Multi-Drive Libraries, Virtual Tape Libraries (VTL
... respectably and improve restore times since the data is being processed at disk speed rather than tape speed. Additionally, some of the devices provide licenses that emulate a multi-drive library, providing even better performance by allowing multiple clients to backup simultaneously as with the mul ...
... respectably and improve restore times since the data is being processed at disk speed rather than tape speed. Additionally, some of the devices provide licenses that emulate a multi-drive library, providing even better performance by allowing multiple clients to backup simultaneously as with the mul ...
View PDF - CiteSeerX
... There is some dispute in the KR community as to what exactly an \ontology" is. In particular, there is a question as to whether \exemplars," the individual items lling an ontological de nition count as part of the ontology. Thus, for example, does a knowledge base containing information about thous ...
... There is some dispute in the KR community as to what exactly an \ontology" is. In particular, there is a question as to whether \exemplars," the individual items lling an ontological de nition count as part of the ontology. Thus, for example, does a knowledge base containing information about thous ...
Slide 1
... LabKey/CPAS resolved these challenges through the creation of a SQL View layer. In our solution, the Data model defines a virtual schema definition in a database schema named “cabig”. We then created a set of SQL views with the same names and same columns as the UML Data model. The caCOREgenerated w ...
... LabKey/CPAS resolved these challenges through the creation of a SQL View layer. In our solution, the Data model defines a virtual schema definition in a database schema named “cabig”. We then created a set of SQL views with the same names and same columns as the UML Data model. The caCOREgenerated w ...
NIST 800-30 Risk Assessment Steps
... methodology that will work for all organizations and all situations. The following steps represent key steps to complete a comprehensive risk assessment program as outlined in NIST SP 800-30. These steps should be customized to most effectively identify risks for an organization based on its own uni ...
... methodology that will work for all organizations and all situations. The following steps represent key steps to complete a comprehensive risk assessment program as outlined in NIST SP 800-30. These steps should be customized to most effectively identify risks for an organization based on its own uni ...
What is SQL? - In Easy Steps
... in 1989 by the American National Standards Institute (ANSI) in a standard specification known as SQL-89. This was expanded three years later with publication of the SQL-92 specification by a joint committee of ANSI and the International Standards Organization (ISO). A third standard specification, S ...
... in 1989 by the American National Standards Institute (ANSI) in a standard specification known as SQL-89. This was expanded three years later with publication of the SQL-92 specification by a joint committee of ANSI and the International Standards Organization (ISO). A third standard specification, S ...
69 - ICM Software House
... Oracle SQL and PL/SQL Fundamentals training delivers the fundamentals of SQL and PL/SQL along with the benefits of the programming languages using Oracle Database technology. It helps you understand the benefits of powerful programming language, while teaching you real-world scenarios. In this cours ...
... Oracle SQL and PL/SQL Fundamentals training delivers the fundamentals of SQL and PL/SQL along with the benefits of the programming languages using Oracle Database technology. It helps you understand the benefits of powerful programming language, while teaching you real-world scenarios. In this cours ...
OLAP - Computer Science
... OLAP is the term that describes a technology that uses multidimensional view of aggregate data to provide quick access to strategic information for the purposes of advanced analysis. OLAP enables users to gain a deeper understanding and knowledge about various aspects of their corporate data through ...
... OLAP is the term that describes a technology that uses multidimensional view of aggregate data to provide quick access to strategic information for the purposes of advanced analysis. OLAP enables users to gain a deeper understanding and knowledge about various aspects of their corporate data through ...
PP453OLAP - WordPress.com
... OLAP is the term that describes a technology that uses multidimensional view of aggregate data to provide quick access to strategic information for the purposes of advanced analysis. OLAP enables users to gain a deeper understanding and knowledge about various aspects of their corporate data through ...
... OLAP is the term that describes a technology that uses multidimensional view of aggregate data to provide quick access to strategic information for the purposes of advanced analysis. OLAP enables users to gain a deeper understanding and knowledge about various aspects of their corporate data through ...
