NVCC COLLEGE-WIDE COURSE CONTENT SUMMARY
... In order to standardize the core topics of ITD 256 so that a course taught at one campus is equivalent to the same course taught at another campus, the following student contact hours per topic are required. The topics do not need to be followed sequentially. Many topics are taught best as an integr ...
... In order to standardize the core topics of ITD 256 so that a course taught at one campus is equivalent to the same course taught at another campus, the following student contact hours per topic are required. The topics do not need to be followed sequentially. Many topics are taught best as an integr ...
Lecture 18 - Introduction to Distributed Databases
... – Full Replication: the entire database is replicated – Partial Replication: some selected part is replicated to some of the sites. – Data replication is achieved through a replication schema, a definition of: • all attributes and tuples in the DB; and • a sequence of UNION operations from which the ...
... – Full Replication: the entire database is replicated – Partial Replication: some selected part is replicated to some of the sites. – Data replication is achieved through a replication schema, a definition of: • all attributes and tuples in the DB; and • a sequence of UNION operations from which the ...
Database and Cloud Security
... provide, not a ‘how to’ design solution and implementation. The reference architecture is intended to facilitate the understanding of the operational intricacies in cloud computing. It does not represent the system architecture of a specific cloud computing system; instead it is a tool for describin ...
... provide, not a ‘how to’ design solution and implementation. The reference architecture is intended to facilitate the understanding of the operational intricacies in cloud computing. It does not represent the system architecture of a specific cloud computing system; instead it is a tool for describin ...
Introduction
... • Storage manager is a program module that provides the interface between the low-level data stored in the database and the application programs and queries submitted to the system. • The storage manager is responsible to the following tasks: – Interaction with the file manager – Efficient storing, ...
... • Storage manager is a program module that provides the interface between the low-level data stored in the database and the application programs and queries submitted to the system. • The storage manager is responsible to the following tasks: – Interaction with the file manager – Efficient storing, ...
MIS 2502 Access 2007 Tutorial
... Queries select records from one or more tables in a database so they can be viewed, analyzed, and sorted on a common datasheet. The resulting collection of records, called a dynaset (short for dynamic subset), is saved as a database object and can therefore be easily used in the future. The query wi ...
... Queries select records from one or more tables in a database so they can be viewed, analyzed, and sorted on a common datasheet. The resulting collection of records, called a dynaset (short for dynamic subset), is saved as a database object and can therefore be easily used in the future. The query wi ...
Best practices for packaging database applications
... database. If an automated system is to assist in such an upgrade, it should be considered as a part of the package upgrade process; failure to upgrade the database should be considered a failure to upgrade the package. This is the only way to safely guarantee the chance to reattempt the upgrade with ...
... database. If an automated system is to assist in such an upgrade, it should be considered as a part of the package upgrade process; failure to upgrade the database should be considered a failure to upgrade the package. This is the only way to safely guarantee the chance to reattempt the upgrade with ...
Define the SERVER (SYSTEM):
... Note: These instructions consider the use of Environment Manager which is installed from Cool: Plex CD and does not make part of Default Installation. o Go to: Start|Programs|Cool: Plex Application Server|Environment Manager. o Enter the SERVER (SYSTEM) and press Refresh. This will display a list of ...
... Note: These instructions consider the use of Environment Manager which is installed from Cool: Plex CD and does not make part of Default Installation. o Go to: Start|Programs|Cool: Plex Application Server|Environment Manager. o Enter the SERVER (SYSTEM) and press Refresh. This will display a list of ...
FastObjects Database Components
... FastObjects supports the Java and C++ object model. You can concentrate on your application model instead of writing mapping code. You save code (up to 40 percent less application code) and your application runs significantly faster. The more complex your model is, the greater the benefits of using ...
... FastObjects supports the Java and C++ object model. You can concentrate on your application model instead of writing mapping code. You save code (up to 40 percent less application code) and your application runs significantly faster. The more complex your model is, the greater the benefits of using ...
Integrating the Practical Use of a Database
... deliverables, which are identified later in this section, and assessment deliverables, which include group status reports, confidential evaluations (self and peer) and team assessment. The assessment consists of questions in which students must assess their understanding of the course material with ...
