Should the Maastricht fiscal criteria be redefined?
... liabilities do not affect the level of general government debt and deficit, they have so far gone largely unnoticed. In November 2011, the European Parliament and the European Council adopted an improved framework for the management of economic policy in the EU (the Enhanced Economic Governance Pack ...
... liabilities do not affect the level of general government debt and deficit, they have so far gone largely unnoticed. In November 2011, the European Parliament and the European Council adopted an improved framework for the management of economic policy in the EU (the Enhanced Economic Governance Pack ...
No Slide Title - American University
... The four transaction properties are: • Atomicity requires that all parts of a transaction must be completed or the transaction is aborted. This property ensures that the database will remain in a consistent state. • Durability indicates that the database will be in a permanent consistent state afte ...
... The four transaction properties are: • Atomicity requires that all parts of a transaction must be completed or the transaction is aborted. This property ensures that the database will remain in a consistent state. • Durability indicates that the database will be in a permanent consistent state afte ...
Searches for NP : non-SUSY scenarios
... - Eloss could be so large that M may stop in the beam-pipe ! EPJC xxx (2005) E. Perez ...
... - Eloss could be so large that M may stop in the beam-pipe ! EPJC xxx (2005) E. Perez ...
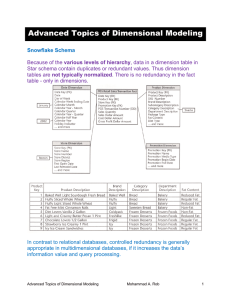
Dimensional Modeling
... A separate time dimension table should be constructed if a fine time granularity, such as minute or second, is needed. See above. A time dimension table of one-minute granularity will contain 24X60 = 1,440 rows for a day, and a table of seconds will contain 24X60X60 = 86,400 rows for a day. If exact ...
... A separate time dimension table should be constructed if a fine time granularity, such as minute or second, is needed. See above. A time dimension table of one-minute granularity will contain 24X60 = 1,440 rows for a day, and a table of seconds will contain 24X60X60 = 86,400 rows for a day. If exact ...
An introduction to creating JSF applications in Rational Application Developer Version 8.0
... interface for a set of tables in a database. The developer packages the code into a JAR file for use by the page developer. A page developer creates a new JSF-enabled Web application and imports the supplied JAR file from the application developer. The page developer creates a new JSF page for inter ...
... interface for a set of tables in a database. The developer packages the code into a JAR file for use by the page developer. A page developer creates a new JSF-enabled Web application and imports the supplied JAR file from the application developer. The page developer creates a new JSF page for inter ...
The Euro and the Geography of International Debt Flow
... a further subsidy to risk taking. For a microeconomic model of ECB refinancing operations, see Cassola et al. (2013). ...
... a further subsidy to risk taking. For a microeconomic model of ECB refinancing operations, see Cassola et al. (2013). ...
Input the title of your manuscript - International Journal of Computer
... be represented in different forms such as a decision tree, set of rules, or support vector machines, to name a few. After the classifier completes the learning phase, it can predict the class of newly added data based on the model that it learned. Quite often a concept drift may occur due to changes ...
... be represented in different forms such as a decision tree, set of rules, or support vector machines, to name a few. After the classifier completes the learning phase, it can predict the class of newly added data based on the model that it learned. Quite often a concept drift may occur due to changes ...
FrontOffice 2000 pdf spec sheet
... GoldMine Web users can use their browsers to connect anytime, from anywhere, with the rest of their team. GoldMine Web offers users the ability to manage all of their customer relationships by supporting everything from basic call center activities to management analysis and measurement functions vi ...
... GoldMine Web users can use their browsers to connect anytime, from anywhere, with the rest of their team. GoldMine Web offers users the ability to manage all of their customer relationships by supporting everything from basic call center activities to management analysis and measurement functions vi ...
Runtime Translation of the Java Bytecode to OpenCL and GPU
... library is designed in a way that allows distributed execution on many computing resources such as CPU, GPU or remote computers. When a result is received, it is passed to the set method of an object which implements the Destination interface. This method receives the resulted data and a task unique ...
