10-realSQL
... Main memory (RAM) for currently used data. Disk for the main database (secondary storage). Tapes for archiving older versions of the data (tertiary storage). ...
... Main memory (RAM) for currently used data. Disk for the main database (secondary storage). Tapes for archiving older versions of the data (tertiary storage). ...
Insert, Update and Delete in Access
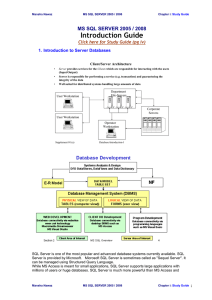
... All advanced database management systems include some kind of service applications as part of the database system. For example, to use the SQL Server database, you must have an application called "SQL Server Engine" running on the computer. This application is a windows service (a hidden application ...
... All advanced database management systems include some kind of service applications as part of the database system. For example, to use the SQL Server database, you must have an application called "SQL Server Engine" running on the computer. This application is a windows service (a hidden application ...
to my CV in Word 97 format
... I developed several PC user interfaces in Microsoft Access to SQL Server 7.0 databases for Thrombolysis and CardioPulmonary Resuscitation clinical audit packages. I also developed three Microsoft Access databases for nursing research into Elements of Care and Patient Satisfaction Surveys. All of the ...
... I developed several PC user interfaces in Microsoft Access to SQL Server 7.0 databases for Thrombolysis and CardioPulmonary Resuscitation clinical audit packages. I also developed three Microsoft Access databases for nursing research into Elements of Care and Patient Satisfaction Surveys. All of the ...
Frolund Presentation
... processing can be assumed • Up to user to figure out what has happened • Crashed client does not affect other clients ...
... processing can be assumed • Up to user to figure out what has happened • Crashed client does not affect other clients ...
Understanding Database Pricing: Comparing Database and
... Basic: Targeted at small- to medium-sized businesses with basic data management requirements. These editions provide simplified management tools and basic database capabilities but are limited to the number of CPUs, and may also add limitations to memory, database size or number of users. ...
... Basic: Targeted at small- to medium-sized businesses with basic data management requirements. These editions provide simplified management tools and basic database capabilities but are limited to the number of CPUs, and may also add limitations to memory, database size or number of users. ...
Introduction to Database Systems
... architecture • If combined with client: thick-client architecture ...
... architecture • If combined with client: thick-client architecture ...
Basics on Geodatabases - UN-GGIM
... Raster: Sits independently within a file geodatabase and cannot be stored in a feature dataset. Topology file: Stores the rules which enforce data integrity within the database. Relationship file: Creates a join between multiple feature classes and/or non-spatial tables. ...
... Raster: Sits independently within a file geodatabase and cannot be stored in a feature dataset. Topology file: Stores the rules which enforce data integrity within the database. Relationship file: Creates a join between multiple feature classes and/or non-spatial tables. ...
In-Class Exercise #6 – Putting data into Database
... In-Class Exercise SQL #2: Putting Information into a Database Submit your solutions for Part 2 and Part 4 of this exercise as a word file through Blackboard. In this exercise, you will begin to build a database for a simple contact management system for a marketing organization called MarketCo. You’ ...
... In-Class Exercise SQL #2: Putting Information into a Database Submit your solutions for Part 2 and Part 4 of this exercise as a word file through Blackboard. In this exercise, you will begin to build a database for a simple contact management system for a marketing organization called MarketCo. You’ ...
Data_Security
... certain software attacks. (See https://www.elie.net/go/p14a) It can’t protect its keys from an ‘inside job’. Where security is truly critical a 3rd party hardware based encryption system (using the EKM interface) is almost mandatory. These have no interface to reveal their keys. Only the box can dec ...
... certain software attacks. (See https://www.elie.net/go/p14a) It can’t protect its keys from an ‘inside job’. Where security is truly critical a 3rd party hardware based encryption system (using the EKM interface) is almost mandatory. These have no interface to reveal their keys. Only the box can dec ...
Wait-Time Based Oracle Performance Management
... 50% performance improvement Log file sync wait event was then the largest ...
... 50% performance improvement Log file sync wait event was then the largest ...
SQL Server 2016 Operational Analytics
... Enterprise Resource Planning (ERP) – Inventory, Order, Sales, Machine Data – Data from machine operations on factory floor ...
... Enterprise Resource Planning (ERP) – Inventory, Order, Sales, Machine Data – Data from machine operations on factory floor ...
Introduction to Oracle
... OLE DB is Microsoft’s object-oriented interface for relational and other databases. ADO (Active Data Objects) is Microsoft’s standard providing easier access to OLE DB data for the non-object-oriented programmer. ...
... OLE DB is Microsoft’s object-oriented interface for relational and other databases. ADO (Active Data Objects) is Microsoft’s standard providing easier access to OLE DB data for the non-object-oriented programmer. ...
Advanced Database - Lightweight OCW University of Palestine
... knowledge of database management systems enabling them to work productively on projects involving online database applications. On completion of this subject students will have gained an understanding of why a database application requires the use of a Database Management System (DBMS) to facilitate ...
... knowledge of database management systems enabling them to work productively on projects involving online database applications. On completion of this subject students will have gained an understanding of why a database application requires the use of a Database Management System (DBMS) to facilitate ...
Procedure to Setup Microsoft SQL Server 7
... 8. When “Next>” is clicked above, setup will start applying the SQL Server 7.0 Service Pack2. Installation will display the following screen after it finishes copying the necessary files. Restart the computer to apply the changes. ...
... 8. When “Next>” is clicked above, setup will start applying the SQL Server 7.0 Service Pack2. Installation will display the following screen after it finishes copying the necessary files. Restart the computer to apply the changes. ...
database server
... – Updates used to store orders • New record created for order in Order table • Customer information added to other tables • Quantities updated in inventory tables ...
... – Updates used to store orders • New record created for order in Order table • Customer information added to other tables • Quantities updated in inventory tables ...
Diapositive 1
... Like for Database, user can also create new objects (Text, Barcode or Image) that will be directly linked to the new database variable At the end All variables and objects are created and a predesigned label is built up automatically. User just needs to adjust the layout. ...
... Like for Database, user can also create new objects (Text, Barcode or Image) that will be directly linked to the new database variable At the end All variables and objects are created and a predesigned label is built up automatically. User just needs to adjust the layout. ...
D3S2_TSV404_Database_Vulnerability_Assessment_v1
... ■ Different audit settings for different databases – Audit the privileged and database users – Various level of audit settings ...
... ■ Different audit settings for different databases – Audit the privileged and database users – Various level of audit settings ...
table - Staffordshire University
... // fetches a row of fields and steps to the next one $row = $rsSearch->fetch_assoc(); // gets each field by name $linkcode=$row['LinkAd']; $buycode=$row['BuyAd']; ...
... // fetches a row of fields and steps to the next one $row = $rsSearch->fetch_assoc(); // gets each field by name $linkcode=$row['LinkAd']; $buycode=$row['BuyAd']; ...
SQL Injection
... command execution, and if this is permitted to the web user, complete compromise of the webserver is inevitable. What we had done so far was limited to the web application and the underlying database, but if we can run commands, the webserver itself cannot help but be compromised. Access to xp_cmdsh ...
... command execution, and if this is permitted to the web user, complete compromise of the webserver is inevitable. What we had done so far was limited to the web application and the underlying database, but if we can run commands, the webserver itself cannot help but be compromised. Access to xp_cmdsh ...