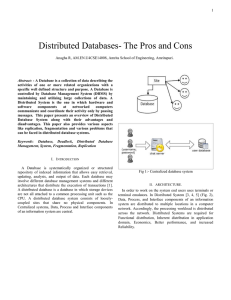
Keywords: Database, Deadlock, Distributed
... Distributed Database systems. Database Manager is software responsible forhandling a segment of the distributed database. User Request Interface is another important component of distributed database systems. It is usually a client program which acts as an interface to the Distributed Transaction Ma ...
... Distributed Database systems. Database Manager is software responsible forhandling a segment of the distributed database. User Request Interface is another important component of distributed database systems. It is usually a client program which acts as an interface to the Distributed Transaction Ma ...
Resume of SRAVAN
... different heterogeneous systems and SQL Server. Involved in creating Jobs, SQL Mail Agent, Alerts and Scheduled DTS/SSIS Packages. Adept in creating Ad-hoc, Cross-Tab, Drill-down and Sub-Report using RDL in SSRS. Experienced in creating Report Models, generating Reports for business analysis and m ...
... different heterogeneous systems and SQL Server. Involved in creating Jobs, SQL Mail Agent, Alerts and Scheduled DTS/SSIS Packages. Adept in creating Ad-hoc, Cross-Tab, Drill-down and Sub-Report using RDL in SSRS. Experienced in creating Report Models, generating Reports for business analysis and m ...
Slide 1
... We run into a big issue here. The problem is that our database replicates a lot of tables out to other databases. And when we replicate from our 11.2 database to a 9.2 database, the mview log (on the 11.2) does not get purged. But we have applied the one-off patch on the database, and the issue stil ...
... We run into a big issue here. The problem is that our database replicates a lot of tables out to other databases. And when we replicate from our 11.2 database to a 9.2 database, the mview log (on the 11.2) does not get purged. But we have applied the one-off patch on the database, and the issue stil ...
The SQL Server Database Consolidation Appliance Reference
... Provides a complete, pre-built, integrated hardware & software solution for SQL Server database consolidation • Pre-installed and configured software stack utilizing Windows Server, Hyper-V, SQL Server and System Center ...
... Provides a complete, pre-built, integrated hardware & software solution for SQL Server database consolidation • Pre-installed and configured software stack utilizing Windows Server, Hyper-V, SQL Server and System Center ...
Oracle Forensics
... PL/SQL Injection – exploiting dynamic SQL, e.g. by creating functions Trigger abuse – injection of code into triggers Cursor snarfing – access to other peoples cursors which had not been closed properly (fixed) – External procedures – EXTPROC loads libraries and executes; 12c run as designated OS cr ...
... PL/SQL Injection – exploiting dynamic SQL, e.g. by creating functions Trigger abuse – injection of code into triggers Cursor snarfing – access to other peoples cursors which had not been closed properly (fixed) – External procedures – EXTPROC loads libraries and executes; 12c run as designated OS cr ...
Chapter 8
... – A virtual table (multiple columns and rows): it can be used wherever a table is expected – Always up-to-date, because it is a query, not a real table – A view’s data is not saved to the database; rather, the SQL query for the view is executed each time it is called ...
... – A virtual table (multiple columns and rows): it can be used wherever a table is expected – Always up-to-date, because it is a query, not a real table – A view’s data is not saved to the database; rather, the SQL query for the view is executed each time it is called ...
Data mining
... Auditing Similar to OS auditing A retroactive technique to check whether improper access to database information has been obtained this allows corrective action to be taken (sometimes automated as part of audit system) it can also notify the DBA of potential security breakdowns or corrupted data and ...
... Auditing Similar to OS auditing A retroactive technique to check whether improper access to database information has been obtained this allows corrective action to be taken (sometimes automated as part of audit system) it can also notify the DBA of potential security breakdowns or corrupted data and ...
Microsoft Access 2010
... For the JOIN to happen properly… the fields have to be spelled EXACTLY alike, be the same data type, width, etc. If you still don’t have a join line.. .create one yourself… I will show you how. ...
