Chapter x - CHAPTER TITLE
... If it is necessary to assign a head pointer, you must either save the value of the pointer in another pointer variable, or walk through the list, deleting the store, node by node, if you are through with it. If you are not through with that memory, you should reassess your desire to assign the head ...
... If it is necessary to assign a head pointer, you must either save the value of the pointer in another pointer variable, or walk through the list, deleting the store, node by node, if you are through with it. If you are not through with that memory, you should reassess your desire to assign the head ...
Priority Queues and Heaps
... of the grandchildren of the root, etc. Recall that a complete Binary Search Tree of height h has 2h+1 1 vertices in total (counting both the internal vertices and the leaves). We say that a binary tree of height h (where we have the usual notion of left and right children) is almost complete if leve ...
... of the grandchildren of the root, etc. Recall that a complete Binary Search Tree of height h has 2h+1 1 vertices in total (counting both the internal vertices and the leaves). We say that a binary tree of height h (where we have the usual notion of left and right children) is almost complete if leve ...
Linked List - Narayana Info Solutions
... blocks representing list nodes with arrows pointing to successive list nodes appears in "Programming the Logic Theory Machine" by Newell and Shaw in Proc. WJCC, February 1957. Newell and Simon were recognized with the ACM Turing Award in 1975 for having "made basic contributions to artificial intell ...
... blocks representing list nodes with arrows pointing to successive list nodes appears in "Programming the Logic Theory Machine" by Newell and Shaw in Proc. WJCC, February 1957. Newell and Simon were recognized with the ACM Turing Award in 1975 for having "made basic contributions to artificial intell ...
NBER WORKING PAPER SERIES UNINSURED IDIOSYNCRATIC INVESTMENT RISK AND AGGREGATE SAVING George-Marios Angeletos
... A key property of the neoclassical growth model is not affected by the introduction of idiosyncratic investment risk: capital accumulation exhibits diminishing returns at the aggregate level, but linear returns at the individual level. For given sequence of prices, the households’ decision problem is ...
... A key property of the neoclassical growth model is not affected by the introduction of idiosyncratic investment risk: capital accumulation exhibits diminishing returns at the aggregate level, but linear returns at the individual level. For given sequence of prices, the households’ decision problem is ...
Dynamic Connectivity
... In one update we may need to check all the edges associated with a subtree T(u) But after checking an edge, its level increases, so every edge can be checked O(log n) times If initially the graph is empty, the number of edges is at most the number of update, so we need to check O(log n) edges ...
... In one update we may need to check all the edges associated with a subtree T(u) But after checking an edge, its level increases, so every edge can be checked O(log n) times If initially the graph is empty, the number of edges is at most the number of update, so we need to check O(log n) edges ...
Model Viva Questions for “Name of the Lab: Data structure lab”
... link, pointer, to connect them. Since we can't use ordinary pointers for this, we use the void pointer. Void pointer is a generic pointer type, and capable of storing pointer to any type. Q3: What issue do auto_ptr objects address? A3: If you use auto_ptr objects you would not have to be concerned w ...
... link, pointer, to connect them. Since we can't use ordinary pointers for this, we use the void pointer. Void pointer is a generic pointer type, and capable of storing pointer to any type. Q3: What issue do auto_ptr objects address? A3: If you use auto_ptr objects you would not have to be concerned w ...
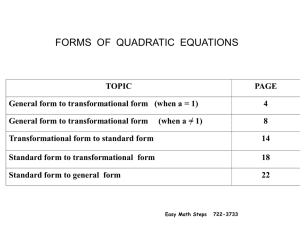
forms of quadratic equations
... CHANGING FROM GENERAL FORM TO TRANSFORMATIONAL FORM ( when "a" is not equal to 1 ) Quadratic equation in general form ...
... CHANGING FROM GENERAL FORM TO TRANSFORMATIONAL FORM ( when "a" is not equal to 1 ) Quadratic equation in general form ...
US Treasury Securities
... A lower market price isn’t a problem if you plan to hold the bond to maturity, since you will still receive your entire principal back at that time. But interest rate risk does mean you could find yourself holding a bond that pays interest at a lower rate than newer bonds being issued, so you realiz ...
... A lower market price isn’t a problem if you plan to hold the bond to maturity, since you will still receive your entire principal back at that time. But interest rate risk does mean you could find yourself holding a bond that pays interest at a lower rate than newer bonds being issued, so you realiz ...
$doc.title
... -8domestic absorption, the trade deficit as a share of GDP, and the output of tradables and nontradables. This Figure also shows the period of gradual but sustained expansion and widening trade deficit that preceded the crash, and the relatively rapid recovery after 1995. Note in addition that, fro ...
... -8domestic absorption, the trade deficit as a share of GDP, and the output of tradables and nontradables. This Figure also shows the period of gradual but sustained expansion and widening trade deficit that preceded the crash, and the relatively rapid recovery after 1995. Note in addition that, fro ...
NBER WORKING PAPER SERIES AN EQUILIBRIUM BUSINESS CYCLE FRAMEWORK
... bankruptcy costs that increase the real cost of servicing debt at date 2. In this case, the competitive equilibrium yields two mutually-consistent outcomes. On one hand, there is bankruptcy, that is firms become unable to repay their debt. On the other hand, the equilibrium relative price of nontrad ...
