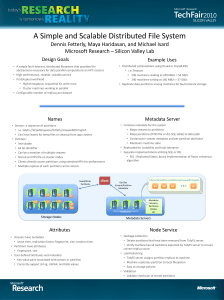
It is possible to use a simple SQL and access the
... product does not allow accessing web service as database. Microsoft’s SQL server does not have the same kind of features as RAD and DB2. It can be assumed that IBM is the only product which offers such possibilities. This gives DB2 an edge over others in this field. It is very essential for companie ...
... product does not allow accessing web service as database. Microsoft’s SQL server does not have the same kind of features as RAD and DB2. It can be assumed that IBM is the only product which offers such possibilities. This gives DB2 an edge over others in this field. It is very essential for companie ...
p1 p2 p3 pn
... • 240 machines reading at 240 MB/s = 56 GB/s • 240 machines writing at 160 MB/s = 37 GB/s • Replicate data partitions among machines for fault tolerant storage ...
... • 240 machines reading at 240 MB/s = 56 GB/s • 240 machines writing at 160 MB/s = 37 GB/s • Replicate data partitions among machines for fault tolerant storage ...
Microsoft® Office Excel® 2010: Part 3 (Second Edition)
... formulas, a lot of its features and functionality, and its powerful data analysis tools. You are likely called upon to analyze and report on data frequently, work in collaboration with others to deliver actionable organizational intelligence, and keep and maintain workbooks for all manner of purpose ...
... formulas, a lot of its features and functionality, and its powerful data analysis tools. You are likely called upon to analyze and report on data frequently, work in collaboration with others to deliver actionable organizational intelligence, and keep and maintain workbooks for all manner of purpose ...
Teradata Overview - dbmanagement.info
... •Anthem Blue/Cross •The Hartford •Zurich Kemple Life •Merck Medco •Mercy Health ...
... •Anthem Blue/Cross •The Hartford •Zurich Kemple Life •Merck Medco •Mercy Health ...
Introduction to databases from a bioinformatics perspective
... Problem-solving knowledge automates specific tasks ...
... Problem-solving knowledge automates specific tasks ...
A Comprehensive Study of Data Mining and Application
... cited by civil libertarians, and represents how control over one’s information can be a tenuous proposition. Mission creep refers to the use of data for purposes other than that for which the data was originally collected. This can occur regardless of whether the data was provided voluntarily by the ...
... cited by civil libertarians, and represents how control over one’s information can be a tenuous proposition. Mission creep refers to the use of data for purposes other than that for which the data was originally collected. This can occur regardless of whether the data was provided voluntarily by the ...
SWTMedicalInformatics
... Semantic Web and Technologies The Semantic Web is a vision of how the existing infrastructure of the World-wide Web (WWW) can be extended such that machines can interpret the meaning of data on it Semantic Web technologies are the standards and technologies that have been developed to achieve the ...
... Semantic Web and Technologies The Semantic Web is a vision of how the existing infrastructure of the World-wide Web (WWW) can be extended such that machines can interpret the meaning of data on it Semantic Web technologies are the standards and technologies that have been developed to achieve the ...
Choose between Access and Excel
... Now, wasn’t that easy? For example, a sales database typically puts information about customers — their names, addresses, and other key facts — in one table, and information about what those customers buy in another table. Organizing your data that way can make it quite powerful. Choose between Acce ...
... Now, wasn’t that easy? For example, a sales database typically puts information about customers — their names, addresses, and other key facts — in one table, and information about what those customers buy in another table. Organizing your data that way can make it quite powerful. Choose between Acce ...
Slide 1 - Carnegie Mellon University
... • Relational Markov Networks (RMN) • Other models (ILP based, Vector Space based, etc) •Overall: – Lack of direct comparison among methods – Results are usually compared to “flat” model – Splitting data into train/test sets can be an issue ...
... • Relational Markov Networks (RMN) • Other models (ILP based, Vector Space based, etc) •Overall: – Lack of direct comparison among methods – Results are usually compared to “flat” model – Splitting data into train/test sets can be an issue ...
Oracle 10g SQL Programming
... • Scalar Functions • SQL Queries - Joins • Aggregate Functions and Advanced Techniques • Data Manipulation and Transactions • Data Definition and Control Statements ...
... • Scalar Functions • SQL Queries - Joins • Aggregate Functions and Advanced Techniques • Data Manipulation and Transactions • Data Definition and Control Statements ...
Chapter 3 - Accounting and Information Systems Department
... Distinguish between management fraud and employee fraud Common types of fraud schemes Key features of SAS 78 / COSO internal control framework Objects and application of physical controls ...
... Distinguish between management fraud and employee fraud Common types of fraud schemes Key features of SAS 78 / COSO internal control framework Objects and application of physical controls ...
知识管理的IT实现 IBM知识管理解决方案
... management systems running on minicomputers and mainframes. Increasingly,however,SQL is being supported by PC database systems because it supports distributed databases(databases that are spread out over several computer systems).This enables several users on a local area network to access the same ...
... management systems running on minicomputers and mainframes. Increasingly,however,SQL is being supported by PC database systems because it supports distributed databases(databases that are spread out over several computer systems).This enables several users on a local area network to access the same ...
