Module_5_Sample_Test_2
... Move the date from the bottom to the top of the Products report. Do not obscure any other objects in the report. ...
... Move the date from the bottom to the top of the Products report. Do not obscure any other objects in the report. ...
answers - shilepsky.net
... Closed book, single session. Omit 25 points. You may do all or parts of this in Word and/or Actrix on this exam and email it/them back to me. Leave anything done by hand in my office and email me when you have finished. 1. (5 points) In the architecture of a database system, describe what each level ...
... Closed book, single session. Omit 25 points. You may do all or parts of this in Word and/or Actrix on this exam and email it/them back to me. Leave anything done by hand in my office and email me when you have finished. 1. (5 points) In the architecture of a database system, describe what each level ...
X-Data: Test Data Generation for Killing SQL Mutants
... A dataset kills a mutant if query and the mutant give different results on the dataset A dataset is considered complete if it can kill all non-equivalent mutants of the given query Prior work: Tuya and Suarez-Cabal [IST07], Chan et al. [QSIC05] defined a class of SQL query mutations Shortc ...
... A dataset kills a mutant if query and the mutant give different results on the dataset A dataset is considered complete if it can kill all non-equivalent mutants of the given query Prior work: Tuya and Suarez-Cabal [IST07], Chan et al. [QSIC05] defined a class of SQL query mutations Shortc ...
Connection Object - Pearson Education
... XML Documents • XML can be used to present any kind of information in a simple, structured format. The following are the parts of an XML document: An XML document begins with a declaration tag. The second component in an XML document is called an element. An element is re ...
... XML Documents • XML can be used to present any kind of information in a simple, structured format. The following are the parts of an XML document: An XML document begins with a declaration tag. The second component in an XML document is called an element. An element is re ...
database
... ◦ IBM’s DB2, Microsoft’s SQL Server, and Oracle are examples of enterprise DBMS products. © 2007 Prentice Hall, Inc. ...
... ◦ IBM’s DB2, Microsoft’s SQL Server, and Oracle are examples of enterprise DBMS products. © 2007 Prentice Hall, Inc. ...
cos346day20
... When an Oracle database is created, two special user accounts named SYS and SYSTEM are created. The user account SYS is the owner of all base tables and user-accessible views in the data dictionary. The security of the SYS account is quite tight and only DBAs can access this account. During database ...
... When an Oracle database is created, two special user accounts named SYS and SYSTEM are created. The user account SYS is the owner of all base tables and user-accessible views in the data dictionary. The security of the SYS account is quite tight and only DBAs can access this account. During database ...
Document
... Application Scalability In the past clustered databases scaled well for specific types of applications ...
... Application Scalability In the past clustered databases scaled well for specific types of applications ...
DataRepresenting_by_YueLu102
... – How to represent SQL datatypes as fields – How to represent tuples as records – How to represent collections or records in blocks of memory – How to represent and store relations as collections of blocks – How to cope with record sizes – What if the size of a record changes due to updating ...
... – How to represent SQL datatypes as fields – How to represent tuples as records – How to represent collections or records in blocks of memory – How to represent and store relations as collections of blocks – How to cope with record sizes – What if the size of a record changes due to updating ...
MAA / Data Guard 12c Setup Guide Creating a RAC Physical
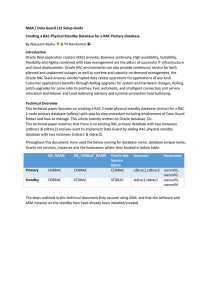
... there will be no more services registered with the listener and hence by setting, we can escape from “ORA-12514: TNS:listener does not currently know of service requested in connect descriptor” and Oracle can perform bounce of standby system safely. 10. Login to one of the RAC physical standby datab ...
... there will be no more services registered with the listener and hence by setting, we can escape from “ORA-12514: TNS:listener does not currently know of service requested in connect descriptor” and Oracle can perform bounce of standby system safely. 10. Login to one of the RAC physical standby datab ...
Lecture notes
... Solution: Periodic reconstruction of the materialized view, which is otherwise “out of date.” ...
... Solution: Periodic reconstruction of the materialized view, which is otherwise “out of date.” ...
Methodological notes
... (https://www.czso.cz/csu/czso/databaze-demografickych-udaju-za-obce-cr). The source publications always presented a table with basic demographic data not only for the whole republic (Protectorate of Bohemia and Moravia) but also for the partial territories (regions, districts (legal, administrative) ...
... (https://www.czso.cz/csu/czso/databaze-demografickych-udaju-za-obce-cr). The source publications always presented a table with basic demographic data not only for the whole republic (Protectorate of Bohemia and Moravia) but also for the partial territories (regions, districts (legal, administrative) ...
