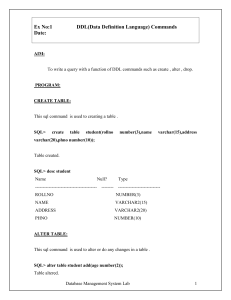
Why Unisys and MISER? - the MISER Users Group
... provides system programmers with protections against common security bugs such as buffer overruns and memory allocation problems. The system enforces memory protection, for each word of memory, by assigning tags to the memory location that describe the types of operations allowed for that particular ...
... provides system programmers with protections against common security bugs such as buffer overruns and memory allocation problems. The system enforces memory protection, for each word of memory, by assigning tags to the memory location that describe the types of operations allowed for that particular ...
Calling Stored Procedures from RulePoint
... Calling Stored Procedures from a SQL Analytic in Oracle, IBM DB2, and Microsoft SQL Server The rule validates the event conditions based on the values that an SQL analytic returns. You may want an SQL analytic to return values from a stored procedure. You can call a stored procedure from a SQL analy ...
... Calling Stored Procedures from a SQL Analytic in Oracle, IBM DB2, and Microsoft SQL Server The rule validates the event conditions based on the values that an SQL analytic returns. You may want an SQL analytic to return values from a stored procedure. You can call a stored procedure from a SQL analy ...
Modern Database Management
... create, maintain, and provide controlled access to the database and the repository. d. Database: organized collection of logically related data. e. Application programs: computer programs that are used to create and maintain the database. f. User interface: languages, menus, and other facilities by ...
... create, maintain, and provide controlled access to the database and the repository. d. Database: organized collection of logically related data. e. Application programs: computer programs that are used to create and maintain the database. f. User interface: languages, menus, and other facilities by ...
Your Database can do SAS too!
... While from the SAS users’ perspective, it’s becoming more difficult to draw the lines as in-database functionality continues to advance, it’s important that we think through the principles above when developing reporting and analytical solutions. The tendency of many of us ( certainly the author fal ...
... While from the SAS users’ perspective, it’s becoming more difficult to draw the lines as in-database functionality continues to advance, it’s important that we think through the principles above when developing reporting and analytical solutions. The tendency of many of us ( certainly the author fal ...
Introduction to GIS - University of Vermont
... A design used in database systems in which relationships are created between one or more flat files or tables based on the idea that each pair of tables has a field in common, or “key”. In a relational database, the records are generally different in each table The advantages: each table can be prep ...
... A design used in database systems in which relationships are created between one or more flat files or tables based on the idea that each pair of tables has a field in common, or “key”. In a relational database, the records are generally different in each table The advantages: each table can be prep ...
1 - WordPress.com
... database can contain all the data about an individual employee, but one group of users may be authorized to view only payroll data, while others are allowed access to only work history and medical data. If the DBMS provides a way to interactively enter and update the database, as well as interrogate ...
... database can contain all the data about an individual employee, but one group of users may be authorized to view only payroll data, while others are allowed access to only work history and medical data. If the DBMS provides a way to interactively enter and update the database, as well as interrogate ...
ADB-Lecture14-InformationRetrieval
... keyword query, and system finds other documents similar to these Vector space model: define an n-dimensional space, where n is the number of words in the document set. Vector for document d goes from origin to a point whose i th ...
... keyword query, and system finds other documents similar to these Vector space model: define an n-dimensional space, where n is the number of words in the document set. Vector for document d goes from origin to a point whose i th ...
Object-Oriented Databases - School of Information Technology
... Databases provide a common repository for data Database management systems provide sophisticated capabilities to store, retrieve, and manage data Detailed database models are derived from domain class diagrams Database models are implemented using database management systems Databases can be re ...
... Databases provide a common repository for data Database management systems provide sophisticated capabilities to store, retrieve, and manage data Detailed database models are derived from domain class diagrams Database models are implemented using database management systems Databases can be re ...
Privacy - Personal Web Pages
... No perceptible risk is incurred by joining DB Anything adversary can do to me, it could do without me (my data) ...
... No perceptible risk is incurred by joining DB Anything adversary can do to me, it could do without me (my data) ...
Data Guard
... Does not commit until redo written to at least one Standby Creates guaranteed RPO of 0 seconds – no data loss Causes potential slowness on Primary database as it has to wait for an acknowledgement from Standby ...
... Does not commit until redo written to at least one Standby Creates guaranteed RPO of 0 seconds – no data loss Causes potential slowness on Primary database as it has to wait for an acknowledgement from Standby ...
Slide 1
... • Create list of SQL Server that you want to analyze now or in the future • BPA will scan all databases on a given server (including system databases) ...
... • Create list of SQL Server that you want to analyze now or in the future • BPA will scan all databases on a given server (including system databases) ...
