slides - Indico
... In preparation for data taking, the ATLAS experiment has run a series of large-scale computational exercises to test and validate multi-tier distributed data grid solutions under development Real experience in prototypes and production systems was collected with three ATLAS major database applic ...
... In preparation for data taking, the ATLAS experiment has run a series of large-scale computational exercises to test and validate multi-tier distributed data grid solutions under development Real experience in prototypes and production systems was collected with three ATLAS major database applic ...
Slide 1
... Sys.Database_Mirroring Sys.Database_Mirroring_Endpoints Sys.DM_DB_Mirroring_Connections Sp_DbmMonitorResults ...
... Sys.Database_Mirroring Sys.Database_Mirroring_Endpoints Sys.DM_DB_Mirroring_Connections Sp_DbmMonitorResults ...
Document
... time in each of our solutions is only one order higher than that in the best nonprivacy-preserving data mining algorithms. Since both data and computing work are outsourced to the cloud servers, the resource consumption at the data owner end is very low. ...
... time in each of our solutions is only one order higher than that in the best nonprivacy-preserving data mining algorithms. Since both data and computing work are outsourced to the cloud servers, the resource consumption at the data owner end is very low. ...
Course: Database Management Systems Credits: 3
... Storage management: how secondary storage is used effectively to hold data and allow it to be accessed quickly Query processing: how queries expressed in a very high-level language such as SQL can be executed efficiently Transaction management: how to support transactions. ...
... Storage management: how secondary storage is used effectively to hold data and allow it to be accessed quickly Query processing: how queries expressed in a very high-level language such as SQL can be executed efficiently Transaction management: how to support transactions. ...
Pass4sure 190
... A. Designers can enable SCT through the properties of the New Database Info tab. B. Databases that use an SCT-enabled template do not need to store their design elements, but they must retrieve them from the template instead. C. SCT reduces the drain on server resources, storage, and memory. D. A da ...
... A. Designers can enable SCT through the properties of the New Database Info tab. B. Databases that use an SCT-enabled template do not need to store their design elements, but they must retrieve them from the template instead. C. SCT reduces the drain on server resources, storage, and memory. D. A da ...
McAfee Database User Identifier
... Capture All Data Needed for Accurate Identification In capturing every user action, as well as user details, such as the URL, client ID, and client IP, McAfee Database User Identifier not only brings your organization into sync with corporate policies that require authorization based on the identity ...
... Capture All Data Needed for Accurate Identification In capturing every user action, as well as user details, such as the URL, client ID, and client IP, McAfee Database User Identifier not only brings your organization into sync with corporate policies that require authorization based on the identity ...
Data Mining
... Preprocessing (Pre-Mining 2) : Cleanse data. Transformation (Pre-Mining 3): Convert to common format. Transform to new format. Data Mining: Obtain desired results. Interpretation/Evaluation (Post-Mining): Present results to user in meaningful manner. ...
... Preprocessing (Pre-Mining 2) : Cleanse data. Transformation (Pre-Mining 3): Convert to common format. Transform to new format. Data Mining: Obtain desired results. Interpretation/Evaluation (Post-Mining): Present results to user in meaningful manner. ...
Adaptive Cluster Distance Bounding for High
... from databases (see [1] for more details). The size of these databases can range from the ...
... from databases (see [1] for more details). The size of these databases can range from the ...
Toward the Universal Database: U-forms and the
... across many diverse devices. This stipulation implies the need for a high level of data liquidity, that is, the ability for data to flow readily from venue to venue. Each computing device and each physical location represents such a venue. Since no single venue could possibly hope to accumulate more ...
... across many diverse devices. This stipulation implies the need for a high level of data liquidity, that is, the ability for data to flow readily from venue to venue. Each computing device and each physical location represents such a venue. Since no single venue could possibly hope to accumulate more ...
Database Edition for Oracle Performance
... • Are you using file systems or raw disk partitions to Oracle data? ...
... • Are you using file systems or raw disk partitions to Oracle data? ...
Microsoft Office 2013 Microsoft Access-Intro 103-141
... 1 USB drive (purchased separately) unless your instructor advises differently ...
... 1 USB drive (purchased separately) unless your instructor advises differently ...
Lecture Notes
... Relational Databases • Relational databases are the most prevalent type of database used. • Information is organized into related tables. • Each table captures information about a different entity. – Columns are different fields of information (attributes of the entity). – Each row represents one i ...
... Relational Databases • Relational databases are the most prevalent type of database used. • Information is organized into related tables. • Each table captures information about a different entity. – Columns are different fields of information (attributes of the entity). – Each row represents one i ...
Design and Development of Land Resources Information System of
... access interface services the internal and external users with service response protocols. ...
... access interface services the internal and external users with service response protocols. ...
ENACh01final_Introduction
... maintain database applications (called “Actors on the Scene”), and Those who design and develop the DBMS software and related tools, and the computer systems operators (called “Workers Behind the ...
... maintain database applications (called “Actors on the Scene”), and Those who design and develop the DBMS software and related tools, and the computer systems operators (called “Workers Behind the ...
ThesisPresentation1 - California State University, Los Angeles
... In case of dynamic group, proposed schema solves database re-encryption problem in the event when group membership changes dynamically. It efficiently solves the security problems: data confidentiality and owner privacy. ...
... In case of dynamic group, proposed schema solves database re-encryption problem in the event when group membership changes dynamically. It efficiently solves the security problems: data confidentiality and owner privacy. ...
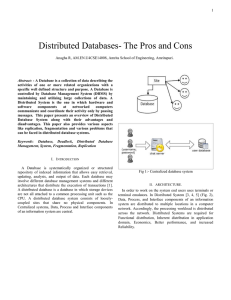
Keywords: Database, Deadlock, Distributed
... Distributed Database Systems are broadly classified into two types: i) Homogeneous Distributed System - In Homogenous distributed database system, the data is distributed but all servers run the same Database Management System (DBMS) software ii) Heterogeneous Distributed System–In Heterogeneous dis ...
... Distributed Database Systems are broadly classified into two types: i) Homogeneous Distributed System - In Homogenous distributed database system, the data is distributed but all servers run the same Database Management System (DBMS) software ii) Heterogeneous Distributed System–In Heterogeneous dis ...
Document
... • Most of the actions you need to perform on a database are done with SQL statements. • Ex: select all the records in the "Person" table. SELECT * FROM Person ...
... • Most of the actions you need to perform on a database are done with SQL statements. • Ex: select all the records in the "Person" table. SELECT * FROM Person ...
No Slide Title - Microsoft Research
... Laguna Beech Extract of the important and unimportant topics Bernstein DeWitt Gawlick Gray Maier Schek Stonebraker Hans-J. Schek, Institute of Information Systems ETH Zürich and UMIT Innsbruck ...
... Laguna Beech Extract of the important and unimportant topics Bernstein DeWitt Gawlick Gray Maier Schek Stonebraker Hans-J. Schek, Institute of Information Systems ETH Zürich and UMIT Innsbruck ...
Database_EN_2011
... DATABASE SERVER • A database server is a computer program that provides database services to other computer programs or computers, as defined by the client-server model. The term may also refer to a computer dedicated to running such a program. Database management systems frequently provide databas ...
... DATABASE SERVER • A database server is a computer program that provides database services to other computer programs or computers, as defined by the client-server model. The term may also refer to a computer dedicated to running such a program. Database management systems frequently provide databas ...