CIS 5357 - FSU Computer Science
... If b’ = b, the attacker wins. If every attacker has only a negligible probability of success, we say that the scheme is secure under chosen-plaintext attacks. ...
... If b’ = b, the attacker wins. If every attacker has only a negligible probability of success, we say that the scheme is secure under chosen-plaintext attacks. ...
Cryptanalysis of Shieh-Lin-Yang
... The message m is first signed by an initiator U1, and then is sent separately to all signer. Finally,U1 is responsible for combining these individual signature into a multisignature. ...
... The message m is first signed by an initiator U1, and then is sent separately to all signer. Finally,U1 is responsible for combining these individual signature into a multisignature. ...
On Designatedly Verified (Non-interactive) Watermarking Schemes
... watermark is embedded in the host image directly in the spatial domain. Although, all the schemes in this paper can be applied to all media objects such as text, video, audio, images etc., we have restricted our discussion to images alone for the sake of brevity. Regardless of the embedding method, ...
... watermark is embedded in the host image directly in the spatial domain. Although, all the schemes in this paper can be applied to all media objects such as text, video, audio, images etc., we have restricted our discussion to images alone for the sake of brevity. Regardless of the embedding method, ...
The key questions that we`d like to ask at the beginning
... your entire conversation. Because if a hacker does manage to gain access to the private key, he still won’t be able to recover the shared, short-term secret key and will not be able to decrypt any communications. What’s more, PFS continuously changes the key material during a session, generating a n ...
... your entire conversation. Because if a hacker does manage to gain access to the private key, he still won’t be able to recover the shared, short-term secret key and will not be able to decrypt any communications. What’s more, PFS continuously changes the key material during a session, generating a n ...
How to Encrypt with the LPN Problem
... Related work. We briefly review the related work building cryptographic primitives based on hard learning problems. We have already cited the authentication protocol HB+ [19], which was itself derived from a simpler protocol named HB by Hopper and Blum [17]. Both protocols possess a proof of securi ...
... Related work. We briefly review the related work building cryptographic primitives based on hard learning problems. We have already cited the authentication protocol HB+ [19], which was itself derived from a simpler protocol named HB by Hopper and Blum [17]. Both protocols possess a proof of securi ...
256 Bit Key — Is It Big Enough?
... keys typically doubles the total amount of nonvolatile and volatile data memory which could therefore increase the device cost; however, as the line widths in devices shrink, the core size of the memory cells becomes a smaller and smaller percentage of the total device area reducing this cost penalt ...
... keys typically doubles the total amount of nonvolatile and volatile data memory which could therefore increase the device cost; however, as the line widths in devices shrink, the core size of the memory cells becomes a smaller and smaller percentage of the total device area reducing this cost penalt ...
MT311-14
... System security refers to the safety and stability of the computing environment. The safety and stability can be breached in a number of ways. When a malicious application (such as a virus) executes itself, it can cause damage to the system — for example, by deleting some critical files and renderin ...
... System security refers to the safety and stability of the computing environment. The safety and stability can be breached in a number of ways. When a malicious application (such as a virus) executes itself, it can cause damage to the system — for example, by deleting some critical files and renderin ...
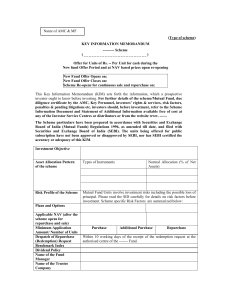
KEY INFORMATION MEMORANDUM
... Within 10 working days of the receipt of the redemption request at the authorised centre of the ------- Fund. ...
... Within 10 working days of the receipt of the redemption request at the authorised centre of the ------- Fund. ...
Three challenges with secret key encryption
... Keyspace (the range of possible value of the Key)? Why the issue of number of bit required in a key to ensure secure encryption is controversial? A brute -force attack is applying all possible value of a key to the algorithm until you succeed in deciphering the message. The longer the key space the ...
... Keyspace (the range of possible value of the Key)? Why the issue of number of bit required in a key to ensure secure encryption is controversial? A brute -force attack is applying all possible value of a key to the algorithm until you succeed in deciphering the message. The longer the key space the ...
PPT - Purdue Computer Science
... – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
... – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
DCLG (11) 75 Presentation, HM Treasury
... date and robust membership data are available. Calculations will have an effective date of 1 April 2015. • Methodology: Projected Unit Method (PUM). Standard actuarial methodology with one year control period. PUM measures the cost of accrual and avoids emphasis on any one category of membership. It ...
... date and robust membership data are available. Calculations will have an effective date of 1 April 2015. • Methodology: Projected Unit Method (PUM). Standard actuarial methodology with one year control period. PUM measures the cost of accrual and avoids emphasis on any one category of membership. It ...
Teaching Cryptologic Mathematics
... hash. A hash function is a map h from a long input x to a much shorter output y such that it is not feasible to find two different inputs x and x' such that h(x)=h(x'). Having introduced hash functions, RSA digital signature may be described as follows. After sending to Bob the message x, Alice sign ...
... hash. A hash function is a map h from a long input x to a much shorter output y such that it is not feasible to find two different inputs x and x' such that h(x)=h(x'). Having introduced hash functions, RSA digital signature may be described as follows. After sending to Bob the message x, Alice sign ...