... For the JOIN to happen properly… the fields have to be spelled EXACTLY alike, be the same data type, width, etc. If you still don’t have a join line.. .create one yourself… I will show you how. ...
Rack servers: Database price performance
... drive for quick access. We used that backup file to restore both servers between test runs. We followed these steps to create the database: 1. We created the database and file structure using database creation scripts in the DS2 download. We made size modifications specific to our 5GB database and t ...
... drive for quick access. We used that backup file to restore both servers between test runs. We followed these steps to create the database: 1. We created the database and file structure using database creation scripts in the DS2 download. We made size modifications specific to our 5GB database and t ...
Introduction to Relational Database Management Systems
... sort key, index, or key word. For example, if you sort records by age, then the age field is a key. Most database management systems allow you to have more than one key so that you can sort records in different ways. One of the keys is designated as the primary key, and must hold a unique value for ...
... sort key, index, or key word. For example, if you sort records by age, then the age field is a key. Most database management systems allow you to have more than one key so that you can sort records in different ways. One of the keys is designated as the primary key, and must hold a unique value for ...
Scaling Up with SQL Server 2008
... MOLAP partitions, which removes the performance degradation that is caused by maintaining ROLAP write-back tables. ...
... MOLAP partitions, which removes the performance degradation that is caused by maintaining ROLAP write-back tables. ...
Oracle SOA Suite - How to Integrate Databases and
... Database Adapter Overview • Enables an activity in a BPEL process to: • Poll the database at a regular interval, looking for new rows to process (“inbound”) ...
... Database Adapter Overview • Enables an activity in a BPEL process to: • Poll the database at a regular interval, looking for new rows to process (“inbound”) ...
Course Review
... Intelligent Keys : have a meaning. Longitude and Latitude of an object (say a building) uniquely identifies a building and also nominates where it is. Super Key : This is normally a key with too many attributes in it. Some of the columns could be removed and a key would still exist. A good example i ...
... Intelligent Keys : have a meaning. Longitude and Latitude of an object (say a building) uniquely identifies a building and also nominates where it is. Super Key : This is normally a key with too many attributes in it. Some of the columns could be removed and a key would still exist. A good example i ...
jdbc
... • Embedding SQL statements into a host language - Java • Opposed to a CLI to access the database - JDBC • SQLJ is similar to the ANSI/ISO embedded SQL standards for C, Fortran and other programming languages – proposed to ANSI/ISO as the SQL and Java Standard ...
... • Embedding SQL statements into a host language - Java • Opposed to a CLI to access the database - JDBC • SQLJ is similar to the ANSI/ISO embedded SQL standards for C, Fortran and other programming languages – proposed to ANSI/ISO as the SQL and Java Standard ...
Java Database Connectivity (JDBC)
... server level. The JDBC driver on the client uses sockets to call a middleware application on the server that translates the client requests into an API specific to the desired driver. ...
... server level. The JDBC driver on the client uses sockets to call a middleware application on the server that translates the client requests into an API specific to the desired driver. ...
Microsoft SQL Server
... 2. Secure MSDE installations If MSDE is distributed with application, the following additional guidance applies: Install MSDE using "Windows security mode" as the default. When distributing MSDE to customers, use the Microsoft-supplied installer rather than merge modules. When installing an instance ...
... 2. Secure MSDE installations If MSDE is distributed with application, the following additional guidance applies: Install MSDE using "Windows security mode" as the default. When distributing MSDE to customers, use the Microsoft-supplied installer rather than merge modules. When installing an instance ...
SQL Server 2016 CTP3 Technical Overview
... Database Master Key of the master Database creates a certificate in the master database ...
... Database Master Key of the master Database creates a certificate in the master database ...
A Relational Database Primer for SAS Programmers
... are the dominant vehicle for storing business information so uH~mat~ly the discussion is rhetorical. An interesting question, Included here as a sidebar, inquires after the location ofthe SAS System in the preceding spectrum. Users can index SAS datasets, can include password protection, and can use ...
