Jones ch13.qxd - Angelo State University
... see the column and row summaries of the table’s data. Our example includes four columns. Column one contains the variable value (row) labels “Liberal” through “Conservative.” The second column lists the frequencies, or number of cases, for each category of the variable. The third column lists the va ...
... see the column and row summaries of the table’s data. Our example includes four columns. Column one contains the variable value (row) labels “Liberal” through “Conservative.” The second column lists the frequencies, or number of cases, for each category of the variable. The third column lists the va ...
Aligning some Nicholson sheep-blowfly data sets with system input
... The presence of periodic behavior is the crux of this present work. A periods is known to be one of the discrete set of sawtooth periods used in Nicholson’s experiments. The principal tool to be employed here is “a seasonal-trend decomposition based on loess” (STL), see Cleveland et al. (1990). Both ...
... The presence of periodic behavior is the crux of this present work. A periods is known to be one of the discrete set of sawtooth periods used in Nicholson’s experiments. The principal tool to be employed here is “a seasonal-trend decomposition based on loess” (STL), see Cleveland et al. (1990). Both ...
ch8 - German Vargas
... In Chapters 2 and 3 we used “descriptive statistics” when we summarized data using tools such as graphs, and statistics such as the mean and standard deviation. Methods of inferential statistics use sample data to make an inference or conclusion about a population. The two main activities of inferen ...
... In Chapters 2 and 3 we used “descriptive statistics” when we summarized data using tools such as graphs, and statistics such as the mean and standard deviation. Methods of inferential statistics use sample data to make an inference or conclusion about a population. The two main activities of inferen ...
Evaluation of Rarity of Fingerprints in Forensics
... The fingerprint collected from the crime scene is usually only a small portion of the complete fingerprint. So the feature set extracted from the print only contains relative spatial relationship. It’s obvious that feature sets with same relative spatial relationship can lead to different rarity if ...
... The fingerprint collected from the crime scene is usually only a small portion of the complete fingerprint. So the feature set extracted from the print only contains relative spatial relationship. It’s obvious that feature sets with same relative spatial relationship can lead to different rarity if ...
Chapter 13
... standard deviation are: – It is the most frequently used measure of dispersion, and because of its mathematical properties it has widespread use in problems involving statistical inference – If the mean cannot be calculated, neither can the standard deviation – Its value is affected by the value of ...
... standard deviation are: – It is the most frequently used measure of dispersion, and because of its mathematical properties it has widespread use in problems involving statistical inference – If the mean cannot be calculated, neither can the standard deviation – Its value is affected by the value of ...
how effective is using a convenience sample to supplement a
... must be small. One way to respond to this limitation may be to focus on estimating parameters that are less subject to bias, such as within-subject differences or regression coefficients, rather than population estimates of proportions or means. One can also use post-stratification to reduce bias as ...
... must be small. One way to respond to this limitation may be to focus on estimating parameters that are less subject to bias, such as within-subject differences or regression coefficients, rather than population estimates of proportions or means. One can also use post-stratification to reduce bias as ...
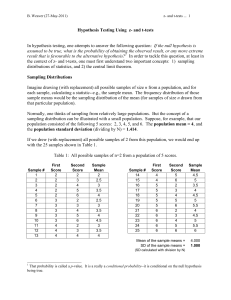
Hypothesis Testing Using z- and t-tests In hypothesis testing, one
... how t was calculated. Rather, they differed in how/where one obtained the critical value to which they compared their computed t-value. For the small-sample test, one used the critical value of t, from a table of critical t-values. For the large-sample test, one used the critical value of z, obtaine ...
... how t was calculated. Rather, they differed in how/where one obtained the critical value to which they compared their computed t-value. For the small-sample test, one used the critical value of t, from a table of critical t-values. For the large-sample test, one used the critical value of z, obtaine ...