Security
... developed public-key cryptography Asymmetric: – Private key – kept secret by owner – Public key – distributed freely to all who wish to send – Generated by computer algorithm, so a mathematical relation exists between them ... however ... – It is computationally difficult to determine the private ke ...
... developed public-key cryptography Asymmetric: – Private key – kept secret by owner – Public key – distributed freely to all who wish to send – Generated by computer algorithm, so a mathematical relation exists between them ... however ... – It is computationally difficult to determine the private ke ...
compatible-development-of
... suspicions about a National Security Agency (NSA) backdoor. DES consequently came under intense academic scrutiny which motivated the modern understanding of block ciphers and their cryptanalysis. Diffie and Hellman publish New Directions in Cryptography. Phil Zimmermann releases the public key encr ...
... suspicions about a National Security Agency (NSA) backdoor. DES consequently came under intense academic scrutiny which motivated the modern understanding of block ciphers and their cryptanalysis. Diffie and Hellman publish New Directions in Cryptography. Phil Zimmermann releases the public key encr ...
Problem Set 8 The getting is
... J. If mp < np and p is positive then m < n. True in N? In Z? 2. If a=' b (mod n) and c =' d (mod n) then a + c =' b + d (mod n). 3. If a=' b (mod n) and c =' d (mod n) then ac =' bd (mod n). 4 . ......,(alb) and ......,(alc) ...
... J. If mp < np and p is positive then m < n. True in N? In Z? 2. If a=' b (mod n) and c =' d (mod n) then a + c =' b + d (mod n). 3. If a=' b (mod n) and c =' d (mod n) then ac =' bd (mod n). 4 . ......,(alb) and ......,(alc) ...
solution - My Webspace files
... Problems and occasional updates on solutions and winners will be posted at webspace.ship.edu/pttaylor/PSC/index.html ...
... Problems and occasional updates on solutions and winners will be posted at webspace.ship.edu/pttaylor/PSC/index.html ...
A Secure Anti-Collusion Data Sharing Scheme for
... encryption, proxy re-encryption and lazy re-encryption to achieve finegrained data access control without disclosing data contents. DISADVANTAGES OF EXISTING SYSTEM: The file-block keys need to be updated and distributed for a user revocation; therefore, the system had a heavy key distribution ove ...
... encryption, proxy re-encryption and lazy re-encryption to achieve finegrained data access control without disclosing data contents. DISADVANTAGES OF EXISTING SYSTEM: The file-block keys need to be updated and distributed for a user revocation; therefore, the system had a heavy key distribution ove ...
Packaging Information: Data Compression and
... A sender looks up the recipient's public key and uses it to encode a message The recipient then decodes the message with his or her private key (this private key is necessary to decode the message) ...
... A sender looks up the recipient's public key and uses it to encode a message The recipient then decodes the message with his or her private key (this private key is necessary to decode the message) ...
pdf
... (GQ) signature scheme (this was the scheme from Homework 4, problem 1; note that you do not actually need any details of this scheme other than to recall that the public key is N, e, y and the secret key is x for which x e = y). Prove that this is indeed a secure identity-based scheme when H is a ra ...
... (GQ) signature scheme (this was the scheme from Homework 4, problem 1; note that you do not actually need any details of this scheme other than to recall that the public key is N, e, y and the secret key is x for which x e = y). Prove that this is indeed a secure identity-based scheme when H is a ra ...
Secure Deduplication with Efficient and Reliable
... may be frequently updated by the users, including insertion, deletion, modification, appending, reordering, etc. One critical challenge of today’s cloud storage services is the management of the ever-increasing volume of data. According to the analysis report of IDC, the volume of data in the wild i ...
... may be frequently updated by the users, including insertion, deletion, modification, appending, reordering, etc. One critical challenge of today’s cloud storage services is the management of the ever-increasing volume of data. According to the analysis report of IDC, the volume of data in the wild i ...
The United States Secret Service - Federal Reserve Bank of San
... New York Electronic Crimes Task Force model, throughout the United States for the purpose of preventing, detecting, and investigating various forms of electronic crimes, including potential terrorist attacks against critical infrastructure and financial payment systems. ...
... New York Electronic Crimes Task Force model, throughout the United States for the purpose of preventing, detecting, and investigating various forms of electronic crimes, including potential terrorist attacks against critical infrastructure and financial payment systems. ...
Secret sharing
Secret sharing (also called secret splitting) refers to methods for distributing a secret amongst a group of participants, each of whom is allocated a share of the secret. The secret can be reconstructed only when a sufficient number, of possibly different types, of shares are combined together; individual shares are of no use on their own.In one type of secret sharing scheme there is one dealer and n players. The dealer gives a share of the secret to the players, but only when specific conditions are fulfilled will the players be able to reconstruct the secret from their shares. The dealer accomplishes this by giving each player a share in such a way that any group of t (for threshold) or more players can together reconstruct the secret but no group of fewer than t players can. Such a system is called a (t, n)-threshold scheme (sometimes it is written as an (n, t)-threshold scheme).Secret sharing was invented independently by Adi Shamir and George Blakley in 1979.