Lesson-C - uob.edu.bh
... Does not physically exist in the database as table Presents data in a different format from ...
... Does not physically exist in the database as table Presents data in a different format from ...
On the performance of parallel join processing in shared nothing
... system throughput. To improve response time, intra-transaction parallelism is needed either in the form of inter-DML or intra-DML parallelism. Inter-DML parallelism refers to the concurrent execution of different DML statements (queries) of the same transaction. However, the degree of parallelism ob ...
... system throughput. To improve response time, intra-transaction parallelism is needed either in the form of inter-DML or intra-DML parallelism. Inter-DML parallelism refers to the concurrent execution of different DML statements (queries) of the same transaction. However, the degree of parallelism ob ...
Question Answer
... How difficult will it be to To help make the transition seamless, the LCC Viewer interface shows screens locate information in similar to what you see in Purkinje or Health Screen. the Viewer? The following configurations were also done: The migration of the document tree to preserve the organizat ...
... How difficult will it be to To help make the transition seamless, the LCC Viewer interface shows screens locate information in similar to what you see in Purkinje or Health Screen. the Viewer? The following configurations were also done: The migration of the document tree to preserve the organizat ...
MCA I- Year I-Semester
... 1. Create a simple HTML page which demonstrates all types of lists. 2. Create a letter head of your college using following styles i. image as background ii. use header tags to format college name and address 3. Create a web page, which contains hyper links like fruits, flowers, animals. When you cl ...
... 1. Create a simple HTML page which demonstrates all types of lists. 2. Create a letter head of your college using following styles i. image as background ii. use header tags to format college name and address 3. Create a web page, which contains hyper links like fruits, flowers, animals. When you cl ...
Chapter 2 - High Point University
... When working with a table, there may not be access to the CREATE TABLE command used for the table ...
... When working with a table, there may not be access to the CREATE TABLE command used for the table ...
SQL and SAS/ACCESS Differences and Interrelationships
... PROC SOl, which Is part of base $AS software,ls the $AS System's implementation of structured query language, or SOL (pronounced 'sequel' in this paper). SOL was developed by IBM® , and has since been adopted by the American National Standards Institute (ANSI) as the standard language for relational ...
... PROC SOl, which Is part of base $AS software,ls the $AS System's implementation of structured query language, or SOL (pronounced 'sequel' in this paper). SOL was developed by IBM® , and has since been adopted by the American National Standards Institute (ANSI) as the standard language for relational ...
ppt
... E.g., a system with 100 disks, each with MTTF of 100,000 hours (approx. 11 years), will have a system MTTF of 1000 hours (approx. 41 days) Techniques for using redundancy to avoid data loss are critical with large numbers of disks Originally a cost-effective alternative to large, expensive disks ...
... E.g., a system with 100 disks, each with MTTF of 100,000 hours (approx. 11 years), will have a system MTTF of 1000 hours (approx. 41 days) Techniques for using redundancy to avoid data loss are critical with large numbers of disks Originally a cost-effective alternative to large, expensive disks ...
Data concurrency
... Transactions using the Repeatable Read isolation level can retrieve the same set of rows multiple times and perform any number of operations on them until terminated by a commit or a rollback operation; other transactions are not allowed to perform insert, update, or delete operations that will affe ...
... Transactions using the Repeatable Read isolation level can retrieve the same set of rows multiple times and perform any number of operations on them until terminated by a commit or a rollback operation; other transactions are not allowed to perform insert, update, or delete operations that will affe ...
Security Options in Oracle, the matrix of what`s
... 2. Remedial Plan – Based on the vulnerability, create a remedial plan with timelines for implementing as well as responsibilities and funding. 3. Warning – Immediately establish a department to warn of significant attacks and enhance the system for detecting and analyzing attacks. 4. Response – Have ...
... 2. Remedial Plan – Based on the vulnerability, create a remedial plan with timelines for implementing as well as responsibilities and funding. 3. Warning – Immediately establish a department to warn of significant attacks and enhance the system for detecting and analyzing attacks. 4. Response – Have ...
The Design and Implementation of a Self
... that the database could have been seriously corrupted. The execution of new transactions can be resumed only after the database is recovered for sure. In some cases, the real purpose of a data corruption attacker could be denail-of-service to good users. Besides preventive controls, a self-healing o ...
... that the database could have been seriously corrupted. The execution of new transactions can be resumed only after the database is recovered for sure. In some cases, the real purpose of a data corruption attacker could be denail-of-service to good users. Besides preventive controls, a self-healing o ...
XML-OLAP: A Multidimensional Analysis
... for decision-making [11]. It provides an analysis from multiple perspectives or dimensions for a large amount of data residing in a data warehouse. Data warehouses are commonly organized with one large fact table and multiple small dimension tables. The fact and dimension tables are typically the st ...
... for decision-making [11]. It provides an analysis from multiple perspectives or dimensions for a large amount of data residing in a data warehouse. Data warehouses are commonly organized with one large fact table and multiple small dimension tables. The fact and dimension tables are typically the st ...
PDF
... Most policy management solutions do not meet all four requirements for VoLTE. Problems include: ...
... Most policy management solutions do not meet all four requirements for VoLTE. Problems include: ...
Extensible Indexing: A Framework for Integrating Domain
... • Cartridge Developer: Defines a new indexing scheme and operators, and registers them with the database. The steps which the indextype designer is expected to undertake include providing functional implementations for user-defined operators, creating the operators, defining a type that implements t ...
