Architectures for an Event Notification Service Scalable to Wide
... 1.2 Structure of the thesis Chapter 2 explores the problem space for an event service. Related technologies and systems are surveyed and classified. This classification helps us in isolating and defining the main challenges that we intend to face in this research. Chapter 3 defines the SIENA event s ...
... 1.2 Structure of the thesis Chapter 2 explores the problem space for an event service. Related technologies and systems are surveyed and classified. This classification helps us in isolating and defining the main challenges that we intend to face in this research. Chapter 3 defines the SIENA event s ...
TinyOS – A Skeleton OS for Networks of Embedded Systems
... Schema-capabilities of motes in the system as a single virtual Database “table” Tables-typed attributes , commands that can be run within query executor. Query processing-sensor readings from each mote is placed in “tuples” (passed between motes for multihop routing and/or aggregation, or migh ...
... Schema-capabilities of motes in the system as a single virtual Database “table” Tables-typed attributes , commands that can be run within query executor. Query processing-sensor readings from each mote is placed in “tuples” (passed between motes for multihop routing and/or aggregation, or migh ...
TinyOS – A Skeleton OS for Networks of Embedded Systems
... Schema-capabilities of motes in the system as a single virtual Database “table” Tables-typed attributes , commands that can be run within query executor. Query processing-sensor readings from each mote is placed in “tuples” (passed between motes for multihop routing and/or aggregation, or migh ...
... Schema-capabilities of motes in the system as a single virtual Database “table” Tables-typed attributes , commands that can be run within query executor. Query processing-sensor readings from each mote is placed in “tuples” (passed between motes for multihop routing and/or aggregation, or migh ...
TinyOS tutorial (5)
... • Tasks are scheduled to executed and put into a single queue. A task doesn’t preempt another task. • Hardware event handlers are executed in response to a hardware interrupt. They may preempt the execution of a task and other hardware handler. – The events and commands executed as part of a hardwar ...
... • Tasks are scheduled to executed and put into a single queue. A task doesn’t preempt another task. • Hardware event handlers are executed in response to a hardware interrupt. They may preempt the execution of a task and other hardware handler. – The events and commands executed as part of a hardwar ...
Peekquence: Visual Analytics for Event Sequence Data
... different granularities providing users with appropriate interpretation layers, which confirm the importance of paving the cow path of users’ analysis pattern [3]. To increase the transparency of complex pattern mining algorithms like SPAM, we believe that it is important to provide users with visua ...
... different granularities providing users with appropriate interpretation layers, which confirm the importance of paving the cow path of users’ analysis pattern [3]. To increase the transparency of complex pattern mining algorithms like SPAM, we believe that it is important to provide users with visua ...
Visual management of Sags and Incidents gathered in Management
... Event – Incidence: Direct association of one event to one incidence, like a cause-effect relation. ...
... Event – Incidence: Direct association of one event to one incidence, like a cause-effect relation. ...
5. PsEPR Implementation Details
... (NAT) systems, and so forth; as IM clients, we are able to fully exploit this connectivity to our advantage. By mapping our concepts into Jabber constructs (e.g. “JIDs” and “resources” play the role of PsEPR services and instances), we gain the benefit of object-level addressing, enabling our channe ...
... (NAT) systems, and so forth; as IM clients, we are able to fully exploit this connectivity to our advantage. By mapping our concepts into Jabber constructs (e.g. “JIDs” and “resources” play the role of PsEPR services and instances), we gain the benefit of object-level addressing, enabling our channe ...
A Shared Global Event Propagation System to Enable Next Generation
... (NAT) systems, and so forth; as IM clients, we are able to fully exploit this connectivity to our advantage. By mapping our concepts into Jabber constructs (e.g. “JIDs” and “resources” play the role of PsEPR services and instances), we gain the benefit of object-level addressing, enabling our channe ...
... (NAT) systems, and so forth; as IM clients, we are able to fully exploit this connectivity to our advantage. By mapping our concepts into Jabber constructs (e.g. “JIDs” and “resources” play the role of PsEPR services and instances), we gain the benefit of object-level addressing, enabling our channe ...