Integrated 3D Geophysical Inversion and Geological Modelling for
... has at mineral prospects over the last several years. A case study to be presented at the 2012 GRC conference will further demonstrate the application. ...
... has at mineral prospects over the last several years. A case study to be presented at the 2012 GRC conference will further demonstrate the application. ...
Lecture 21 - The University of Texas at Dallas
... Audit logs are considered good practice for business systems, and are required by federal regulations for secure systems, drug approval data, medical information disclosure, financial records, and electronic voting. Given the central role of audit logs, it is critical that they are correct and inalt ...
... Audit logs are considered good practice for business systems, and are required by federal regulations for secure systems, drug approval data, medical information disclosure, financial records, and electronic voting. Given the central role of audit logs, it is critical that they are correct and inalt ...
Proactive Compliance for Insider Threat Protection
... few years in the effort to bring security standards to a baseline for both cybersecurity and insider threat. Cybersecurity has this Administration’s attention, with accountability and deliverables outlined in several Executive Orders. I think we will all agree; we are only as strong as the weakest l ...
... few years in the effort to bring security standards to a baseline for both cybersecurity and insider threat. Cybersecurity has this Administration’s attention, with accountability and deliverables outlined in several Executive Orders. I think we will all agree; we are only as strong as the weakest l ...
Extending SSIS with Custom Tasks
... What is CEP? Complex Event Processing (CEP) is the continuous and incremental processing of event streams from multiple sources based on declarative query and pattern specifications with near-zero latency. ...
... What is CEP? Complex Event Processing (CEP) is the continuous and incremental processing of event streams from multiple sources based on declarative query and pattern specifications with near-zero latency. ...
CASME: A CASE Tool for Spatial Data Marts Design and Generation
... geographical databases [7]. In fact, the collected data can exceed human's capacity to analyze and extract interesting knowledge from large spatial databases. Many methods of knowledge discovery in geographic database have been introduced (methods using classification, discovery of spatial associati ...
... geographical databases [7]. In fact, the collected data can exceed human's capacity to analyze and extract interesting knowledge from large spatial databases. Many methods of knowledge discovery in geographic database have been introduced (methods using classification, discovery of spatial associati ...
Acceptable Use Policy for IT
... level of personal use of the company’s IT systems. If employees are uncertain they should consult their manager. Any information that is particularly sensitive or vulnerable must be encrypted and/or securely stored so that unauthorised access is prevented (or at least made extremely difficult). Howe ...
... level of personal use of the company’s IT systems. If employees are uncertain they should consult their manager. Any information that is particularly sensitive or vulnerable must be encrypted and/or securely stored so that unauthorised access is prevented (or at least made extremely difficult). Howe ...
location information
... true about the function of the VPC except for one. Which statement is not a function of the VPC? a. The VPC uses the received location information with other locally stored information that enables it to determine the appropriate ERDB to query for the routing instructions. b. The VPC uses the routin ...
... true about the function of the VPC except for one. Which statement is not a function of the VPC? a. The VPC uses the received location information with other locally stored information that enables it to determine the appropriate ERDB to query for the routing instructions. b. The VPC uses the routin ...
October 26 - Center for Computer Systems Security
... – Based on the access needed to the different classes of data. • You will architect your system and network to enforce policies at the boundaries of these classes. – You will place data to make the ...
... – Based on the access needed to the different classes of data. • You will architect your system and network to enforce policies at the boundaries of these classes. – You will place data to make the ...
Unique Triangles
... Unique Triangles are triangles that do not have an equivalent. This means there is not another triangle that has the exact dimensions or shape. What are the facts or conditions that you need to know to create a unique triangle? In other words, if two people had the same information is it possible fo ...
... Unique Triangles are triangles that do not have an equivalent. This means there is not another triangle that has the exact dimensions or shape. What are the facts or conditions that you need to know to create a unique triangle? In other words, if two people had the same information is it possible fo ...