XDWE: A prototype to establish XML as a Native Data Source in
... retaining its natural tree structure. At the same time, we would like to obtain all the benefits of relational database management ...
... retaining its natural tree structure. At the same time, we would like to obtain all the benefits of relational database management ...
Structure and Functions of Computer Database Systems
... technology, it is clear that databases need to improve and undergo some changes. Also, the expanding base of microcomputers and the development of user-friendly applications software has increased the demand for direct access to stored data. This has increased the need for a system that ensures that ...
... technology, it is clear that databases need to improve and undergo some changes. Also, the expanding base of microcomputers and the development of user-friendly applications software has increased the demand for direct access to stored data. This has increased the need for a system that ensures that ...
Absolute Software Overview Brochure
... monitor their devices (on or off the network), knowing where they are, who’s using them, and what types of software and other applications reside on them. And they can take proactive or immediate measures for any devices that may be at risk. ...
... monitor their devices (on or off the network), knowing where they are, who’s using them, and what types of software and other applications reside on them. And they can take proactive or immediate measures for any devices that may be at risk. ...
Theory of Computation - Lightweight OCW University of Palestine
... be hidden from their users. They should not have to be aware whether the system they are using is centralized or distributed. Thus, it is transparent for the user that s/he is using a distributed system. • To make life easier for an application programmer, s/he should also not have to be aware that ...
... be hidden from their users. They should not have to be aware whether the system they are using is centralized or distributed. Thus, it is transparent for the user that s/he is using a distributed system. • To make life easier for an application programmer, s/he should also not have to be aware that ...
GIS Tutorial 1 - Basic Workbook
... containing a translation of Esri geometries and symbology. File is compressed using ZIP compression, has a .kmz extension Can be read by any KML client including ArcGIS Explorer, ArcGlobe, and Google Earth. To access: Arctoolbox> Conversion tools> To KML> Layer to KML ...
... containing a translation of Esri geometries and symbology. File is compressed using ZIP compression, has a .kmz extension Can be read by any KML client including ArcGIS Explorer, ArcGlobe, and Google Earth. To access: Arctoolbox> Conversion tools> To KML> Layer to KML ...
- Free Documents
... CCA designers must address the risks arising from vulnerable user devices and vulnerable clients Client authentication must be achieved through components. encompassing not only the server side. and externallymanaged identities Shibboleth. APIs. ...
... CCA designers must address the risks arising from vulnerable user devices and vulnerable clients Client authentication must be achieved through components. encompassing not only the server side. and externallymanaged identities Shibboleth. APIs. ...
NZAMT 91038 (1.12): Demonstrate understanding of chance and
... drinking incidents changing over time for females, so lower values are more common in the first part of the two year period. If the two lowest values are excluded from the study then the measures of spread would be much closer. As Rebecca suspects the current situation is a result of a growing trend ...
... drinking incidents changing over time for females, so lower values are more common in the first part of the two year period. If the two lowest values are excluded from the study then the measures of spread would be much closer. As Rebecca suspects the current situation is a result of a growing trend ...
Marlin Merges Digital Marketing Business from Teradata with
... Combination creates one of the largest independent digital marketing companies in the industry serving more than 3,000 customers globally LOS ANGELES, July 20, 2016 -- Marlin Equity Partners (“Marlin”) today announced that it has merged its existing portfolio company BlueHornet, a leading U.S.-based ...
... Combination creates one of the largest independent digital marketing companies in the industry serving more than 3,000 customers globally LOS ANGELES, July 20, 2016 -- Marlin Equity Partners (“Marlin”) today announced that it has merged its existing portfolio company BlueHornet, a leading U.S.-based ...
Microsoft Access – Part I (Database Design Basics) ShortCourse
... Access - Part I (database design basics) is a non-credit, 2-hour course designed as an introductory course to Microsoft Access database design. This shortcourse is the foundation for Access Part II and Access Part III short courses series. Microsoft Access is a Relational Database Management System, ...
... Access - Part I (database design basics) is a non-credit, 2-hour course designed as an introductory course to Microsoft Access database design. This shortcourse is the foundation for Access Part II and Access Part III short courses series. Microsoft Access is a Relational Database Management System, ...
Chapter 16 - Computer Information Systems
... – transactions that run frequently and will have a significant impact on performance; – transactions that are critical to the business; – times during the day/week when there will be a high demand made on the database (called the peak load). ...
... – transactions that run frequently and will have a significant impact on performance; – transactions that are critical to the business; – times during the day/week when there will be a high demand made on the database (called the peak load). ...
chapter 7 - Routledge
... Based on the principle of exponential smoothing Automatic ordering can be managed by exception Automatic replenishment relies on supply source (DC or supply depot) being able to respond directly to demand. AR Systems will alert stores to problems ...
... Based on the principle of exponential smoothing Automatic ordering can be managed by exception Automatic replenishment relies on supply source (DC or supply depot) being able to respond directly to demand. AR Systems will alert stores to problems ...
1
... – Soft, weak and phantom references require special processing during GC – Finalizers should be avoided • Will keep objects alive for one extra GC cycle • Detrimental to pause time goals ...
... – Soft, weak and phantom references require special processing during GC – Finalizers should be avoided • Will keep objects alive for one extra GC cycle • Detrimental to pause time goals ...