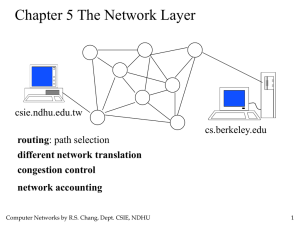
HOPI Project Update
... •Problems to understand • When does a host use the circuit switched infrastructure and when does it use the packet infrastructure? • Temporal degree of dynamic provisioning • Temporal duration of dynamic paths and requirement for scheduling • Topological extent of deterministic provisioning • Examin ...
... •Problems to understand • When does a host use the circuit switched infrastructure and when does it use the packet infrastructure? • Temporal degree of dynamic provisioning • Temporal duration of dynamic paths and requirement for scheduling • Topological extent of deterministic provisioning • Examin ...
tutorial7
... • If Group-Membership-LSP distribution is limited to an area, then how multicast between different areas of the same AS is executed ? • A part of Area-Border-Routers are defined to function also as a Inter Area Multicast Forwarders • In this role, they summarize Group-Membership-LSP for their area a ...
... • If Group-Membership-LSP distribution is limited to an area, then how multicast between different areas of the same AS is executed ? • A part of Area-Border-Routers are defined to function also as a Inter Area Multicast Forwarders • In this role, they summarize Group-Membership-LSP for their area a ...
What is Wireless Mesh Network?
... access points installed at each network user's locale. Each network user is also a provider, forwarding data to the next node. The networking infrastructure is decentralized and simplified because each node need only transmit as far as the next node. Wireless mesh networking could allow people livin ...
... access points installed at each network user's locale. Each network user is also a provider, forwarding data to the next node. The networking infrastructure is decentralized and simplified because each node need only transmit as far as the next node. Wireless mesh networking could allow people livin ...
Solving the problems of IMS using P2P technology By Adrian
... the end-to-end principle of the Internet • Network is unaware of the applications, this makes it scalable • Nothing should be done in the network that can be done in an end-system • Quality of Service (QoS) is a matter of bandwidth availability and not of central control ...
... the end-to-end principle of the Internet • Network is unaware of the applications, this makes it scalable • Nothing should be done in the network that can be done in an end-system • Quality of Service (QoS) is a matter of bandwidth availability and not of central control ...
1 - Salisbury University
... end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure 1.4 delay, loss, throughput in networks 1.5 protocol layers, service models 1.6 networks under attack: security 1.7 history ...
... end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure 1.4 delay, loss, throughput in networks 1.5 protocol layers, service models 1.6 networks under attack: security 1.7 history ...
Network Layer
... reason not to put the complexity in the hosts. 2. The subnet is a major international investment that will last for decades, so it should not be cluttered up with features that may become obsolete quickly. 3. Some applications, such as digitized voice and real-time data collection may regard speedy ...
... reason not to put the complexity in the hosts. 2. The subnet is a major international investment that will last for decades, so it should not be cluttered up with features that may become obsolete quickly. 3. Some applications, such as digitized voice and real-time data collection may regard speedy ...
Lesson 9 - EdTechnology, educational technology
... LANs are smaller networks limited in geographic area. Many LANs connected together allow the Internet to function. But LANs have limitations in scale. Although there have been technological advances to improve the speed of communications, such as Metro Optical, Gigabit, and 10Gigabit Ethernet, dista ...
... LANs are smaller networks limited in geographic area. Many LANs connected together allow the Internet to function. But LANs have limitations in scale. Although there have been technological advances to improve the speed of communications, such as Metro Optical, Gigabit, and 10Gigabit Ethernet, dista ...
Document
... numbers and routing complexity • Site looks to rest of internet like single network • Each LAN assigned subnet number • Host portion of address partitioned into subnet number and host number • Local routers route within subnetted network • Subnet mask indicates which bits are subnet number and which ...
... numbers and routing complexity • Site looks to rest of internet like single network • Each LAN assigned subnet number • Host portion of address partitioned into subnet number and host number • Local routers route within subnetted network • Subnet mask indicates which bits are subnet number and which ...
Network Routing Algorithms
... Computing the New Routes • Dijkstra’s Shortest Path algorithm is used to determine the shortest path to each destination. ...
... Computing the New Routes • Dijkstra’s Shortest Path algorithm is used to determine the shortest path to each destination. ...
3rd Edition: Chapter 4
... connectionless service VC network provides network-layer connection service Analogous to the transport-layer services, but: ...
... connectionless service VC network provides network-layer connection service Analogous to the transport-layer services, but: ...
Network Routing Algorithms
... Computing the New Routes • Dijkstra’s Shortest Path algorithm is used to determine the shortest path to each destination. ...
... Computing the New Routes • Dijkstra’s Shortest Path algorithm is used to determine the shortest path to each destination. ...
