True-False Questions
... security and privacy are more difficult. it is best used for cable television. even a radio can pick up the digital signal. Both a and c ...
... security and privacy are more difficult. it is best used for cable television. even a radio can pick up the digital signal. Both a and c ...
《Electromagnetic Field and Microwave Technology》 Course syllabus
... (1)The history of Circuit switch development (2)Circuit switch foundation. (3)Basic switch unit (4)Switch network 3 Digital program-controlled switching technology (12 class hour) (1) Characteristics and business performance of digital program-controlled switchboard (2)hardware structure of digital ...
... (1)The history of Circuit switch development (2)Circuit switch foundation. (3)Basic switch unit (4)Switch network 3 Digital program-controlled switching technology (12 class hour) (1) Characteristics and business performance of digital program-controlled switchboard (2)hardware structure of digital ...
Communicating over the Network - Seneca
... – Commonly referred to as hosts (source or destination of a message) – Each host has an address that will identify it on the network – Role of end devices: • Client (software installed so they can request & display info from the ...
... – Commonly referred to as hosts (source or destination of a message) – Each host has an address that will identify it on the network – Role of end devices: • Client (software installed so they can request & display info from the ...
Control System Specification
... 2.19. Gateway: A device that contains an I/O software mapping to translate data from one protocol to ...
... 2.19. Gateway: A device that contains an I/O software mapping to translate data from one protocol to ...
C THE GRIDES (GSM-R INTEGRITY DETECTION LINE Authors
... GRIDES project. In fact, an SDR-based system is a radio communication system which uses software routines for demodulation and digital signal processing (DSP) of radio signals. An SDR-receiver performs significant amounts of signal processing in a general purpose computer or a reconfigurable piece o ...
... GRIDES project. In fact, an SDR-based system is a radio communication system which uses software routines for demodulation and digital signal processing (DSP) of radio signals. An SDR-receiver performs significant amounts of signal processing in a general purpose computer or a reconfigurable piece o ...
Heterogeneous Cellular Networks: From Theory to Practice
... driven by smart phones, tablets, and other media-hungry devices, network operators will have to significantly increase the capacity of their networks as well as reduce the cost/bit delivered by perhaps two orders of magnitude. A number of studies have documented the over 100 percent annual growth in ...
... driven by smart phones, tablets, and other media-hungry devices, network operators will have to significantly increase the capacity of their networks as well as reduce the cost/bit delivered by perhaps two orders of magnitude. A number of studies have documented the over 100 percent annual growth in ...
Basic Ingredients of Network Management
... network, it makes the devices hard to reach Also hard to find out what it happen ...
... network, it makes the devices hard to reach Also hard to find out what it happen ...
Position Description
... appropriate funding within the NIRSA annual operating budget will be available. In addition to the above, the Regional Representative that is elected* to serve as Chair of the Member Network will have the following duties specific to their leadership role, which include but are not limited to: ...
... appropriate funding within the NIRSA annual operating budget will be available. In addition to the above, the Regional Representative that is elected* to serve as Chair of the Member Network will have the following duties specific to their leadership role, which include but are not limited to: ...
Preparation of Papers in Two-Column Format
... connect the entire globe. Someday LTE networks may replace all existing 2G and 3G networks, even before a full implementation of 3G. Many 3G standards are springing up that would make it difficult for 3G devices to be truly global. The main distinguishing factor between 3G and LTE is the data rates. ...
... connect the entire globe. Someday LTE networks may replace all existing 2G and 3G networks, even before a full implementation of 3G. Many 3G standards are springing up that would make it difficult for 3G devices to be truly global. The main distinguishing factor between 3G and LTE is the data rates. ...
Communication Networks
... A communication network, in its simplest form, is a set of equipment (機器) and facilities (管線) that provides services: the transfer of information between users located at various geographical points. Examples are such as telephone network, computer network, television broadcasting network, cellular ...
... A communication network, in its simplest form, is a set of equipment (機器) and facilities (管線) that provides services: the transfer of information between users located at various geographical points. Examples are such as telephone network, computer network, television broadcasting network, cellular ...
File - Learning@NDGTA
... computers exercising LAN control • In turn these may be part of a network with a larger mainframe company computer controlling all ...
... computers exercising LAN control • In turn these may be part of a network with a larger mainframe company computer controlling all ...
William Stallings Data and Computer Communications
... Means of commuinication: electrical wave with various frequencies Services: carrying signals that encode human conversations. Requirements: Real-time service: delay in the order of seconds can not be accepted; acceptable delay is around 250 milliseconds Availability requirement is higher than T ...
