ...
... Networks switches with some expertise in the following areas: Network administration Storage administration Server administration Application delivery administration Network security administration ...
Cisco TrustSec How-To Guide: Segmenting Clients and Servers in
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
PDF
... 802.1x MAC Auth Bypass (Including MAB with voice VLAN): The 802.1x protocol has three entities: client (supplicant), authenticator, and authentication server. Typically, the host PC runs the supplicant software and tries to authenticate itself by sending its credentials to the authenticator, which i ...
... 802.1x MAC Auth Bypass (Including MAB with voice VLAN): The 802.1x protocol has three entities: client (supplicant), authenticator, and authentication server. Typically, the host PC runs the supplicant software and tries to authenticate itself by sending its credentials to the authenticator, which i ...
MCT+Design+Options+and+Best+Practices+Guide+for+NetIron+
... of routed multicast traffic in order to prevents black-hole from uplink failure. • The IP interface can be either configured on ICL or on an extra link ...
... of routed multicast traffic in order to prevents black-hole from uplink failure. • The IP interface can be either configured on ICL or on an extra link ...
User Manual
... Part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy, and may cause harmful interference to radio communications if it is not installed a ...
... Part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy, and may cause harmful interference to radio communications if it is not installed a ...
Product Description
... © 2015 ZTE Corporation. All rights reserved. ZTE CONFIDENTIAL: This document contains proprietary information of ZTE and is not to be disclosed or used without the prior written permission of ZTE. Due to update and improvement of ZTE products and technologies, information in this document is subject ...
... © 2015 ZTE Corporation. All rights reserved. ZTE CONFIDENTIAL: This document contains proprietary information of ZTE and is not to be disclosed or used without the prior written permission of ZTE. Due to update and improvement of ZTE products and technologies, information in this document is subject ...
PDF - Complete Book (2.44 MB)
... www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R) Any Internet Protocol (IP) addresses and phone numbers used in this document a ...
... www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R) Any Internet Protocol (IP) addresses and phone numbers used in this document a ...
vPath - Cisco Communities
... client source, but increases deployment complexity and operation cost • Inline ADC’s become performance bottleneck high-performance ...
... client source, but increases deployment complexity and operation cost • Inline ADC’s become performance bottleneck high-performance ...
Clustered Data ONTAP 8.3 Network Management Guide
... Each node should be connected to three distinct networks. One network is for management, one is for data access, and one is for intracluster communication. The management and data networks can be logically separated. For setting up the cluster interconnect and the management network by using the sup ...
... Each node should be connected to three distinct networks. One network is for management, one is for data access, and one is for intracluster communication. The management and data networks can be logically separated. For setting up the cluster interconnect and the management network by using the sup ...
ExtremeWare 7.0 Software User Guide
... Multiple EAPS Domains Per Switch Creating and Deleting an EAPS Domain Defining the EAPS Mode of the Switch Configuring EAPS Polling Timers Configuring the Primary and Secondary Ports Configuring the EAPS Control VLAN Configuring the EAPS Protected VLANs Enabling and Disabling an EAPS Domain Enabling ...
... Multiple EAPS Domains Per Switch Creating and Deleting an EAPS Domain Defining the EAPS Mode of the Switch Configuring EAPS Polling Timers Configuring the Primary and Secondary Ports Configuring the EAPS Control VLAN Configuring the EAPS Protected VLANs Enabling and Disabling an EAPS Domain Enabling ...
Animation - Cisco Communities
... network engineers, network operators, and data center architects to allow them to quickly and effectively deploy these technologies in their data center infrastructure based on proven commonly deployed designs. ...
... network engineers, network operators, and data center architects to allow them to quickly and effectively deploy these technologies in their data center infrastructure based on proven commonly deployed designs. ...
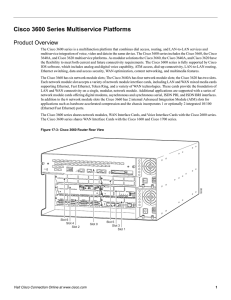
Cisco 3600 Series Multiservice Platforms
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...