The Third International Conference on Case
... CBR Strategies for Building and Maintaining Corporate Memories’’ was also concerned with the business environment but focused instead on methodologies for knowledge management. “Formalization of Adaptation in CBR’’ addressed the most complex aspect of CBR: adaptation of prior solutions to solve new ...
... CBR Strategies for Building and Maintaining Corporate Memories’’ was also concerned with the business environment but focused instead on methodologies for knowledge management. “Formalization of Adaptation in CBR’’ addressed the most complex aspect of CBR: adaptation of prior solutions to solve new ...
Artificial Intelligence and Expert Systems
... Decision Support Systems and Intelligent Systems, Efraim Turban and Jay E. Aronson 6th ed, Copyright 2001, Prentice Hall, Upper Saddle River, NJ ...
... Decision Support Systems and Intelligent Systems, Efraim Turban and Jay E. Aronson 6th ed, Copyright 2001, Prentice Hall, Upper Saddle River, NJ ...
Computer Science (MS)
... The Master of Science (MS) in Computer Science provides students a strong foundation in the core computer science areas, together with advanced study of specialized topics in computing. Students work closely with faculty members and may select to complete either a thesis or project. The thesis optio ...
... The Master of Science (MS) in Computer Science provides students a strong foundation in the core computer science areas, together with advanced study of specialized topics in computing. Students work closely with faculty members and may select to complete either a thesis or project. The thesis optio ...
Sample chapter - Computer Science and Software Engineering
... One is cognitive economy, calling for grouping similar things together and giving them a name. The other principle is rather a recognition that the continuous world outside of the body is actually structured and forms natural discontinuities. Categories are then, economically, formed by objects that ...
... One is cognitive economy, calling for grouping similar things together and giving them a name. The other principle is rather a recognition that the continuous world outside of the body is actually structured and forms natural discontinuities. Categories are then, economically, formed by objects that ...
Reasoned Use of Expertise in Argumentation
... guarding against. But does this suggest that all appeals to expert authority in argument are fallacious? It should not. For taking into account the intelligent and informed opinion of a legitimate expert on a question that one needs to act upon may be reasonable in argument, if no better or more dir ...
... guarding against. But does this suggest that all appeals to expert authority in argument are fallacious? It should not. For taking into account the intelligent and informed opinion of a legitimate expert on a question that one needs to act upon may be reasonable in argument, if no better or more dir ...
Analysis of Machine Learning Techniques for Intrusion Detection
... Intrusions. There are many machine learning techniques used in Intrusion Detection System and they comprised single, hybrid and ensemble classifiers. Many resources have been used on various machine learning techniques. These techniques work very well for IDS but it is known that there is not even a ...
... Intrusions. There are many machine learning techniques used in Intrusion Detection System and they comprised single, hybrid and ensemble classifiers. Many resources have been used on various machine learning techniques. These techniques work very well for IDS but it is known that there is not even a ...
content - ITC Digital Library
... who have helped advance our thinking and practice. Historical facts can be sorted out and better understood, but more information gathering is necessary. This paper traces decision support applications and research studies related to model and data-oriented systems, management expert systems, multid ...
... who have helped advance our thinking and practice. Historical facts can be sorted out and better understood, but more information gathering is necessary. This paper traces decision support applications and research studies related to model and data-oriented systems, management expert systems, multid ...
Toward a truly personal computer
... Toward a truly personal computer Pattie Maes MIT Media Lab Firefly Network, Inc [email protected] ...
... Toward a truly personal computer Pattie Maes MIT Media Lab Firefly Network, Inc [email protected] ...
Physical symbol systems - Research Showcase @ CMU
... These constraints are far from precisely defined. Operationalizing the notion of self-awareness poses difficult problems, however critical it seems as a requirement. Even what constitutes the brain is open, moving over the last thirty years from an essentially neural view to one that includes macrom ...
