PDF - Complete Book (3.38 MB)
... built with an equivalent API called the XML API. This API works by sending and receiving XML documents over an HTTP connection. This scheme allows the use of any programming language with the ability to create and parse XML and handle HTTP connections. Languages such as Perl or ASP in conjunction wi ...
... built with an equivalent API called the XML API. This API works by sending and receiving XML documents over an HTTP connection. This scheme allows the use of any programming language with the ability to create and parse XML and handle HTTP connections. Languages such as Perl or ASP in conjunction wi ...
Malware Removal Guide
... A File infector virus when executed on a system will seek out other files and insert its code into them. The programs with .EXE and .COM extensions are the most commonly targeted, but a file infector virus can target any executable file. When the application is started, the infection is executed and ...
... A File infector virus when executed on a system will seek out other files and insert its code into them. The programs with .EXE and .COM extensions are the most commonly targeted, but a file infector virus can target any executable file. When the application is started, the infection is executed and ...
TCP/UDP Sockets
... – (family, string_ptr, address_ptr) – Convert IP address string to network byte ordered 32 or 128 bit value – 1 on success, -1 on failure, 0 on invalid input ...
... – (family, string_ptr, address_ptr) – Convert IP address string to network byte ordered 32 or 128 bit value – 1 on success, -1 on failure, 0 on invalid input ...
TCP/UDP Sockets
... – (family, string_ptr, address_ptr) – Convert IP address string to network byte ordered 32 or 128 bit value – 1 on success, -1 on failure, 0 on invalid input ...
... – (family, string_ptr, address_ptr) – Convert IP address string to network byte ordered 32 or 128 bit value – 1 on success, -1 on failure, 0 on invalid input ...
International Technical Support Organization Connectivity on a PC
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1996. All rights reserved. Note to U.S. Government Users — Do ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1996. All rights reserved. Note to U.S. Government Users — Do ...
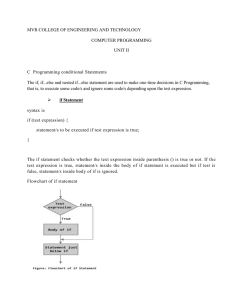
C Programming conditional Statements
... Output Enter name: Dennis Ritchie Your name is Dennis. Here, program will ignore Ritchie because, scanf() function takes only string before the white space. ...
... Output Enter name: Dennis Ritchie Your name is Dennis. Here, program will ignore Ritchie because, scanf() function takes only string before the white space. ...
Combining Events And Threads For Scalable
... Such massively-concurrent programs are difficult to implement, especially when other requirements, such as high performance and strong security, must also be met. Events vs. threads: Two implementation strategies for building such inherently concurrent systems have been successful. Both the multithr ...
... Such massively-concurrent programs are difficult to implement, especially when other requirements, such as high performance and strong security, must also be met. Events vs. threads: Two implementation strategies for building such inherently concurrent systems have been successful. Both the multithr ...
04-Sockets - Computer Science Division
... API: set of function types, data structures and constants • Allows programmer to learn once, write anywhere • Greatly simplifies job of application programmer ...
... API: set of function types, data structures and constants • Allows programmer to learn once, write anywhere • Greatly simplifies job of application programmer ...
THE TAXONOMY OF BUGS 1. SYNOPSIS What are the possible
... assurance inspection process by using the methods that are most effective against the most important bugs. 8. If a test is passed, then some nightmares or parts of them go away. If a test is failed, then a nightmare is possible, but upon correcting the bug, it too goes away. Testing, then, gives you ...
... assurance inspection process by using the methods that are most effective against the most important bugs. 8. If a test is passed, then some nightmares or parts of them go away. If a test is failed, then a nightmare is possible, but upon correcting the bug, it too goes away. Testing, then, gives you ...
PDF - Complete Book (645.0 KB)
... firmware, setup BIOS and CIMC, configure RAID logical volume, install operating systems, and perform diagnostics on Cisco Rack servers. It is designed to run on one server at a time. You can launch the application through physical or virtual media. This section contains the following topics: ...
... firmware, setup BIOS and CIMC, configure RAID logical volume, install operating systems, and perform diagnostics on Cisco Rack servers. It is designed to run on one server at a time. You can launch the application through physical or virtual media. This section contains the following topics: ...
Proceedings of the 9th USENIX Security Symposium USENIX Association Denver, Colorado, USA
... cameras, and even game consoles are identi able. Many of these systems, like routers, are important parts of the Internet infrastructure, and compromising infrastructure is a more serious problem than compromising end hosts. Therefore a general mechanism to protect any system is needed. Some people ...
... cameras, and even game consoles are identi able. Many of these systems, like routers, are important parts of the Internet infrastructure, and compromising infrastructure is a more serious problem than compromising end hosts. Therefore a general mechanism to protect any system is needed. Some people ...
Web Application Development
... var str = new String("abcdef"); var ch = str.charAt(0); var index = str.indexOf("b", 0); if (index > 0) alert("Found at index: " + index); else alert("Not Found!"); ...
