Reverse engineering of relational database applications
... without object identity). Both methods and constraints may be defined on these data structures, using a computationally complete, functional data manipulation language, which is also capable of expressing set-oriented queries in a declarative way. This DML will be used as the target language of our ...
... without object identity). Both methods and constraints may be defined on these data structures, using a computationally complete, functional data manipulation language, which is also capable of expressing set-oriented queries in a declarative way. This DML will be used as the target language of our ...
Resume - State Public Services Tribunal
... representatives of those countries associated to this region in order to validate the different aspects of the financial state of each entity however there are two main topics included in all these reviews: the actual figures associated to each financial indicator (quantitative data) and the detail ...
... representatives of those countries associated to this region in order to validate the different aspects of the financial state of each entity however there are two main topics included in all these reviews: the actual figures associated to each financial indicator (quantitative data) and the detail ...
A Quarterly, Utilization-Adjusted Series on Total Factor Productivity
... This paper describes a new real-time, quarterly growth-accounting database for the U.S. business sector. There are three major advantages relative to naïve or crude Solow residuals. First, the data on inputs, including both capital and labor, apply the careful growth-accounting methods used by the B ...
... This paper describes a new real-time, quarterly growth-accounting database for the U.S. business sector. There are three major advantages relative to naïve or crude Solow residuals. First, the data on inputs, including both capital and labor, apply the careful growth-accounting methods used by the B ...
When Development Means Business FY2000 First Quarter
... XML versus databases “The truth of the matter. The RDBMS is not going anywhere anytime soon, if ever. Even ignoring serious issues such as relational data representation in XML, the DBMS technology is a core part of too many applications in use today. Although XML may be a realistic possibility for ...
... XML versus databases “The truth of the matter. The RDBMS is not going anywhere anytime soon, if ever. Even ignoring serious issues such as relational data representation in XML, the DBMS technology is a core part of too many applications in use today. Although XML may be a realistic possibility for ...
PHP - MYSQL - ISI Academy
... How to update existing records into MySQL database using PHP. How to fetch records from MySQL database using PHP. How to show your query result into multiple pages and how to create The navigation link. Build and Design E-commerce project in PHP. ...
... How to update existing records into MySQL database using PHP. How to fetch records from MySQL database using PHP. How to show your query result into multiple pages and how to create The navigation link. Build and Design E-commerce project in PHP. ...
SC PE
... • The SCSI command processing entity within the storage target represents a logical unit (LU) and is assigned a logical unit number (LUN) for identification by the host platform. • The offset within a block is identified by the Logical Block Address (LBA). ...
... • The SCSI command processing entity within the storage target represents a logical unit (LU) and is assigned a logical unit number (LUN) for identification by the host platform. • The offset within a block is identified by the Logical Block Address (LBA). ...
ch4 - Personal Web Pages
... the sensitivity of complete-link clustering to outliers and the tendency of single-link clustering to form long chains that do not correspond to the intuitive notion of clusters as compact, spherical objects. In this method, the distance between two clusters is the average distance of all pair-wise ...
... the sensitivity of complete-link clustering to outliers and the tendency of single-link clustering to form long chains that do not correspond to the intuitive notion of clusters as compact, spherical objects. In this method, the distance between two clusters is the average distance of all pair-wise ...
NDG Vocabulary Server Outline Description
... identifier (4-byte string) Lists may aggregated in ‘Superlists’ Each ‘Superlist’ is given a semantically opaque identifier (bytes 1-3 of the component list identifiers) ...
... identifier (4-byte string) Lists may aggregated in ‘Superlists’ Each ‘Superlist’ is given a semantically opaque identifier (bytes 1-3 of the component list identifiers) ...
CH8 Br
... operations operating on the base relations to produce another relation. • A view is a virtual relation that does not actually exist in the database but is produced upon request, at time of request. • Contents of a view are defined as a query on one or more base relations. • Views are dynamic, meanin ...