... deliverables, which are identified later in this section, and assessment deliverables, which include group status reports, confidential evaluations (self and peer) and team assessment. The assessment consists of questions in which students must assess their understanding of the course material with ...
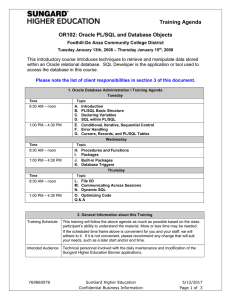
PL/SQL and Database Objects
... within an Oracle relational database. SQL Developer is the application or tool used to access the database in this course. Please note the list of client responsibilities in section 3 of this document. 1. Oracle Database Administration I Training Agenda ...
... within an Oracle relational database. SQL Developer is the application or tool used to access the database in this course. Please note the list of client responsibilities in section 3 of this document. 1. Oracle Database Administration I Training Agenda ...
Providing information on the WWW
... This example program uses PHP to talk to a MYSQL relational database The details of each step will differ between databases and languages, but will share many similarities Here we insert information from a web form into a database and retrieve an observation number for later use. ...
... This example program uses PHP to talk to a MYSQL relational database The details of each step will differ between databases and languages, but will share many similarities Here we insert information from a web form into a database and retrieve an observation number for later use. ...
L49069799
... for data access while calling. When in call process user want to access data, server need to validate it and while validation data accessing must be synchronize with mysql server. For large data accessing API is essential. This method is for HTML5 and AJAX for fast data synchronization. REST can sup ...
... for data access while calling. When in call process user want to access data, server need to validate it and while validation data accessing must be synchronize with mysql server. For large data accessing API is essential. This method is for HTML5 and AJAX for fast data synchronization. REST can sup ...
How Databases Work For Records Management Presented By Joe Gentry
... Everyone who uses Windows! Run REGEDIT.EXE some time View the Microsoft Window’s Internal Database Where Associations Are Stored Where Application Settings Are Stored Where Object Permissions Are Stored ...
... Everyone who uses Windows! Run REGEDIT.EXE some time View the Microsoft Window’s Internal Database Where Associations Are Stored Where Application Settings Are Stored Where Object Permissions Are Stored ...
Introduction to SQL Server 2000
... addition to database files, SQL Server also has backup devices, which are logical devices that map to operating system files, to physical devices such as tape drives, or even to named pipes. : Primary data files Every database has one primary data file that keeps track of all the rest of the files ...
... addition to database files, SQL Server also has backup devices, which are logical devices that map to operating system files, to physical devices such as tape drives, or even to named pipes. : Primary data files Every database has one primary data file that keeps track of all the rest of the files ...
Database System Concepts
... Example: Transfer of funds from one account to another should either complete or not happen at all Concurrent access by multiple users Uncontrolled concurrent accesses can lead to inconsistencies Example: Two people reading a balance (say 100) and updating it by withdrawing money (say 50 eac ...
... Example: Transfer of funds from one account to another should either complete or not happen at all Concurrent access by multiple users Uncontrolled concurrent accesses can lead to inconsistencies Example: Two people reading a balance (say 100) and updating it by withdrawing money (say 50 eac ...
Database System Concepts - Department of Systems Engineering
... Example: Transfer of funds from one account to another should either complete or not happen at all Concurrent access by multiple users Uncontrolled concurrent accesses can lead to inconsistencies Example: Two people reading a balance (say 100) and updating it by withdrawing money (say 50 eac ...
... Example: Transfer of funds from one account to another should either complete or not happen at all Concurrent access by multiple users Uncontrolled concurrent accesses can lead to inconsistencies Example: Two people reading a balance (say 100) and updating it by withdrawing money (say 50 eac ...
SYSTEM DATABASES CORRUPTION
... Open Setup.exe from Media -> Maintenance -> Repair. Using both approach is similar and it would perform rebuild of resource and system databases. After rebuilding Resource database, restore Master, Model and MSDB backups (if they are available). Alternate option is to COPY Resource database files ...