... var str = new String("abcdef"); var ch = str.charAt(0); var index = str.indexOf("b", 0); if (index > 0) alert("Found at index: " + index); else alert("Not Found!"); ...
B14 Apache Spark with IMS and DB2 data
... Analytics possible for those joined data sources Spark allows for caching and reusing the results which reduces the number of SQLs issued against the database ...
... Analytics possible for those joined data sources Spark allows for caching and reusing the results which reduces the number of SQLs issued against the database ...
ITB255 - ABAP/4 Programming
... in a runtime error (eg, inconsistent interface parameters) warns about use of literals instead of text elements ...
... in a runtime error (eg, inconsistent interface parameters) warns about use of literals instead of text elements ...
threads
... Questions on the poor man’s approach Does it work for high-performance network services? (using a pure, lazy, functional language?) ...
... Questions on the poor man’s approach Does it work for high-performance network services? (using a pure, lazy, functional language?) ...
scons
... extension based on the system the software is being built. This would result in something like this being executed: cc -o hello -L. -lm -lpthread ...
... extension based on the system the software is being built. This would result in something like this being executed: cc -o hello -L. -lm -lpthread ...
well there`s a language called Go
... where users also have access to object-oriented style structures. Compiling to LLVM: - Compiling to LLVM allows for cross-language integrations that would allow a user to combine the functionality of Stop with a library from C. ...
... where users also have access to object-oriented style structures. Compiling to LLVM: - Compiling to LLVM allows for cross-language integrations that would allow a user to combine the functionality of Stop with a library from C. ...
Java Stored Procedures - Getting the Environment Ready
... DSNTIJSG – creates various stored procedures (grant execute to PUBLIC) SQLJ.DB2_INSTALL_JAR, SQLJ.DB2_REPLACE_JAR SQLJ.DB2_REMOVE_JAR SQLJ.DB2_UPDATEJARINFO DSNJDBC and DSNJAR collection’s perform GRANT CREATE ON COLLECTION… as necessary DSNTIJMS – creates additional indexes and catalog objects (may ...
... DSNTIJSG – creates various stored procedures (grant execute to PUBLIC) SQLJ.DB2_INSTALL_JAR, SQLJ.DB2_REPLACE_JAR SQLJ.DB2_REMOVE_JAR SQLJ.DB2_UPDATEJARINFO DSNJDBC and DSNJAR collection’s perform GRANT CREATE ON COLLECTION… as necessary DSNTIJMS – creates additional indexes and catalog objects (may ...
TDC561 Network Programming
... Need an IP address, protocol and port. – often use host names instead of IP addresses. – usually the protocol (UDP vs. TCP) is not specified by the user. – often the port is not specified by the user. ...
... Need an IP address, protocol and port. – often use host names instead of IP addresses. – usually the protocol (UDP vs. TCP) is not specified by the user. – often the port is not specified by the user. ...
Introduction to Linux Network
... Linux Networking Layers BSD Socket Interface INET Socket Interface An Example of Socket Programming ...
... Linux Networking Layers BSD Socket Interface INET Socket Interface An Example of Socket Programming ...
Integrating Interchangeable Virtual Instruments _IVI_ Resources
... New software technologies such as VISA and IVI continue to bring the industry towards greater standardization and interchangeability. The benefit to the integrator is reduced costs through reuse of the same hardware and software. The benefit to the customer end-user is lower costs by reducing modifi ...
... New software technologies such as VISA and IVI continue to bring the industry towards greater standardization and interchangeability. The benefit to the integrator is reduced costs through reuse of the same hardware and software. The benefit to the customer end-user is lower costs by reducing modifi ...
Lecture 1: Verilog HDL Introduction
... What is VHDL? • VHDL represents another high level language for digital system design. • In this course we study Verilog HDL – reason: • used more often in electronic and computer industry • programming style is very similar to C programming language ...
... What is VHDL? • VHDL represents another high level language for digital system design. • In this course we study Verilog HDL – reason: • used more often in electronic and computer industry • programming style is very similar to C programming language ...
Introduction
... over the internet. An application sends a packet trough a socket addressed to a certain IP number and port. There should be another application on that host listening to packets coming to that port (which is agreed beforehand) • TCP simulates a data flow. A client must establish a communication with ...
... over the internet. An application sends a packet trough a socket addressed to a certain IP number and port. There should be another application on that host listening to packets coming to that port (which is agreed beforehand) • TCP simulates a data flow. A client must establish a communication with ...
Lecture 1: Verilog HDL Introduction
... What is VHDL? • VHDL represents another high level language for digital system design. • In this course we study Verilog HDL – reason: • used more often in electronic and computer industry • programming style is very similar to C programming language ...
... What is VHDL? • VHDL represents another high level language for digital system design. • In this course we study Verilog HDL – reason: • used more often in electronic and computer industry • programming style is very similar to C programming language ...