Extracting UML/OCL Integrity Constraints and Derived Types from Relational Databases
... Relational databases play a key role in most organizations storing the data they need for their business operations. To make sure the data is consistent, a set of integrity constraints is defined as part of the database schema. These constraints must be obviously aligned with the organizational poli ...
... Relational databases play a key role in most organizations storing the data they need for their business operations. To make sure the data is consistent, a set of integrity constraints is defined as part of the database schema. These constraints must be obviously aligned with the organizational poli ...
slides - Johns Hopkins University
... Input queries pre-processed into a key-value dictionary Keys are z-index values of data atoms stored in DB Entries are lists of queries Temp table is created out of dictionary keys ...
... Input queries pre-processed into a key-value dictionary Keys are z-index values of data atoms stored in DB Entries are lists of queries Temp table is created out of dictionary keys ...
Document
... Once database has been populated, users can query the data A data manipulation language controls how the user can specify queries, (and thus what types of queries are allowed) ...
... Once database has been populated, users can query the data A data manipulation language controls how the user can specify queries, (and thus what types of queries are allowed) ...
Study of Proposed System - Academic Science,International Journal
... and IBM DB2. There are different data models among which RDBMS is a common choice for the storage of information in new databases used for financial records, manufacturing and logistical information, personnel data, and other applications since the 1980s. Relational databases have often replaced hie ...
... and IBM DB2. There are different data models among which RDBMS is a common choice for the storage of information in new databases used for financial records, manufacturing and logistical information, personnel data, and other applications since the 1980s. Relational databases have often replaced hie ...
Chapter-3
... in an intuitive way so that the user can easily see and enter the data. Structured Query Language (SQL): is the most common language used to interface with databases Query by example (QBE): it enables us to fill out a grid, or template, in order to construct a sample data we would like to see. ...
... in an intuitive way so that the user can easily see and enter the data. Structured Query Language (SQL): is the most common language used to interface with databases Query by example (QBE): it enables us to fill out a grid, or template, in order to construct a sample data we would like to see. ...
Database Security
... authentication of a computer, document, or webpage. Then, a third party such as Equifax certifies that the document is legal or illegal. ...
... authentication of a computer, document, or webpage. Then, a third party such as Equifax certifies that the document is legal or illegal. ...
ADBC_plugin.pdf
... The Acrobat Database Connectivity (ADBC) plug-in provides some basic JavaScript properties and methods for connecting to a database. These can be used to obtain information about the databases available on the system, the tables contained within each database and the data types used within any given ...
... The Acrobat Database Connectivity (ADBC) plug-in provides some basic JavaScript properties and methods for connecting to a database. These can be used to obtain information about the databases available on the system, the tables contained within each database and the data types used within any given ...
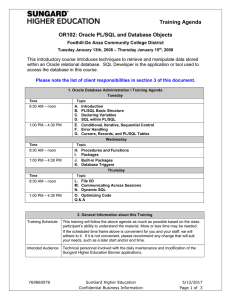
PL/SQL and Database Objects
... M. Communicating Across Sessions N. Dynamic SQL O. Optimizing Code Q&A ...
... M. Communicating Across Sessions N. Dynamic SQL O. Optimizing Code Q&A ...
Database
... coordinating and monitoring its use aquiring software and hardware as needed solving problems such as breach of security or poor system performance ...
... coordinating and monitoring its use aquiring software and hardware as needed solving problems such as breach of security or poor system performance ...
R-GMA - SNS Courseware
... R-GMA can survive loads of around 20% of the current CMS requirements and does provides a grid method for monitoring. An overload of a factor 2 jobs causes ...
... R-GMA can survive loads of around 20% of the current CMS requirements and does provides a grid method for monitoring. An overload of a factor 2 jobs causes ...
Sample pages 1 PDF
... query is formulated. The relational algebra is procedural in that the user is expected to specify, using certain high-level operators, how the result is to be obtained. The relational calculus, on the other hand, is non-procedural; the user only specifies the relationships that should hold in the re ...
... query is formulated. The relational algebra is procedural in that the user is expected to specify, using certain high-level operators, how the result is to be obtained. The relational calculus, on the other hand, is non-procedural; the user only specifies the relationships that should hold in the re ...
Polaris: A System for Query, Analysis, and Visualization of
... Excel Pivot tables provide a simple interface for building text-based tables Graphs require multiple steps: different interfaces and conceptual models Want to unify tables, graphs, and database queries in one interface ...
... Excel Pivot tables provide a simple interface for building text-based tables Graphs require multiple steps: different interfaces and conceptual models Want to unify tables, graphs, and database queries in one interface ...
ActiveObjects
... that 99% of use-cases do not call for such extreme measures. If your project does require such complex behavior within your ORM, you should be using Hibernate. It’s as simple as that. ActiveObjects is not intended to supplant Hibernate. Rather, its goal is to be an easier and lighter alternative for ...
... that 99% of use-cases do not call for such extreme measures. If your project does require such complex behavior within your ORM, you should be using Hibernate. It’s as simple as that. ActiveObjects is not intended to supplant Hibernate. Rather, its goal is to be an easier and lighter alternative for ...
Difference between Windows Authentication and SQL
... What are the different roles in SQL Server? You have a client who needs to be able execute stored procedure. What kind of permission does the user need? Serveradmin role & DDL (Data Definition Language) Database role DDL Commands are: Create, delete, What is custom role or user defined role? How to ...