... • Cartridge Developer: Defines a new indexing scheme and operators, and registers them with the database. The steps which the indextype designer is expected to undertake include providing functional implementations for user-defined operators, creating the operators, defining a type that implements t ...
Chapter 3
... Specifies that each entity e in E participates in at least min and at most max relationship instances in R Default(no constraint): min=0, max=n (signifying no limit) Must have minmax, min0, max 1 Derived from the knowledge of mini-world constraints Examples: A department has exactly one manager ...
... Specifies that each entity e in E participates in at least min and at most max relationship instances in R Default(no constraint): min=0, max=n (signifying no limit) Must have minmax, min0, max 1 Derived from the knowledge of mini-world constraints Examples: A department has exactly one manager ...
Fundamentals of Database Development (with Delphi)
... type of database is a Word document or a simple .ini file. To access an .ini file we generally use routines and techniques for typed or untyped files. Building a modern database application requires us to think of data in a relational way. The basic idea behind the relational model is that a databas ...
... type of database is a Word document or a simple .ini file. To access an .ini file we generally use routines and techniques for typed or untyped files. Building a modern database application requires us to think of data in a relational way. The basic idea behind the relational model is that a databas ...
Chapter 14: Concurrency Control
... Rigorous two-phase locking is even stricter: here all locks are ...
... Rigorous two-phase locking is even stricter: here all locks are ...
DESIGN AND IMPLEMENTATION OF THE LOST AND FOUND WEB
... This chapter presents the match engine. Topics that are discussed here include reason why the engine was created, the problem that it solves, other possible approach es to solving the same or similar problems and why there were not chosen for this project, the theory behind the implementation of the ...
... This chapter presents the match engine. Topics that are discussed here include reason why the engine was created, the problem that it solves, other possible approach es to solving the same or similar problems and why there were not chosen for this project, the theory behind the implementation of the ...
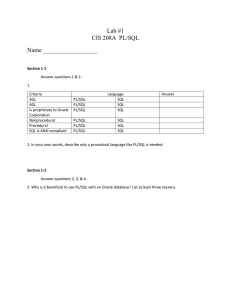
Lab Assignment # 1
... 2. Which of the following PL/SQL blocks executes successfully? For the blocks that fail, explain why they fail A. BEGIN END; B. DECLARE ...
... 2. Which of the following PL/SQL blocks executes successfully? For the blocks that fail, explain why they fail A. BEGIN END; B. DECLARE ...
1 AND 1=1
... 1 AND (select count(*) FROM sysusers as sys1, sys2, sysusers as sys2, sysusers as sys3, sysusers as sys4, sysusers as sys5, sysusers as sys6, sysusers as sys7, sysusers as sys8)> 0 AND 52 < (select top 1 ASCII(substring(name,1,1)) from sysusers) Suitable for databases that do not support time de ...
... 1 AND (select count(*) FROM sysusers as sys1, sys2, sysusers as sys2, sysusers as sys3, sysusers as sys4, sysusers as sys5, sysusers as sys6, sysusers as sys7, sysusers as sys8)> 0 AND 52 < (select top 1 ASCII(substring(name,1,1)) from sysusers) Suitable for databases that do not support time de ...
E - Read
... estimating the size of the resultant relations produced by the operation p, according to statistics in the catalog about the relations on which the operation is conducted ...
... estimating the size of the resultant relations produced by the operation p, according to statistics in the catalog about the relations on which the operation is conducted ...
ch12new
... take the n(search-key value, pointer) pairs (including the one being inserted) in sorted order. Place the first n/2 in the original node, and the rest in a new node. let the new node be p, and let k be the least key value in p. Insert (k,p) in the parent of the node being split. If the paren ...
... take the n(search-key value, pointer) pairs (including the one being inserted) in sorted order. Place the first n/2 in the original node, and the rest in a new node. let the new node be p, and let k be the least key value in p. Insert (k,p) in the parent of the node being split. If the paren ...
INTRODUCTION TO THE ACCESS DATABASE Keeping student
... • update the data once you've collected them, by adding or deleting records and by changing existing records; An electronic filing cabinet such as a database allows you also to easily and quickly use the data--sort them, create reports, merge the data with other documents, and so forth. How is a dat ...
... • update the data once you've collected them, by adding or deleting records and by changing existing records; An electronic filing cabinet such as a database allows you also to easily and quickly use the data--sort them, create reports, merge the data with other documents, and so forth. How is a dat ...
PPT
... 1. Use index on dept_name to find instructors with department name Finance; test salary = 80000 2. Use index on salary to find instructors with a salary of $80000; test dept_name = “Finance”. 3. Use dept_name index to find pointers to all records pertaining to the “Finance” department. Similarly use ...
... 1. Use index on dept_name to find instructors with department name Finance; test salary = 80000 2. Use index on salary to find instructors with a salary of $80000; test dept_name = “Finance”. 3. Use dept_name index to find pointers to all records pertaining to the “Finance” department. Similarly use ...
chapter 3
... complex Many-to-many relationship More flexible but doesn’t support ad hoc requests well ...
... complex Many-to-many relationship More flexible but doesn’t support ad hoc requests well ...
Database model

A database model is a type of data model that determines the logical structure of a database and fundamentally determines in which manner data can be stored, organized, and manipulated. The most popular example of a database model is the relational model, which uses a table-based format.