... library is designed in a way that allows distributed execution on many computing resources such as CPU, GPU or remote computers. When a result is received, it is passed to the set method of an object which implements the Destination interface. This method receives the resulted data and a task unique ...
Helping the Royal Shakespeare Company Achieve High
... of Accenture’s regular clients. The theatre company required the same methodologies and leading-edge analytics software that would enable a global retailer or a financial multinational to achieve high performance. Working collaboratively with the RSC, Accenture profiled the theatre company’s current ...
... of Accenture’s regular clients. The theatre company required the same methodologies and leading-edge analytics software that would enable a global retailer or a financial multinational to achieve high performance. Working collaboratively with the RSC, Accenture profiled the theatre company’s current ...
TBR Unparalleled demands on storage shift IT expectations for managed
... more efficiently. Combining those two elements with the deep understanding and experience that Dimension Data has built around managing storage and automation will enable the customer to benefit from the processes that have been developed. Storage management, based on policies and procedures that us ...
... more efficiently. Combining those two elements with the deep understanding and experience that Dimension Data has built around managing storage and automation will enable the customer to benefit from the processes that have been developed. Storage management, based on policies and procedures that us ...
AN OVERVIEW OF FRAGMENTATION DESIGN FOR DISTRIBUTED
... The emerging of smart phone and tablet market has generated big volume of data and it grown exponentially in every minute. This gigantic volume of data also has been named as Big Data. The cohesiveness between these data is low as data might or might not be related to each other. Thus, XML is a good ...
... The emerging of smart phone and tablet market has generated big volume of data and it grown exponentially in every minute. This gigantic volume of data also has been named as Big Data. The cohesiveness between these data is low as data might or might not be related to each other. Thus, XML is a good ...
Centralize-Your-Automatic-Workload-Repository-Data-for
... – Loads files found place in the Central AWR load file space ...
... – Loads files found place in the Central AWR load file space ...
HPE Universal Discovery software data sheet
... or non-existent? Can you meet your inventory management challenges? Can you ensure you’re accurately mapping CI’s in the cloud? Without visibility into IT applications and infrastructure dependencies, it is difficult and time‑consuming to prioritize, triage, and resolve incidents. An understanding o ...
... or non-existent? Can you meet your inventory management challenges? Can you ensure you’re accurately mapping CI’s in the cloud? Without visibility into IT applications and infrastructure dependencies, it is difficult and time‑consuming to prioritize, triage, and resolve incidents. An understanding o ...
ASYCUDA Modules
... The national transit functions within ASYCUDA++ are used to monitor and control the movement of goods in transit within the country. Controlled movements can include all forms of internal transit, such as: Border to border (i.e. through transit); Border to inland office, or inland office to bord ...
... The national transit functions within ASYCUDA++ are used to monitor and control the movement of goods in transit within the country. Controlled movements can include all forms of internal transit, such as: Border to border (i.e. through transit); Border to inland office, or inland office to bord ...
What Is AJAX?
... Examples of AJAX usage include GMail and Flickr. It is largely due to these and other prominent sites that AJAX has become popular only relatively recently – the technology has been available for some time. One precursor was dynamic HTML (DHTML), which twinned HTML with CSS and JavaScript but suffer ...
... Examples of AJAX usage include GMail and Flickr. It is largely due to these and other prominent sites that AJAX has become popular only relatively recently – the technology has been available for some time. One precursor was dynamic HTML (DHTML), which twinned HTML with CSS and JavaScript but suffer ...
BWDB2UG Agenda - The Fillmore Group
... point out and discuss areas to be aware of and prepare for as well as listing many of the changes that you need to be aware of before and after an upgrade to DB2 9.7. 10:30 – 11:45: Building and Managing Efficient Data Access to DB2 Presenter: Vijay Bommireddipalli, IBM Managing performance of your ...
... point out and discuss areas to be aware of and prepare for as well as listing many of the changes that you need to be aware of before and after an upgrade to DB2 9.7. 10:30 – 11:45: Building and Managing Efficient Data Access to DB2 Presenter: Vijay Bommireddipalli, IBM Managing performance of your ...