... are the dominant vehicle for storing business information so uH~mat~ly the discussion is rhetorical. An interesting question, Included here as a sidebar, inquires after the location ofthe SAS System in the preceding spectrum. Users can index SAS datasets, can include password protection, and can use ...
Administering a Microsoft SQL Server 2000 Database
... • Capacity Planning • Performance Considerations The following lab is covered in this module: • Managing Database Files At the end of this module, you will be able to: • Describe how SQL Server stores data and handles transactions. • Create a database, including specifying options during and after d ...
... • Capacity Planning • Performance Considerations The following lab is covered in this module: • Managing Database Files At the end of this module, you will be able to: • Describe how SQL Server stores data and handles transactions. • Create a database, including specifying options during and after d ...
Chapter # 8 (Advanced SQL)
... converts it to actual date in Oracle format SQL Server uses CAST and CONVERT functions ...
... converts it to actual date in Oracle format SQL Server uses CAST and CONVERT functions ...
Structured Query Language
... location of the folder where the data for this source is stored. In LookoutDirect 4, it is possible to configure multiple Citadel databases. If you do so, you probably want to configure one ODBC data source for each. If you used the Options»System dialog box in LookoutDirect to configure a default C ...
... location of the folder where the data for this source is stored. In LookoutDirect 4, it is possible to configure multiple Citadel databases. If you do so, you probably want to configure one ODBC data source for each. If you used the Options»System dialog box in LookoutDirect to configure a default C ...
IPD - SQL Server - Best IT Documents
... both of these can cause performance degradation if not properly calculated. ...
... both of these can cause performance degradation if not properly calculated. ...
Accelerate and Improve Microsoft SQL Server* Database Performance
... Software and workloads used in performance tests may have been optimized for performance only on Intel microprocessors. Performance measurements in Windows*, Microsoft* SQL Server, are measured using specific computer systems, components, software, operations and functions. Any change to any of th ...
... Software and workloads used in performance tests may have been optimized for performance only on Intel microprocessors. Performance measurements in Windows*, Microsoft* SQL Server, are measured using specific computer systems, components, software, operations and functions. Any change to any of th ...
TPC Benchmarks
... Application models a wholesale supplier managing orders. Order-entry provides a conceptual model for the benchmark; underlying components are typical of any OLTP system. Workload consists of five transaction types. Users and database scale linearly with throughput. Spec defines full-screen end-user ...
... Application models a wholesale supplier managing orders. Order-entry provides a conceptual model for the benchmark; underlying components are typical of any OLTP system. Workload consists of five transaction types. Users and database scale linearly with throughput. Spec defines full-screen end-user ...
Biacore 8K Database Installation and Management Guide
... Biacore 8K software supports the use of different database servers, different databases and different types of users. Several instruments can store run data in the same database. Moving objects between databases is also supported to some extent, using import-export functionality from within the soft ...
... Biacore 8K software supports the use of different database servers, different databases and different types of users. Several instruments can store run data in the same database. Moving objects between databases is also supported to some extent, using import-export functionality from within the soft ...
Microsoft Access
Microsoft Access is a DBMS (also known as Database Management System) from Microsoft that combines the relational Microsoft Jet Database Engine with a graphical user interface and software-development tools. It is a member of the Microsoft Office suite of applications, included in the Professional and higher editions or sold separately.Microsoft Access stores data in its own format based on the Access Jet Database Engine. It can also import or link directly to data stored in other applications and databases.Software developers and data architects can use Microsoft Access to develop application software, and ""power users"" can use it to build software applications. Like other Office applications, Access is supported by Visual Basic for Applications (VBA), an object-oriented programming language that can reference a variety of objects including DAO (Data Access Objects), ActiveX Data Objects, and many other ActiveX components. Visual objects used in forms and reports expose their methods and properties in the VBA programming environment, and VBA code modules may declare and call Windows operating-system functions.