... These constraints are far from precisely defined. Operationalizing the notion of self-awareness poses difficult problems, however critical it seems as a requirement. Even what constitutes the brain is open, moving over the last thirty years from an essentially neural view to one that includes macrom ...
$doc.title
... 39. Seif El-Nasr, M. and Wei, H. (2008). Exploring Non-Verbal Behaviors Using Acting Methods. International Conference on Interactive Storytelling, pp. 71-82. Full paper acceptance rate ...
... 39. Seif El-Nasr, M. and Wei, H. (2008). Exploring Non-Verbal Behaviors Using Acting Methods. International Conference on Interactive Storytelling, pp. 71-82. Full paper acceptance rate ...
Windows-2000 and system Administration
... Because shared printers are available to all users on the network, you might want to limit access for some users by assigning printer permissions. For example, you could give all non administrative users in a department the Print permission and all managers the Print and Manage Documents permissions ...
... Because shared printers are available to all users on the network, you might want to limit access for some users by assigning printer permissions. For example, you could give all non administrative users in a department the Print permission and all managers the Print and Manage Documents permissions ...
Next Previous Contents
... 2. First stage boot loader then loads the second stage boot loader. 3. Second stage boot loader allows user to choose what kernel to boot. 4. Chosen kernel then booted and devices are initialized. 5. Kernel then executes init process. ...
... 2. First stage boot loader then loads the second stage boot loader. 3. Second stage boot loader allows user to choose what kernel to boot. 4. Chosen kernel then booted and devices are initialized. 5. Kernel then executes init process. ...
5. Architecture of a Rule Based System for Medical Billing
... should not use terms like ‘programming’ rather use ‘developing’ or ‘building. Similarly instead of saying ‘rule programming languages’ we should say ‘rule development tools’. Rule based systems are suitable for domains with large and changing body of technical, task specific knowledge [6]. Similarly ...
... should not use terms like ‘programming’ rather use ‘developing’ or ‘building. Similarly instead of saying ‘rule programming languages’ we should say ‘rule development tools’. Rule based systems are suitable for domains with large and changing body of technical, task specific knowledge [6]. Similarly ...
Associative Algorithms for Computational Creativity
... Figure 2, with three main algorithmic components: a generator, a selector, and an externalizer, which interact to produce a culinary recipe. These components are fed by a database of domain knowledge and a way to organize this knowledge. It is important to note that in the system architecture, the e ...
... Figure 2, with three main algorithmic components: a generator, a selector, and an externalizer, which interact to produce a culinary recipe. These components are fed by a database of domain knowledge and a way to organize this knowledge. It is important to note that in the system architecture, the e ...
Enactive Artificial Intelligence
... (e.g. Berthouze & Ziemke 2003; Lungarella et al. 2003), and the dynamical systems approach to adaptive behavior and minimal cognition (e.g. Beer 2003; 1995). In other words, the embodied approach to AI1 has matured and managed to establish itself as a viable methodology for synthesizing and understa ...
... (e.g. Berthouze & Ziemke 2003; Lungarella et al. 2003), and the dynamical systems approach to adaptive behavior and minimal cognition (e.g. Beer 2003; 1995). In other words, the embodied approach to AI1 has matured and managed to establish itself as a viable methodology for synthesizing and understa ...
IBM Presentations: Blue Pearl DeLuxe template
... The Problem: How do you know if DB2 is running okay, performing well? What do you do if you do manage to figure out it's "unhealthy"? Too difficult to determine what to monitor and when to monitor it Need to set up monitors, notification & resolution mechanisms ...
... The Problem: How do you know if DB2 is running okay, performing well? What do you do if you do manage to figure out it's "unhealthy"? Too difficult to determine what to monitor and when to monitor it Need to set up monitors, notification & resolution mechanisms ...
AI in chemometrics
... • Determination of the configuration of some systems (for example C60) • The composition of complex materials (for example composites) • Molecular structure optimization • Protein folding (3D structure of proteins) ...