Query_Store
... • Flush the data at specific business case intervals. For example, if performance of the DB seems to be poor around end of the month due financial reporting, consider using the Agile methodology to complete one iteration, then flush the data before the next iteration. • Keep the Max Size small enoug ...
... • Flush the data at specific business case intervals. For example, if performance of the DB seems to be poor around end of the month due financial reporting, consider using the Agile methodology to complete one iteration, then flush the data before the next iteration. • Keep the Max Size small enoug ...
slides - Indico
... IOVDbSvc takes care of the low level interactions with COOL IOVDbSvc ensures that the correct conditions objects are loaded into TDS for the event currently being analyzed ...
... IOVDbSvc takes care of the low level interactions with COOL IOVDbSvc ensures that the correct conditions objects are loaded into TDS for the event currently being analyzed ...
Simultaneous Pipelining in QPipe: Exploiting Work Sharing
... Data warehousing and scientific database applications operate on massive datasets and are characterized by complex queries accessing large portions of the database. Concurrent queries often exhibit high data and computation overlap, e.g., they access the same relations on disk, compute similar aggre ...
... Data warehousing and scientific database applications operate on massive datasets and are characterized by complex queries accessing large portions of the database. Concurrent queries often exhibit high data and computation overlap, e.g., they access the same relations on disk, compute similar aggre ...
WM2003 - Knowledge Discovery Methods - An - CEUR
... [PR99]. This approach comprises six core processes and two pragmatic modules: identification, acquisition, development, distribution, use, and preservation of knowledge as well as objectives and performance measurement of knowledge. In addition, more or less similar classifications of knowledge mana ...
... [PR99]. This approach comprises six core processes and two pragmatic modules: identification, acquisition, development, distribution, use, and preservation of knowledge as well as objectives and performance measurement of knowledge. In addition, more or less similar classifications of knowledge mana ...
The Customer Marketing Database: Cutting Costs and Improving
... Slow response time can indicate different things, depending on the question. For example, it may be necessary to know how many customers answered a survey question a certain way. A properly designed and well maintained customer marketing database should be able to deliver this answer within seconds. ...
... Slow response time can indicate different things, depending on the question. For example, it may be necessary to know how many customers answered a survey question a certain way. A properly designed and well maintained customer marketing database should be able to deliver this answer within seconds. ...
SAS® System on Network Appliance: Performance Tuning a SAS® Environment with Network Appliance Filers
... SAS NFS deployments have several important characteristics: SAS version, single host versus multiple hosts configuration, number of SAS sessions per host and host memory size versus SAS data set size. This section outlines each of these characteristics SAS Versions SAS currently has three major rele ...
... SAS NFS deployments have several important characteristics: SAS version, single host versus multiple hosts configuration, number of SAS sessions per host and host memory size versus SAS data set size. This section outlines each of these characteristics SAS Versions SAS currently has three major rele ...
SQL 2: GETTING INFORMATION INTO A DATABASE MIS2502
... `CustomerID` INT NOT NULL , `FirstName` VARCHAR(45) NULL , `LastName` VARCHAR(45) NULL , `City` VARCHAR(45) NULL , `State` VARCHAR(2) NULL , `Zip` VARCHAR(10) NULL , PRIMARY KEY (`CustomerID`) ); ...
... `CustomerID` INT NOT NULL , `FirstName` VARCHAR(45) NULL , `LastName` VARCHAR(45) NULL , `City` VARCHAR(45) NULL , `State` VARCHAR(2) NULL , `Zip` VARCHAR(10) NULL , PRIMARY KEY (`CustomerID`) ); ...
Semantic Wrapper over Relational Databases
... LOCATION.east-UTM-in-key, NULL, NULL, NULL, NULL, NULL, NULL, IMAGE.* from LOCATION, IMAGE where time > '1993/01' and exists ( select * from FIXED-STATION where by-physical-observation-station-id = physical-observation-station-id-key and ...
... LOCATION.east-UTM-in-key, NULL, NULL, NULL, NULL, NULL, NULL, IMAGE.* from LOCATION, IMAGE where time > '1993/01' and exists ( select * from FIXED-STATION where by-physical-observation-station-id = physical-observation-station-id-key and ...