Dell XC630 web-scale hyperconverged appliance
... An integrated infrastructure can improve upon the traditional approach by bringing servers, storage, networking, and software together into a single unified package; this can streamline some management challenges and reduce costs. That said, an integrated approach is largely a pre-validated packagin ...
... An integrated infrastructure can improve upon the traditional approach by bringing servers, storage, networking, and software together into a single unified package; this can streamline some management challenges and reduce costs. That said, an integrated approach is largely a pre-validated packagin ...
Computer Sciences at the University of Tampere
... relationships between classes. • However, the associations are typically used for navigation. • In a database-driven application, this may be a big mistake! ...
... relationships between classes. • However, the associations are typically used for navigation. • In a database-driven application, this may be a big mistake! ...
PPT
... obtain < sid, bib> by projecting fro Reserves. We can first partition by scanning Reserves to obtain < sid, bid> pairs and than sort these pairs using < sid, bid > as sort key. Sorting is very important operation in database systems. Sorting a table typically requires two or three passes, each of wh ...
... obtain < sid, bib> by projecting fro Reserves. We can first partition by scanning Reserves to obtain < sid, bid> pairs and than sort these pairs using < sid, bid > as sort key. Sorting is very important operation in database systems. Sorting a table typically requires two or three passes, each of wh ...
Oracle RAC Installation
... reconnected to another system – Applications and queries continue uninterrupted – Login context maintained ...
... reconnected to another system – Applications and queries continue uninterrupted – Login context maintained ...
Incremental Updates VS Full Reload
... Companies usually move changed data from source to target by performing extracts and loads. This approach often involves custom programming, monitoring and moving an entire data volume. The CONNX® DataSync tool solves theses issues with its point-and-click interface and pre-programmed selections. Ta ...
... Companies usually move changed data from source to target by performing extracts and loads. This approach often involves custom programming, monitoring and moving an entire data volume. The CONNX® DataSync tool solves theses issues with its point-and-click interface and pre-programmed selections. Ta ...
Answers to Selected Questions and Problems
... 8. Databases can be classified according to the number of uses supported: single-user, desktop, multiuser, workgroup, and enterprise databases. According to data distribution, a database can be classified as centralized and distributed. According to its intended use, databases can be classified as o ...
... 8. Databases can be classified according to the number of uses supported: single-user, desktop, multiuser, workgroup, and enterprise databases. According to data distribution, a database can be classified as centralized and distributed. According to its intended use, databases can be classified as o ...
Databases and Data Warehouses
... • Understand how data modeling and design creates a conceptual blueprint of a database • Discuss how databases are used on the Web • List the operations involved in transferring data from transactional databases to data warehouses ...
... • Understand how data modeling and design creates a conceptual blueprint of a database • Discuss how databases are used on the Web • List the operations involved in transferring data from transactional databases to data warehouses ...
Chapter 7: Relational Database Design
... allows data to be manipulated directly from the programming language No need to go through SQL. No need for explicit storage format changes format changes are carried out transparently by system Without a persistent programming language, format changes becomes a burden on the programmer ...
... allows data to be manipulated directly from the programming language No need to go through SQL. No need for explicit storage format changes format changes are carried out transparently by system Without a persistent programming language, format changes becomes a burden on the programmer ...
A Three Level Tree Structure Database Architecture for Global
... VLR which is serving the terminal. Then the called HLR sends request to the MSC to get the routing address. Thereby MSC generated a temporarily based local directory number in the mobile terminal which is sent back and referred to as HLR. This called HLR sends the information to the so called MSC an ...
... VLR which is serving the terminal. Then the called HLR sends request to the MSC to get the routing address. Thereby MSC generated a temporarily based local directory number in the mobile terminal which is sent back and referred to as HLR. This called HLR sends the information to the so called MSC an ...
V. Inference Control Schemes in Multilevel
... Mandatory Access Control is enforced by the RDBMS itself. The database tables are stored in operating objects like files and labeled with its security level. A table within the database may contain row of different security levels. Such rows have security levels stored along with the rows in the tab ...
... Mandatory Access Control is enforced by the RDBMS itself. The database tables are stored in operating objects like files and labeled with its security level. A table within the database may contain row of different security levels. Such rows have security levels stored along with the rows in the tab ...
Vblock Specialized Systems for High Performance Databases
... adding solid-state storage to your existing infrastructure will not solve the problem. Designing a high performance database that meets the demands of today’s business can be a daunting task and few organizations have the expertise or the time to accomplish this in-house. The Vblock Specialized Syst ...
... adding solid-state storage to your existing infrastructure will not solve the problem. Designing a high performance database that meets the demands of today’s business can be a daunting task and few organizations have the expertise or the time to accomplish this in-house. The Vblock Specialized Syst ...