... operations operating on the base relations to produce another relation. • A view is a virtual relation that does not actually exist in the database but is produced upon request, at time of request. • Contents of a view are defined as a query on one or more base relations. • Views are dynamic, meanin ...
Computational Complexity of Semantic Web Language
... • Whenever the complexity for a given problem is described as Open, with a star, (*), it is meant that its decidability is still an open question; if the star (*) is omitted, then the problem is known to be decidable but precise complexity bounds have not yet been established. If a problem is lab ...
... • Whenever the complexity for a given problem is described as Open, with a star, (*), it is meant that its decidability is still an open question; if the star (*) is omitted, then the problem is known to be decidable but precise complexity bounds have not yet been established. If a problem is lab ...
Our STORIE - Lone Star College
... ORIE is bound by applicable LSCS policy, state, and federal laws regarding what data and to what degree of detail it can release. Currently, campus requests must be approved by the campus VPI. ORIE responds to all approved campus data requests with those data we are able to provide. ORIE is also gla ...
... ORIE is bound by applicable LSCS policy, state, and federal laws regarding what data and to what degree of detail it can release. Currently, campus requests must be approved by the campus VPI. ORIE responds to all approved campus data requests with those data we are able to provide. ORIE is also gla ...
MySpacePoster
... component of the AstroGrid system, written in Java and communicating via Web services. It is under active development and its current state and future plans are described. Functionality similar to that of MySpace seems likely to be a reasonably common requirement in distributed systems, and the expe ...
... component of the AstroGrid system, written in Java and communicating via Web services. It is under active development and its current state and future plans are described. Functionality similar to that of MySpace seems likely to be a reasonably common requirement in distributed systems, and the expe ...
ppt
... Knowledge bases are created according to the activities and relationships in which we are interested. It is possible that there are more activities taking place between the identified entities, but the domain of interest is always the crucial factor. ...
... Knowledge bases are created according to the activities and relationships in which we are interested. It is possible that there are more activities taking place between the identified entities, but the domain of interest is always the crucial factor. ...
Experiment 3.4 How to analyze the allocations of extents ? Table of
... and uncompressed SQL scripts are located. Start SQL*Plus client in a way described in either Experiment 1.1 for XP operating system or in Experiment 1.2 for Linux operating system. You can use also SQL Developer described in Experiment 1.3. Connect as a user STUDENT with a password student .Execute ...
... and uncompressed SQL scripts are located. Start SQL*Plus client in a way described in either Experiment 1.1 for XP operating system or in Experiment 1.2 for Linux operating system. You can use also SQL Developer described in Experiment 1.3. Connect as a user STUDENT with a password student .Execute ...
Symptoms Autonomic Framework for Market Prediction, Analysis
... want to think about how this impacts standards around XaaS in general, e.g. is there a need for a generalized standard that would make SIS's job easier? At present is needs five different interfaces to composed his service. More details about each role and their interactions in the following sectio ...
... want to think about how this impacts standards around XaaS in general, e.g. is there a need for a generalized standard that would make SIS's job easier? At present is needs five different interfaces to composed his service. More details about each role and their interactions in the following sectio ...
Reduce
... Map-side Join: Parallel Scans • If datasets are sorted by join key, join can be accomplished by a scan over both datasets • How can we accomplish this in parallel? – Partition and sort both datasets in the same manner • In MapReduce: – Map over one dataset, read from other corresponding partition – ...
... Map-side Join: Parallel Scans • If datasets are sorted by join key, join can be accomplished by a scan over both datasets • How can we accomplish this in parallel? – Partition and sort both datasets in the same manner • In MapReduce: – Map over one dataset, read from other corresponding partition – ...
DUA #: Leave blank if new request – if amendment request, then
... has not been previously submitted (usually older DUAs that were established prior to the Attachment B requirement). The objective of this document is to acknowledge the DUA User/Requestor’s understanding that reporting can now be completed at the physician level without having to request an amendmen ...
