Fundamentals Of Database Systems
... Part 2: Relational Model, Languages, and Systems..............................................................................163 Chapter 7: The Relational Data Model, Relational Constraints, and the Relational Algebra...........163 7.1 Relational Model Concepts ..................................... ...
... Part 2: Relational Model, Languages, and Systems..............................................................................163 Chapter 7: The Relational Data Model, Relational Constraints, and the Relational Algebra...........163 7.1 Relational Model Concepts ..................................... ...
(PPT, 382KB)
... hierarchical groupings are needed or if there are meaningful textual descriptions for periods of time within the day (ex. “evening rush” or “first shift”). ...
... hierarchical groupings are needed or if there are meaningful textual descriptions for periods of time within the day (ex. “evening rush” or “first shift”). ...
Oracle9i Automatic Undo Management and Flashback Query
... hold data for up to 5 days (of instance uptime) and is persistent across startups SCN is used to reconstruct past data from Undo segments ...
... hold data for up to 5 days (of instance uptime) and is persistent across startups SCN is used to reconstruct past data from Undo segments ...
Migrating from Oracle . . . to IBM Informix Dynamic Server
... 9.2.1 Backup and restore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287 9.2.2 Fast recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289 9.2.3 Mirroring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... 9.2.1 Backup and restore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287 9.2.2 Fast recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289 9.2.3 Mirroring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Handling of NULL Values in Preference Database Queries
... For example, in a hiking tour database (cp. Table 1) it is highly unlikely that all data for all attributes of a tour are always known. The column length contains two NULL entries, because it was not possible to determine the length of the tours. Furthermore users may fill a global database with the ...
... For example, in a hiking tour database (cp. Table 1) it is highly unlikely that all data for all attributes of a tour are always known. The column length contains two NULL entries, because it was not possible to determine the length of the tours. Furthermore users may fill a global database with the ...
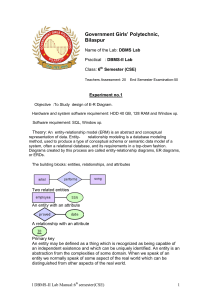
l DBMS-II Lab Manual
... key any subset of a relation is called key. super key a key is called super key if it is sufficient to identify a unique tuple of a relation. candidate key a minimal super key is called candidate key i.e no proper subset of a candidate key is super key. primary key a candidate key chosen as a princi ...
... key any subset of a relation is called key. super key a key is called super key if it is sufficient to identify a unique tuple of a relation. candidate key a minimal super key is called candidate key i.e no proper subset of a candidate key is super key. primary key a candidate key chosen as a princi ...
Operations Guide
... Information in this document is subject to change without notice. Revisions may be issued to advise of such changes and additions. Embarcadero Technologies, Inc. does not warrant that this documentation is error-free. ...
... Information in this document is subject to change without notice. Revisions may be issued to advise of such changes and additions. Embarcadero Technologies, Inc. does not warrant that this documentation is error-free. ...
ASE 15.7 - Performance and Tuning Series: Physical Database Tuning
... Information in this document is subject to change without notice. The software described herein is furnished under a license agreement, and it may be used or copied only in accordance with the terms of that agreement. To order additional documents, U.S. and Canadian customers should call Customer Fu ...
... Information in this document is subject to change without notice. The software described herein is furnished under a license agreement, and it may be used or copied only in accordance with the terms of that agreement. To order additional documents, U.S. and Canadian customers should call Customer Fu ...
cs610a - Arms-A-Flailing | Contain Yourself!
... – specify information content (use DDL) to create database systems Application developers – design and develop applications that extend the functionality of the dbms. E.g. user interface, data analysis and data mining, various business services Database administrators (DBAs) – administer databases: ...
... – specify information content (use DDL) to create database systems Application developers – design and develop applications that extend the functionality of the dbms. E.g. user interface, data analysis and data mining, various business services Database administrators (DBAs) – administer databases: ...
Link to technical report
... contract. The database was constructed in PostgreSQL, an open-source database management system. The REA database was primarily used for the storage of DRDC Atlantic environmental data. However, additional data sets from external sources were added for bathymetry and geological data. As use of the R ...
... contract. The database was constructed in PostgreSQL, an open-source database management system. The REA database was primarily used for the storage of DRDC Atlantic environmental data. However, additional data sets from external sources were added for bathymetry and geological data. As use of the R ...
Oracle Single Client Access Name (SCAN)
... Note: If your DNS server does not return a set of three IPs as shown in figure 3 or does not roundrobin, ask your network administrator to enable such a setup. Round-robin on DNS level allows for a connection request load balancing across SCAN listeners floating in the cluster. It is not required fo ...
... Note: If your DNS server does not return a set of three IPs as shown in figure 3 or does not roundrobin, ask your network administrator to enable such a setup. Round-robin on DNS level allows for a connection request load balancing across SCAN listeners floating in the cluster. It is not required fo ...
Configuring and Monitoring Database Servers
... The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced or disclosed to others without the prior permission of eG Innovations, Inc. eG Innovations, Inc. makes no warranty of any kind with regard to the software and d ...
... The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced or disclosed to others without the prior permission of eG Innovations, Inc. eG Innovations, Inc. makes no warranty of any kind with regard to the software and d ...