Presentation (ppt)
... • These educational materials have been developed as part of the instructors educational tasks. • The “Athens University of Economics and Business Open Courses” project only funded the reformatting of these ...
... • These educational materials have been developed as part of the instructors educational tasks. • The “Athens University of Economics and Business Open Courses” project only funded the reformatting of these ...
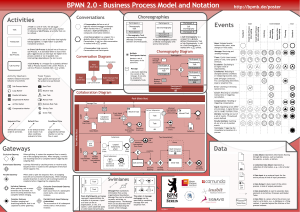
面向服务概述
... monolithic client/server applications into self-managing components, or objects, that can interoperate across disparate networks and operating systems. ◦ SUN J2EE ...
... monolithic client/server applications into self-managing components, or objects, that can interoperate across disparate networks and operating systems. ◦ SUN J2EE ...
Κατανεμημένα Συστήματα
... • CORBA and Java RMI have proved very useful – Higher-level interface that hides underlying complexity – Invocation model: request/reply client/server – Good for LANs but does not scale ...
... • CORBA and Java RMI have proved very useful – Higher-level interface that hides underlying complexity – Invocation model: request/reply client/server – Good for LANs but does not scale ...
A Concept for a Medical Device Plug-and-Play
... are use cases from travel agencies where a flight and a hotel must be booked for a customer. Events are disregarded in this scenario. In the medical application domain a lot of communication is event driven. For example, alarms were sent and real-time data is transmitted. That means that publish-sub ...
... are use cases from travel agencies where a flight and a hotel must be booked for a customer. Events are disregarded in this scenario. In the medical application domain a lot of communication is event driven. For example, alarms were sent and real-time data is transmitted. That means that publish-sub ...
Amplifiers for the Masses: EDFA, EDWA, and SOA Amplets for Metro
... EDFAs consist of a pump laser, pump WDM coupler, erbium doped fiber (EDF) spool, input and output isolators, and input and output detectors. Shorter EDF lengths and tighter bend radii gave rise to smaller components and packaging. The pump laser operates over a large temperature range and drive curr ...
... EDFAs consist of a pump laser, pump WDM coupler, erbium doped fiber (EDF) spool, input and output isolators, and input and output detectors. Shorter EDF lengths and tighter bend radii gave rise to smaller components and packaging. The pump laser operates over a large temperature range and drive curr ...
1MIT1 COMPUTER GRAPHICS AND IMAGE PROCESSING Review of Graphics Fundamentals
... associations, Indexed collections, Using Hibernate Template, Querying, Session management, Transaction integration and demarcation. Spring Introduction of Spring Framework, Spring Architecture, Spring Framework definition, Spring & MVC, Factory Pattern, Bean Factory, Spring Context definition, Inver ...
... associations, Indexed collections, Using Hibernate Template, Querying, Session management, Transaction integration and demarcation. Spring Introduction of Spring Framework, Spring Architecture, Spring Framework definition, Spring & MVC, Factory Pattern, Bean Factory, Spring Context definition, Inver ...
System architectures - University of Manitoba
... Components are called based on their interface (an instance of system interface) which advertises a component's functionality and protocols. ...
... Components are called based on their interface (an instance of system interface) which advertises a component's functionality and protocols. ...
REST Web Services Characteristics Client
... applications. An application's business logic or individual functions are modularized and presented as services for consumer/client applications. What's key to these services is their loosely coupled nature; i.e., the service interface is independent of the implementation. Application developers or ...
... applications. An application's business logic or individual functions are modularized and presented as services for consumer/client applications. What's key to these services is their loosely coupled nature; i.e., the service interface is independent of the implementation. Application developers or ...
Demystifying SOA and EDA
... • Gives a more responsive IT organisation • Decreases development and deployment cycle times • Reduces maintenance costs • Enhances existing IT systems ...
... • Gives a more responsive IT organisation • Decreases development and deployment cycle times • Reduces maintenance costs • Enhances existing IT systems ...