Operational Scenarios Using the Microsoft Data
... Understanding Your Options Organizations move packaged applications and SQL Server to the cloud for a number of reasons. Some of the most common are the following: It can save money. Running on Azure isn’t always cheaper than running in your own datacenter, especially if you’ve already paid for your ...
... Understanding Your Options Organizations move packaged applications and SQL Server to the cloud for a number of reasons. Some of the most common are the following: It can save money. Running on Azure isn’t always cheaper than running in your own datacenter, especially if you’ve already paid for your ...
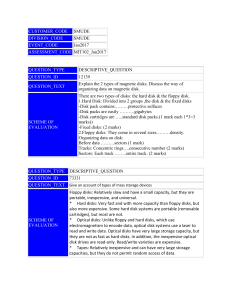
CUSTOMER_CODE SMUDE DIVISION_CODE SMUDE
... have a static size as well and they each have overflow buckets in case the first bucket gets full. To locate a particular item, the search information provided is passed through the hash function again, so the search is quickly narrowed down to roughly 1/N of the total pieces of data that might othe ...
... have a static size as well and they each have overflow buckets in case the first bucket gets full. To locate a particular item, the search information provided is passed through the hash function again, so the search is quickly narrowed down to roughly 1/N of the total pieces of data that might othe ...
6 - Department of Accounting and Information Systems ACIS | Pamplin
... firewalls, aka broadband gateways or DSL/cable modem routers, connect user’s local area network or a specific computer system to Internetworking device Residential-grade firewall software is installed directly on the user’s system Principles of Information Security, 4th Edition ...
... firewalls, aka broadband gateways or DSL/cable modem routers, connect user’s local area network or a specific computer system to Internetworking device Residential-grade firewall software is installed directly on the user’s system Principles of Information Security, 4th Edition ...
aqsproto
... and Local Agencies. EPA uses this data to assess the overall status of the nation’s air quality and to prepare reports to Congress as mandated by the Clean Air Act. EPA also uses the data to identify areas where improvements in air quality are needed. AQS provides several types of data: • Monitoring ...
... and Local Agencies. EPA uses this data to assess the overall status of the nation’s air quality and to prepare reports to Congress as mandated by the Clean Air Act. EPA also uses the data to identify areas where improvements in air quality are needed. AQS provides several types of data: • Monitoring ...
Database
... Create a MySQL Database • “root” user creates database + grants permissions – Using the WAMP console (or mysql –u root –p) • root has no initial password; just hit when asked
...
... Create a MySQL Database • “root” user creates database + grants permissions – Using the WAMP console (or mysql –u root –p) • root has no initial password; just hit
designing a multidimensional data warehouse for
... Designing A Multidimensional Data Warehouse (Ari Yanuar Ridwan) ...
... Designing A Multidimensional Data Warehouse (Ari Yanuar Ridwan) ...
CLAIMS Section 6 Overview Timely Claims Submission Clean Claim
... Plan, it is ‘Ohana’s policy that these requirements also apply to all paper and direct data entry (DDE) transactions. Standard Guides Available online or by calling Customer Service, providers may obtain the Plan’s recommended transaction guidelines. These are: ...
... Plan, it is ‘Ohana’s policy that these requirements also apply to all paper and direct data entry (DDE) transactions. Standard Guides Available online or by calling Customer Service, providers may obtain the Plan’s recommended transaction guidelines. These are: ...
Chapter 10
... An XML document can also contain structured data organized into fields and records, replacing a traditional database. In other cases, you can store data in a relationship database and use server-side software to generate XML documents for exchanging data on the Web. See Figure 10-25 to discuss this ...
... An XML document can also contain structured data organized into fields and records, replacing a traditional database. In other cases, you can store data in a relationship database and use server-side software to generate XML documents for exchanging data on the Web. See Figure 10-25 to discuss this ...