Proper Care and Feeding of your SQL MDB
... DBs whenever possible (default is SQL install disk) - The size of the TEMPDB database should be increased based on available disk space and expected usage - SQL Server adjusts the size incrementally over time, but each adjustment causes a performance hit - You may need to set the original size of th ...
... DBs whenever possible (default is SQL install disk) - The size of the TEMPDB database should be increased based on available disk space and expected usage - SQL Server adjusts the size incrementally over time, but each adjustment causes a performance hit - You may need to set the original size of th ...
Security Features in Teradata Database
... valid username and password as part of the logon string in order for a database session to be established. However, properly securing such password-based schemes requires that a security administrator be able to ensure that passwords are regularly changed, are sufficiently complex, and that effectiv ...
... valid username and password as part of the logon string in order for a database session to be established. However, properly securing such password-based schemes requires that a security administrator be able to ensure that passwords are regularly changed, are sufficiently complex, and that effectiv ...
Site Development Foundations
... Join -- combining two database tables to create a new table Table -- a database topic that contains rows (records) and columns (attributes or fields) Record -- one row of a relational database table Field -- one column of a relational database table Entity (i.e., record) -- a person, place or thing ...
... Join -- combining two database tables to create a new table Table -- a database topic that contains rows (records) and columns (attributes or fields) Record -- one row of a relational database table Field -- one column of a relational database table Entity (i.e., record) -- a person, place or thing ...
Aptitude Questions 1. One guy has Rs. 100/
... (B) "The date of joining is 01-JUN-1999". (The sample date fetched by the SQL stmt) (C) The code complies but results in run-time exception (D) "The date of joining is ". ( The date is null) 4. As far as handling null values in JAVA and SQL is concerned which of the following statements is wrong? ( ...
... (B) "The date of joining is 01-JUN-1999". (The sample date fetched by the SQL stmt) (C) The code complies but results in run-time exception (D) "The date of joining is ". ( The date is null) 4. As far as handling null values in JAVA and SQL is concerned which of the following statements is wrong? ( ...
Implementation Plan - Project Management
... The Microsoft SQL Server Migration Assistant for Access tool (SSMA) will be used to carry out the migration of the alerts database. It can be downloaded from https://www.microsoft.com/en-gb/download/details.aspx?id=43690 Once installed, it might be safer to run the 32-bit mode application, this shou ...
... The Microsoft SQL Server Migration Assistant for Access tool (SSMA) will be used to carry out the migration of the alerts database. It can be downloaded from https://www.microsoft.com/en-gb/download/details.aspx?id=43690 Once installed, it might be safer to run the 32-bit mode application, this shou ...
XTime Install Guide
... A pop-up message will appear indicating where the Registration file is saved to. This file needs to be sent to the licence department of Skycom who will issue a Trial licence. XTime Lite Installation Guide - V2.17.01.2 ...
... A pop-up message will appear indicating where the Registration file is saved to. This file needs to be sent to the licence department of Skycom who will issue a Trial licence. XTime Lite Installation Guide - V2.17.01.2 ...
Tools - BlueGreens
... testing of universes, reports and user and security layer; solving issues and implementing necessary changes; —scenario scripts and testing of LDW database for migration from Oracle 8i to Oracle 9i; —describing and executing migration of NT server applications to Windows 2003 Server; clean up and fr ...
... testing of universes, reports and user and security layer; solving issues and implementing necessary changes; —scenario scripts and testing of LDW database for migration from Oracle 8i to Oracle 9i; —describing and executing migration of NT server applications to Windows 2003 Server; clean up and fr ...
Chapter 13 - Emunix Documentation on the Web
... non-proprietary means to process database views – This is important for the processing of views with multiple multi-value paths ...
... non-proprietary means to process database views – This is important for the processing of views with multiple multi-value paths ...
Microsoft Jet Database Engine
The Microsoft Jet Database Engine is a database engine on which several Microsoft products have been built. A database engine is the underlying component of a database, a collection of information stored on a computer in a systematic way. The first version of Jet was developed in 1992, consisting of three modules which could be used to manipulate a database.Database connect for MicrosoftJET stands for Joint Engine Technology, sometimes being referred to as Microsoft JET Engine or simply Jet. Microsoft Access and Visual Basic use or have used Jet as their underlying database engine. It has since been superseded for general use, however, first by Microsoft Desktop Engine (MSDE), then later by SQL Server Express. For larger database needs, Jet databases can be upgraded (or, in Microsoft parlance, ""up-sized"") to Microsoft's flagship database product, SQL Server.However, this does not mean that a MS Jet (Red) database cannot match MS SQL Server in storage capacity. A 5 billion record MS Jet (Red) database with compression and encryption turned on requires about 1 terabyte of disk storage space, comprising hundreds of (*.mdb) files, each acting as partial table, and not as a database in itself.Over the years, Jet has become almost synonymous with Microsoft Access, to the extent that many people refer to a Jet database as an ""Access database"".