Aster Database Administrator Guide - Information Products
... create derivative works of, and distribute the Feedback and derivative works thereof without limitation on a royalty-free basis. Further, Teradata Corporation will be free to use any ideas, concepts, know-how, or techniques contained in such Feedback for any purpose whatsoever, including developing, ...
... create derivative works of, and distribute the Feedback and derivative works thereof without limitation on a royalty-free basis. Further, Teradata Corporation will be free to use any ideas, concepts, know-how, or techniques contained in such Feedback for any purpose whatsoever, including developing, ...
transactions, database tuning, and advanced topics
... Theorem: If the serialization graph of a computation is acyclic, then every transaction reads the same values and writes the same values as it would in a serial execution consistent with the graph. Proof: Take any topological sort of the graph. The topological sort represents a serial schedule with ...
... Theorem: If the serialization graph of a computation is acyclic, then every transaction reads the same values and writes the same values as it would in a serial execution consistent with the graph. Proof: Take any topological sort of the graph. The topological sort represents a serial schedule with ...
DESERVE: A FRAMEWORK FOR DETECTING PROGRAM SECURITY VULNERABILITY EXPLOITATIONS
... DEtecting program SEcuRity Vulnerability Exploitations). DESERVE identifies exploitable statements from source code based on static backward slicing and embeds necessary code to detect attacks. During the deployment stage, the enhanced programs execute exploitable statements in a separate test envir ...
... DEtecting program SEcuRity Vulnerability Exploitations). DESERVE identifies exploitable statements from source code based on static backward slicing and embeds necessary code to detect attacks. During the deployment stage, the enhanced programs execute exploitable statements in a separate test envir ...
- Oracle Business Intelligence Foundation Suite
... interactive dashboards, ad hoc analysis, multi-dimensional OLAP, scorecards, what-if scenario analysis, and predictive analytics on an integrated platform. It enables access to information through multiple channels such as web-based user interfaces, industry standard portals, mobile devices, and the ...
... interactive dashboards, ad hoc analysis, multi-dimensional OLAP, scorecards, what-if scenario analysis, and predictive analytics on an integrated platform. It enables access to information through multiple channels such as web-based user interfaces, industry standard portals, mobile devices, and the ...
PHP Chapter 8
... • The mysql_fetch_assoc() function returns the fields in the current row of a resultset into an associative array and moves the result pointer to the next row • The difference between mysql_fetch_assoc() and mysql_fetch_row() is that instead of returning the fields into an indexed array, the mysql_f ...
... • The mysql_fetch_assoc() function returns the fields in the current row of a resultset into an associative array and moves the result pointer to the next row • The difference between mysql_fetch_assoc() and mysql_fetch_row() is that instead of returning the fields into an indexed array, the mysql_f ...
Core Responsibilities of a Cloud Architect
... In this course, you will manage the design and plan the implementation of cloud architectures as needed to function as a Certified Cloud Master. You will: ...
... In this course, you will manage the design and plan the implementation of cloud architectures as needed to function as a Certified Cloud Master. You will: ...
AWS Database Migration Service - Step-by
... You can use several AWS tools and services to migrate data from an external database to AWS. Depending on the type of database migration you are doing, you may find that the native migration tools for your database engine are also effective. AWS Database Migration Service (AWS DMS) helps you migrate d ...
... You can use several AWS tools and services to migrate data from an external database to AWS. Depending on the type of database migration you are doing, you may find that the native migration tools for your database engine are also effective. AWS Database Migration Service (AWS DMS) helps you migrate d ...
From Java to Ruby
... Shared nothings make scaling easy by adding hardware. Each application can fulfill requests independantly. only a few layers, such as the database, are shared across a cluster. Most Ruby web applications use this approach. ...
... Shared nothings make scaling easy by adding hardware. Each application can fulfill requests independantly. only a few layers, such as the database, are shared across a cluster. Most Ruby web applications use this approach. ...
The SQL SELECT Statement
... Some database systems require a semicolon at the end of each SQL statement. Semicolon is the standard way to separate each SQL statement in database systems that allow more than one SQL statement to be executed in the same call to the server. We are using MS Access and SQL Server 2000 and we do not ...
... Some database systems require a semicolon at the end of each SQL statement. Semicolon is the standard way to separate each SQL statement in database systems that allow more than one SQL statement to be executed in the same call to the server. We are using MS Access and SQL Server 2000 and we do not ...
Graph Databases
... worked natively with graphs. Our vision was to keep all the proven features from the relational database (transactions, ACID, triggers, etc.) but use a data model for the 21st century. Project Neo was born, and with it graph databases as we know them today. The first decade of the new millennium has ...
... worked natively with graphs. Our vision was to keep all the proven features from the relational database (transactions, ACID, triggers, etc.) but use a data model for the 21st century. Project Neo was born, and with it graph databases as we know them today. The first decade of the new millennium has ...
Partition, Compress, Archive and Purge
... • A very few components and reports access archive tables – Development cost of customisation UKOUG PeopleSoft 2013 - Partition, Compress, Archive, Purge ...
... • A very few components and reports access archive tables – Development cost of customisation UKOUG PeopleSoft 2013 - Partition, Compress, Archive, Purge ...