... Means of commuinication: electrical wave with various frequencies Services: carrying signals that encode human conversations. Requirements: Real-time service: delay in the order of seconds can not be accepted; acceptable delay is around 250 milliseconds Availability requirement is higher than T ...
Chapter 1 Communication Networks and Services
... 1970s: Computers connect directly to each other z ARPANET packet switching network z TCP/IP internet protocols z Ethernet local area network 1980s & 1990s: New applications and Internet growth z Commercialization of Internet z E-mail, file transfer, web, P2P, . . . z Internet traffic surpasses voice ...
... 1970s: Computers connect directly to each other z ARPANET packet switching network z TCP/IP internet protocols z Ethernet local area network 1980s & 1990s: New applications and Internet growth z Commercialization of Internet z E-mail, file transfer, web, P2P, . . . z Internet traffic surpasses voice ...
Chapter 1 - UniMAP Portal
... Frames are broadcast into coaxial cable NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
... Frames are broadcast into coaxial cable NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
What is a communication network?
... Frames are broadcast into coaxial cable NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
... Frames are broadcast into coaxial cable NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
acceptable-use - Gateway Education
... Tettenhall College uses internet filtering software to minimise the possibility of students intentionally or otherwise accessing inappropriate materials. The filtering software in place uses white lists (allowed sites) and black lists (disallowed sites) in conjunction with a real time page scanning ...
... Tettenhall College uses internet filtering software to minimise the possibility of students intentionally or otherwise accessing inappropriate materials. The filtering software in place uses white lists (allowed sites) and black lists (disallowed sites) in conjunction with a real time page scanning ...
View
... Privacy or security(every message travels along a dedicated line, only the intended recipient sees it. Physical boundaries prevents other user from gaining access the message eliminating the traffic problems. The use of dedicated links guarantees that each connection can carry its own data load; ...
... Privacy or security(every message travels along a dedicated line, only the intended recipient sees it. Physical boundaries prevents other user from gaining access the message eliminating the traffic problems. The use of dedicated links guarantees that each connection can carry its own data load; ...
UMTS - MobiHealth
... • CDMA (Code-Division Multiple-Access) is a "spread spectrum" technology, which means that it spreads the information contained in a particular signal of interest over a much greater bandwidth than the original signal. ...
... • CDMA (Code-Division Multiple-Access) is a "spread spectrum" technology, which means that it spreads the information contained in a particular signal of interest over a much greater bandwidth than the original signal. ...
From Analog to Digital - Multi
... As analog networks phase out, broadband have limited data capacity. Since digital lines transform and wireless networks are filling in to improve coverage. the signal into binary code, this allows for more data to Rural customers still need a reliable communication lifeline. be transmitted. Because ...
... As analog networks phase out, broadband have limited data capacity. Since digital lines transform and wireless networks are filling in to improve coverage. the signal into binary code, this allows for more data to Rural customers still need a reliable communication lifeline. be transmitted. Because ...
cellular - D
... media transport as well as high-capacity voice support for the next decade. Enables operators to offer high performance, massmarket mobile broadband services – high bit-rates, high system throughput (uplink and downlink), low latency. Designed to be simple to deploy and operate, through flexible ...
... media transport as well as high-capacity voice support for the next decade. Enables operators to offer high performance, massmarket mobile broadband services – high bit-rates, high system throughput (uplink and downlink), low latency. Designed to be simple to deploy and operate, through flexible ...
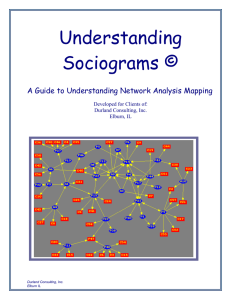
Understanding Sociograms
... Cutpoints and bridges are important for locating individuals who may be helpful for increasing the strength of the network. Even without knowing the individuals, knowing that the network tends to form loosely linked subgroups would facilitate in planning how to develop and enhance communication proc ...
... Cutpoints and bridges are important for locating individuals who may be helpful for increasing the strength of the network. Even without knowing the individuals, knowing that the network tends to form loosely linked subgroups would facilitate in planning how to develop and enhance communication proc ...
Lecture 01
... Frames are broadcast into coaxial cable NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
... Frames are broadcast into coaxial cable NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
Data Communication & Networking
... Privacy or security(every message travels along a dedicated line, only the intended recipient sees it. Physical boundaries prevents other user from gaining access the message eliminating the traffic problems. The use of dedicated links guarantees that each connection can carry its own data load; ...
... Privacy or security(every message travels along a dedicated line, only the intended recipient sees it. Physical boundaries prevents other user from gaining access the message eliminating the traffic problems. The use of dedicated links guarantees that each connection can carry its own data load; ...