... Open Setup.exe from Media -> Maintenance -> Repair. Using both approach is similar and it would perform rebuild of resource and system databases. After rebuilding Resource database, restore Master, Model and MSDB backups (if they are available). Alternate option is to COPY Resource database files ...
Lecture 10 - California State University, Los Angeles
... There will be a problem similar to this on the final! The tasks are sequential, and the first one is necessarily the most difficult. It is important to do these carefully and in order, checking each step to make sure it is right. If you mess up one step, everything after it will probably be wrong. ...
... There will be a problem similar to this on the final! The tasks are sequential, and the first one is necessarily the most difficult. It is important to do these carefully and in order, checking each step to make sure it is right. If you mess up one step, everything after it will probably be wrong. ...
Advanced Relational Database Management MISM Course S17
... Take Care of Yourself Do your best to maintain a healthy lifestyle this semester by eating well, exercising, avoiding drugs and alcohol, getting enough sleep and taking some time to relax. This will help you achieve your goals and cope with stress. All of us benefit from support during times of stru ...
... Take Care of Yourself Do your best to maintain a healthy lifestyle this semester by eating well, exercising, avoiding drugs and alcohol, getting enough sleep and taking some time to relax. This will help you achieve your goals and cope with stress. All of us benefit from support during times of stru ...
Monitoring Exadata with Precise
... instead of the DB Compute Nodes. The full scans will return directly to the PGA with Offloading and this means the Buffer Cache is not affected by the BI activity. This means that the DB Compute Nodes will have much more capability to handle OLTP functionality more efficiently. ...
... instead of the DB Compute Nodes. The full scans will return directly to the PGA with Offloading and this means the Buffer Cache is not affected by the BI activity. This means that the DB Compute Nodes will have much more capability to handle OLTP functionality more efficiently. ...
Database Security
... to restrict access to the column that is confidential, apply confidential security label to the column to restrict managers' access to only the records for their department, each row can be tagged with a security label that indicates the department. write restriction for managers can be implemented ...
... to restrict access to the column that is confidential, apply confidential security label to the column to restrict managers' access to only the records for their department, each row can be tagged with a security label that indicates the department. write restriction for managers can be implemented ...
SQL Server Procedures
... The reporting site provides read access to all of the MessageStats objects. The account(s) accessing the reporting site are assigned the MessageStats_Web database role. This role has SELECT access on all tables and views and EXECUTE access to all user defined functions. This account is normally adde ...
... The reporting site provides read access to all of the MessageStats objects. The account(s) accessing the reporting site are assigned the MessageStats_Web database role. This role has SELECT access on all tables and views and EXECUTE access to all user defined functions. This account is normally adde ...
Pass4sure 70
... D: An Access database doesn't have a Windows NT account. An Access database could have a username and a password. QUESTION 5 You want to configure SQL Server to notify you by e-mail when an alert occurs. Which series of steps must you perform? A. Configure the SQL Server Agent service to log on as t ...
... D: An Access database doesn't have a Windows NT account. An Access database could have a username and a password. QUESTION 5 You want to configure SQL Server to notify you by e-mail when an alert occurs. Which series of steps must you perform? A. Configure the SQL Server Agent service to log on as t ...
Reliability and Security in Database Servers
... Distribution, consistency, and managing databases. DBMS security and access. ...
... Distribution, consistency, and managing databases. DBMS security and access. ...
Microsoft Access
Microsoft Access is a DBMS (also known as Database Management System) from Microsoft that combines the relational Microsoft Jet Database Engine with a graphical user interface and software-development tools. It is a member of the Microsoft Office suite of applications, included in the Professional and higher editions or sold separately.Microsoft Access stores data in its own format based on the Access Jet Database Engine. It can also import or link directly to data stored in other applications and databases.Software developers and data architects can use Microsoft Access to develop application software, and ""power users"" can use it to build software applications. Like other Office applications, Access is supported by Visual Basic for Applications (VBA), an object-oriented programming language that can reference a variety of objects including DAO (Data Access Objects), ActiveX Data Objects, and many other ActiveX components. Visual objects used in forms and reports expose their methods and properties in the VBA programming environment, and VBA code modules may declare and call Windows operating-system functions.