... What are the different roles in SQL Server? You have a client who needs to be able execute stored procedure. What kind of permission does the user need? Serveradmin role & DDL (Data Definition Language) Database role DDL Commands are: Create, delete, What is custom role or user defined role? How to ...
Jerry Held - UML软件工程组织
... • Three sets of static views • Distinguished by their scope: – DBA: What is in all the schemas – ALL: What the user can access – USER: What is in the user’s schema ...
... • Three sets of static views • Distinguished by their scope: – DBA: What is in all the schemas – ALL: What the user can access – USER: What is in the user’s schema ...
UNDERSTANDING DATABASE DESIGN for Beginners
... • An logical entity (or physical table) is in first normal form if there are no attributes (fields) that can have more than one value for a single instance (record). • An logical entity (or physical table) is in second normal form if it is already in first normal form and if the values of all non-pr ...
... • An logical entity (or physical table) is in first normal form if there are no attributes (fields) that can have more than one value for a single instance (record). • An logical entity (or physical table) is in second normal form if it is already in first normal form and if the values of all non-pr ...
Introduction to Databases - Department of Software and Information
... Subject S is allowed to write object O only if class(S) <= class (O) ...
... Subject S is allowed to write object O only if class(S) <= class (O) ...
Chapter – 3 Introduction to Data Base Management System DEPT. OF INFORMATION
... nearly every master file record will be affected. The data is collected over a period of time, then input and verified by clerks (verified means input by someone else and then both inputs are compared by computer) and processed centrally. The transactions are entered in batches by keyboard and store ...
... nearly every master file record will be affected. The data is collected over a period of time, then input and verified by clerks (verified means input by someone else and then both inputs are compared by computer) and processed centrally. The transactions are entered in batches by keyboard and store ...
DB Lesson 2 - Tea Drinker :: Novice Blogger
... All: will be able to add data into a multi-user database Most: will have modified an existing query Some: will have written their own query from scratch. ...
... All: will be able to add data into a multi-user database Most: will have modified an existing query Some: will have written their own query from scratch. ...
Venn Diagrams
... Query Mechanism: Pick a Supplier. Look at every row in the Supplies table and if you fail to see that Supplier even once then consider that Supplier as part of the answer set. Then move on to a new Supplier. So instead of selecting members of the answer set looking at rows one at a time (which is wh ...
... Query Mechanism: Pick a Supplier. Look at every row in the Supplies table and if you fail to see that Supplier even once then consider that Supplier as part of the answer set. Then move on to a new Supplier. So instead of selecting members of the answer set looking at rows one at a time (which is wh ...
SIGMOD 2006: Effective Keyword Search in Relational Databases
... Effective Keyword Search in Relational Databases Fang Liu (University of Illinois at Chicago) Clement Yu (University of Illinois at Chicago) ...
... Effective Keyword Search in Relational Databases Fang Liu (University of Illinois at Chicago) Clement Yu (University of Illinois at Chicago) ...
Normalization
... Boyce-Codd Normal Form (BCNF) – A relation is in BCNF if every determinant is a candidate key “I swear to construct my tables so that all nonkey columns are dependent on the key, the whole key and nothing but the key, so help me Codd.” Kroenke, Database Processing ...
... Boyce-Codd Normal Form (BCNF) – A relation is in BCNF if every determinant is a candidate key “I swear to construct my tables so that all nonkey columns are dependent on the key, the whole key and nothing but the key, so help me Codd.” Kroenke, Database Processing ...
presentation source
... • represented by tables (like spreadsheets) • tables are linked with software pointers • unlike earlier systems, all three types of relationships can be represented • accommodates the design of larger databases that involve complex relationships and intricate manipulations ...
... • represented by tables (like spreadsheets) • tables are linked with software pointers • unlike earlier systems, all three types of relationships can be represented • accommodates the design of larger databases that involve complex relationships and intricate manipulations ...
GSoC 2016 Application Organization: TARDIS
... The scheme is trivial except for the AtomicQuantities table. This table establishes the one-to-many relationship between an atom and its quantities. The AtomicWeights table is a subset table of the AtomicQuantities. It represents the special type of quantities related to atoms - atomic weights. The ...
... The scheme is trivial except for the AtomicQuantities table. This table establishes the one-to-many relationship between an atom and its quantities. The AtomicWeights table is a subset table of the AtomicQuantities. It represents the special type of quantities related to atoms - atomic weights. The ...
Relational model
The relational model for database management is an approach to managing data using a structure and language consistent with first-order predicate logic, first described in 1969 by Edgar F. Codd. In the relational model of a database, all data is represented in terms of tuples, grouped into relations. A database organized in terms of the relational model is a relational database.The purpose of the relational model is to provide a declarative method for specifying data and queries: users directly state what information the database contains and what information they want from it, and let the database management system software take care of describing data structures for storing the data and retrieval procedures for answering queries.Most relational databases use the SQL data definition and query language; these systems implement what can be regarded as an engineering approximation to the relational model. A table in an SQL database schema corresponds to a predicate variable; the contents of a table to a relation; key constraints, other constraints, and SQL queries correspond to predicates. However, SQL databases deviate from the relational model in many details, and Codd fiercely argued against deviations that compromise the original principles.