... • Determination of the configuration of some systems (for example C60) • The composition of complex materials (for example composites) • Molecular structure optimization • Protein folding (3D structure of proteins) ...
The Limits of OCR
... Udi Manber asked Prof. Manuel Blum’s group at CMU: – programs impersonate people in chat rooms, then hand out ads – ugh! – how can all machines be denied access to a Web site ...
... Udi Manber asked Prof. Manuel Blum’s group at CMU: – programs impersonate people in chat rooms, then hand out ads – ugh! – how can all machines be denied access to a Web site ...
Chapter 15: Is Artificial Intelligence Real?
... With respect to neural networks, all of the following are true EXCEPT: A. neural networks distribute knowledge throughout the network. B. neural networks store information in the same way as traditional computers. C. neural networks use distributed, parallel computing systems. D. neural networks con ...
... With respect to neural networks, all of the following are true EXCEPT: A. neural networks distribute knowledge throughout the network. B. neural networks store information in the same way as traditional computers. C. neural networks use distributed, parallel computing systems. D. neural networks con ...
Organisational Intelligence and Distributed AI
... -7b) The information processing system supports the processing of data, information and knowledge in order to produce decisions that fit with the organisational aims and objectives. The information processing system does not necessarily involve information processing technology. c) In general, deci ...
... -7b) The information processing system supports the processing of data, information and knowledge in order to produce decisions that fit with the organisational aims and objectives. The information processing system does not necessarily involve information processing technology. c) In general, deci ...
The Robots Must Be Crazy: DSM TURING TEST
... The other most common issue is lack of agent training. Scripting and monitoring are powerful tools, but it is still critical to implement best practices for training agents in the basics of phone etiquette. ! ...
... The other most common issue is lack of agent training. Scripting and monitoring are powerful tools, but it is still critical to implement best practices for training agents in the basics of phone etiquette. ! ...
Analyzing Impact of AI Tools on Traditional Workflow Systems
... in almost every domain. Winston defines the Artificial Intelligence as “the study of computations that make it possible to perceive reason and act”. [3] The objective of Artificial Intelligence community to develop Intelligent Systems which are capable enough to achieve complex tasks in dynamic and ...
... in almost every domain. Winston defines the Artificial Intelligence as “the study of computations that make it possible to perceive reason and act”. [3] The objective of Artificial Intelligence community to develop Intelligent Systems which are capable enough to achieve complex tasks in dynamic and ...
word office version - European Parliament
... user, etc.); whereas this, in turn, questions whether the ordinary rules on liability are sufficient or whether it calls for new principles and rules to provide clarity on the legal liability of various actors concerning responsibility for the acts and omissions of robots where the cause cannot be ...
... user, etc.); whereas this, in turn, questions whether the ordinary rules on liability are sufficient or whether it calls for new principles and rules to provide clarity on the legal liability of various actors concerning responsibility for the acts and omissions of robots where the cause cannot be ...
... WARNING. On having consulted this thesis you’re accepting the following use conditions: Spreading this thesis by the TDX (www.tesisenxarxa.net) service has been authorized by the titular of the intellectual property rights only for private uses placed in investigation and teaching activities. Reprod ...
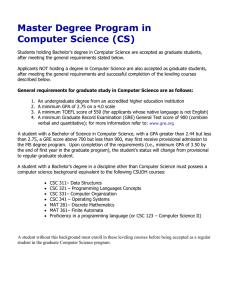
Master Degree Program in Computer Science (CS)
... practical aspects of operating systems: overview of system software, time-sharing and multiprogramming operating systems, network operating systems and the Internet, virtual memory management, inter-process communication and synchronization, file organization, and case studies. Giving advanced topic ...
... practical aspects of operating systems: overview of system software, time-sharing and multiprogramming operating systems, network operating systems and the Internet, virtual memory management, inter-process communication and synchronization, file organization, and case studies. Giving advanced topic ...