Universal Identities I
... (2.1) implies a similar formula for sums of three squares in any commutative ring by specializing the 6 indeterminates to any 6 elements of any commutative ring. So (2.1) implies that sums of three squares are closed under multiplication in any commutative ring, but this false in Z: 3 and 5 are sums ...
... (2.1) implies a similar formula for sums of three squares in any commutative ring by specializing the 6 indeterminates to any 6 elements of any commutative ring. So (2.1) implies that sums of three squares are closed under multiplication in any commutative ring, but this false in Z: 3 and 5 are sums ...
Part-3-of-3-HS-CCSSM..
... Reasoning with Equations and Inequalities The population of a country is initially 2 million people and is increasing at 4% per year. The country's annual food supply is initially adequate for 4 million people and is increasing at a constant rate adequate for an additional 0.5 million people per ...
... Reasoning with Equations and Inequalities The population of a country is initially 2 million people and is increasing at 4% per year. The country's annual food supply is initially adequate for 4 million people and is increasing at a constant rate adequate for an additional 0.5 million people per ...
Secure Distributed Linear Algebra in a Constant Number of
... Our protocols work for arbitrary fields and do not use any cryptographic assumptions, so if the basic sharing method we start from is unconditionally secure, then so are the protocols we construct. It is easy to see that our results allow handling all functions computable in constant round and with ...
... Our protocols work for arbitrary fields and do not use any cryptographic assumptions, so if the basic sharing method we start from is unconditionally secure, then so are the protocols we construct. It is easy to see that our results allow handling all functions computable in constant round and with ...
Basic Vector Space Methods in Signal and Systems Theory
... In the next section, we will use the pseudo-inverse of So the frame bounds ...
... In the next section, we will use the pseudo-inverse of So the frame bounds ...
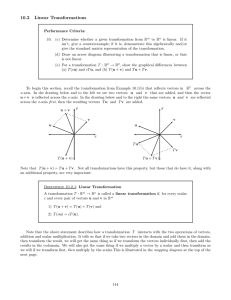
10.2 Linear Transformations
... Note that the above statement describes how a transformation T interacts with the two operations of vectors, addition and scalar multiplication. It tells us that if we take two vectors in the domain and add them in the domain, then transform the result, we will get the same thing as if we transform ...
... Note that the above statement describes how a transformation T interacts with the two operations of vectors, addition and scalar multiplication. It tells us that if we take two vectors in the domain and add them in the domain, then transform the result, we will get the same thing as if we transform ...
DM-nucleon scattering cross sections
... Trace anomaly of the energy-momentum tensor in QCD(Nf = 3) ...
... Trace anomaly of the energy-momentum tensor in QCD(Nf = 3) ...








![λ1 [ v1 v2 ] and A [ w1 w2 ] = λ2](http://s1.studyres.com/store/data/020256186_1-44523acdcc73497aa300703df377fe57-300x300.png)