... has not been previously submitted (usually older DUAs that were established prior to the Attachment B requirement). The objective of this document is to acknowledge the DUA User/Requestor’s understanding that reporting can now be completed at the physician level without having to request an amendmen ...
Lecture 19 - The University of Texas at Dallas
... - Potential solution: Privacy Constraint Processing Problem: Privacy violations due to un-encrypted data ...
... - Potential solution: Privacy Constraint Processing Problem: Privacy violations due to un-encrypted data ...
Learning Fingerprints for a Database Intrusion Detection System
... Only work on a relational DB, based on SQL injection in a SQL Server environment. The security of the signature/fingerprint database has not been considered in this paper. ...
... Only work on a relational DB, based on SQL injection in a SQL Server environment. The security of the signature/fingerprint database has not been considered in this paper. ...
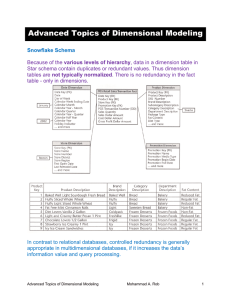
Dimensional Modeling
... Advantages: This does not increase the size of the table, since new information is updated. This allows us to keep some part of history. Disadvantages: Type 3 will not be able to keep all history where an attribute is changed more than once. For example, if Christina later moves to Texas on December ...
... Advantages: This does not increase the size of the table, since new information is updated. This allows us to keep some part of history. Disadvantages: Type 3 will not be able to keep all history where an attribute is changed more than once. For example, if Christina later moves to Texas on December ...
chap17
... used to determine record keys When the relationship is one-to-many, the primary key of the file at the one end of the relationship should be contained as a foreign key on the file at the many end of the relationship A many-to-many relationship should be divided into two one-to-many relationships w ...
... used to determine record keys When the relationship is one-to-many, the primary key of the file at the one end of the relationship should be contained as a foreign key on the file at the many end of the relationship A many-to-many relationship should be divided into two one-to-many relationships w ...
Beyond RDBMS: a rough guide to NoSQL databases
... ▪ Multi-tenant - with free and PAYG tiers ▪ Dedicated - fully-managed dedicated hardware in the cloud of your choice ▪ Local - onpremise solution ▪ replication for offline-first mobile applications on iOS, Android or HTML5 platforms ▪ Cloudant is proud contributor to the Apache CouchDB project IBM C ...
... ▪ Multi-tenant - with free and PAYG tiers ▪ Dedicated - fully-managed dedicated hardware in the cloud of your choice ▪ Local - onpremise solution ▪ replication for offline-first mobile applications on iOS, Android or HTML5 platforms ▪ Cloudant is proud contributor to the Apache CouchDB project IBM C ...
Create a New Project
... This namespace will be used to create a dimensional layer. This may require creating complex query subjects to resolve SQL traps before creating dimension objects, or for a demoralized source dimension objects to be created directly. With the information provided so far, we are able to create our di ...
... This namespace will be used to create a dimensional layer. This may require creating complex query subjects to resolve SQL traps before creating dimension objects, or for a demoralized source dimension objects to be created directly. With the information provided so far, we are able to create our di ...
Preserving Indonesia's heritage
... 3D laser scanners play an important part in mapping and documenting cultural heritage. When deterioration or unexpected natural disasters, such as floods, volcanic eruptions, earthquakes or vandalism, occur, reconstruction of historic structures based on the scanner’s delivered point clouds can be a ...
... 3D laser scanners play an important part in mapping and documenting cultural heritage. When deterioration or unexpected natural disasters, such as floods, volcanic eruptions, earthquakes or vandalism, occur, reconstruction of historic structures based on the scanner’s delivered point clouds can be a ...
Handling Errors That Occur When Writing Data to Remote
... © Copyright Informatica LLC 2016. Informatica LLC. No part of this document may be reproduced or transmitted in ...
... © Copyright Informatica LLC 2016. Informatica LLC. No part of this document may be reproduced or transmitted in ...