AODV (Adaptive On-Demand Distance Vector) Routing Protocol. [3
... of routing and wireless routing. Wireless routing handles multihop communication for symmetric as well as asymmetric links. MANET is a wireless Ad-hoc network. MANET extended as (mobile Ad-hoc network).MANET easily handles changing topology. Due to high level of topological changes (dynamic characte ...
... of routing and wireless routing. Wireless routing handles multihop communication for symmetric as well as asymmetric links. MANET is a wireless Ad-hoc network. MANET extended as (mobile Ad-hoc network).MANET easily handles changing topology. Due to high level of topological changes (dynamic characte ...
4th Edition: Chapter 1 - Simon Fraser University
... Residential, company and university ISPs Access ISPs in turn must be interconnected. So that any two hosts can send packets to each other Resulting network of networks is very complex Evolution was driven by economics and national policies Let’s take a stepwise approach to describe current Int ...
... Residential, company and university ISPs Access ISPs in turn must be interconnected. So that any two hosts can send packets to each other Resulting network of networks is very complex Evolution was driven by economics and national policies Let’s take a stepwise approach to describe current Int ...
Week_Nine_Net_Design_ppt
... • Instead of configuring static routes to remote networks on every router, a dynamic routing protocol allows the routers to automatically learn about these networks from other routers. • These networks -and the best path to each network -are added to the router's routing table and denoted as a netwo ...
... • Instead of configuring static routes to remote networks on every router, a dynamic routing protocol allows the routers to automatically learn about these networks from other routers. • These networks -and the best path to each network -are added to the router's routing table and denoted as a netwo ...
COMP 535 Multicasting Simon Foucher (260 223 197) McGill
... shared trees. PIM-DM multicast tree construction is data-driven, and is used only if data rates exceed a certain value. PIM-SM employs per-group rendezvous points which are used by senders to announce their existence, and by receivers to learn about new senders of a group. The third type of protocol ...
... shared trees. PIM-DM multicast tree construction is data-driven, and is used only if data rates exceed a certain value. PIM-SM employs per-group rendezvous points which are used by senders to announce their existence, and by receivers to learn about new senders of a group. The third type of protocol ...
Data Center Interconnection with VXLAN
... VLANs stretched across sites. While it is true that some VM mobility solutions have removed the need to provide layer-2 connectivity between locations, many current solutions still require layer-2 interconnection. This is also true of many high availability clustering systems and storage virtualizat ...
... VLANs stretched across sites. While it is true that some VM mobility solutions have removed the need to provide layer-2 connectivity between locations, many current solutions still require layer-2 interconnection. This is also true of many high availability clustering systems and storage virtualizat ...
Document
... » closed loop because the network state has to be fed back to the point where traffic is regulated, usually the source » typically do not use resource reservation ...
... » closed loop because the network state has to be fed back to the point where traffic is regulated, usually the source » typically do not use resource reservation ...
momina-RIP
... protocols on internal networks. Helps routers dynamically adapt to changes of network connections by communicating information about which networks each router can reach and how far away those networks are. Its made obsolete by OSPF and IS-IS. Also sometimes called Rest in Pieces. ...
... protocols on internal networks. Helps routers dynamically adapt to changes of network connections by communicating information about which networks each router can reach and how far away those networks are. Its made obsolete by OSPF and IS-IS. Also sometimes called Rest in Pieces. ...
acba0bdb38899c8
... routers would know that route failed ( it is useful in flapping networks ). - hold finish if : The hold-down timer expires. Another update is received with a better metric. ...
... routers would know that route failed ( it is useful in flapping networks ). - hold finish if : The hold-down timer expires. Another update is received with a better metric. ...
Assessment of the Internet Protocol Routing in Space—Joint Capability Technology Demonstration
... with a large number of terminals (32 user nodes) that loaded the network, better traffic generation capabilities, and a more refined set of tests and testing tools than those used in previous IRIS demonstrations. The laboratory emulation test bed is shown in Fig. 5. The PSIM included the three IRIS- ...
... with a large number of terminals (32 user nodes) that loaded the network, better traffic generation capabilities, and a more refined set of tests and testing tools than those used in previous IRIS demonstrations. The laboratory emulation test bed is shown in Fig. 5. The PSIM included the three IRIS- ...
Network Routing Algorithms
... Computing the New Routes • Dijkstra’s Shortest Path algorithm is used to determine the shortest path to each destination. ...
... Computing the New Routes • Dijkstra’s Shortest Path algorithm is used to determine the shortest path to each destination. ...
1.2.2 TCP/IP Protocol Suite (continued)
... We have given the overview of the Internet structure. For communication to happen, we need both hardware and software. This is similar to a complex computation in which we need both a computer and a program. In the next section, we show how these combinations of hardware and ...
... We have given the overview of the Internet structure. For communication to happen, we need both hardware and software. This is similar to a complex computation in which we need both a computer and a program. In the next section, we show how these combinations of hardware and ...