... bankruptcy costs that increase the real cost of servicing debt at date 2. In this case, the competitive equilibrium yields two mutually-consistent outcomes. On one hand, there is bankruptcy, that is firms become unable to repay their debt. On the other hand, the equilibrium relative price of nontrad ...
Data Structures (CS 1520) Name:___________________________ / -
... b) Mark the levels of the tree (level is the number of edges on the path from the root) c) What is the height (max. level) of the tree? The binarytree.py file contains the class definitions for BinaryTree and EmptyTree which both implement the same “binary tree” ADT interface methods. Obviously, the ...
... b) Mark the levels of the tree (level is the number of edges on the path from the root) c) What is the height (max. level) of the tree? The binarytree.py file contains the class definitions for BinaryTree and EmptyTree which both implement the same “binary tree” ADT interface methods. Obviously, the ...
Guggenheim BulletShares® ETFs An In
... buy and sell shares on public exchanges, which in turn helps to keep an ETF’s market price relatively in line with its net asset value. The creation/redemption process also serves to minimize transaction costs incurred by the ETF and to reduce the potential for capital gains transactions that result ...
... buy and sell shares on public exchanges, which in turn helps to keep an ETF’s market price relatively in line with its net asset value. The creation/redemption process also serves to minimize transaction costs incurred by the ETF and to reduce the potential for capital gains transactions that result ...
Time Value of Money
... Type in nominal rate, then Orange Shift key, then NOM% key (in orange). Type in number of periods, then Orange Shift key, then P/YR key (in orange). To find effective rate, hit Orange Shift key, then EFF% key (in orange). ...
... Type in nominal rate, then Orange Shift key, then NOM% key (in orange). Type in number of periods, then Orange Shift key, then P/YR key (in orange). To find effective rate, hit Orange Shift key, then EFF% key (in orange). ...
NBER WORKING PAPER SERIES FINANCIAL GLOBALIZATION, FINANCIAL CRISES, AND THE EXTERNAL
... income (i.e. domestic equity), and by the expectation of sharp increases in expected returns in future states in which nancial crises could occur. As a result, equity prices rise on impact when the transitional dynamics of nancial integration start, and domestic agents refrain from reducing their ...
... income (i.e. domestic equity), and by the expectation of sharp increases in expected returns in future states in which nancial crises could occur. As a result, equity prices rise on impact when the transitional dynamics of nancial integration start, and domestic agents refrain from reducing their ...
Scaling Similarity Joins over Tree-Structured Data
... from trees to other structures (i.e., the transformation is insensitive to τ ) and do not build any index to reduce the number of comparisons between tree pairs (i.e., they have to examine all pairs of trees in a nested-loop fashion). In view of this, in this paper, we propose a partition-based simi ...
... from trees to other structures (i.e., the transformation is insensitive to τ ) and do not build any index to reduce the number of comparisons between tree pairs (i.e., they have to examine all pairs of trees in a nested-loop fashion). In view of this, in this paper, we propose a partition-based simi ...
Backtracking
... other nodes (its children) Each node in the tree, other than the root, has exactly one parent parent Usually, however, we draw our trees downward, with the root at the top ...
... other nodes (its children) Each node in the tree, other than the root, has exactly one parent parent Usually, however, we draw our trees downward, with the root at the top ...
(pdf of the updated version.)
... whose paths end at a given node can be attached to this node. Data associated with a single instance cannot be attached to any single node or arc in the graph. Such private data can be stored in an external list, hash table, or a partial expansion of the graph into a tree, but all of these schemes h ...
... whose paths end at a given node can be attached to this node. Data associated with a single instance cannot be attached to any single node or arc in the graph. Such private data can be stored in an external list, hash table, or a partial expansion of the graph into a tree, but all of these schemes h ...
Efficient Evaluation of Radial Queries using the Target Tree
... need not be dense; since the target tree is a variable depth tree, some codes at various levels may go unassigned. In Figure 7c, we see such a variable depth tree. Even though the wedge with key (3, 0) has not split to form wedges at level 4, the children of wedge (3, 1) have not been assigned code ...
... need not be dense; since the target tree is a variable depth tree, some codes at various levels may go unassigned. In Figure 7c, we see such a variable depth tree. Even though the wedge with key (3, 0) has not split to form wedges at level 4, the children of wedge (3, 1) have not been assigned code ...
Lattice model (finance)

For other meanings, see lattice model (disambiguation)In finance, a lattice model [1] is a technique applied to the valuation of derivatives, where, because of path dependence in the payoff, 1) a discretized model is required and 2) Monte Carlo methods fail to account for optimal decisions to terminate the derivative by early exercise. For equity options, a typical example would be pricing an American option, where a decision as to option exercise is required at ""all"" times (any time) before and including maturity. A continuous model, on the other hand, such as Black Scholes, would only allow for the valuation of European options, where exercise is on the option's maturity date. For interest rate derivatives lattices are additionally useful in that they address many of the issues encountered with continuous models, such as pull to par.