Applying Global Workspace Theory to the Frame Problem
... known algorithms are O(2 n), even though polynomial-time algorithms exist for verifying the correctness of a given solution to the problem. This class of problems is denoted NP, and any task that falls into this class is said to be computationally intractable. The best known of these is the so-calle ...
... known algorithms are O(2 n), even though polynomial-time algorithms exist for verifying the correctness of a given solution to the problem. This class of problems is denoted NP, and any task that falls into this class is said to be computationally intractable. The best known of these is the so-calle ...
Architectures and Idioms: Making Progress in Agent Design
... In this chapter we propose a meta-methodological strategy for the problem of incorporating the advances of new architectures into established development efforts. Our proposal is simple: a researcher, after having developed a new architecture, should express its major contributions in terms of one o ...
... In this chapter we propose a meta-methodological strategy for the problem of incorporating the advances of new architectures into established development efforts. Our proposal is simple: a researcher, after having developed a new architecture, should express its major contributions in terms of one o ...
Information Technology and Artificial Intelligence
... human. There is a strong sense of connection and resonance with this machine. As Michael Dertouzos notes the computer is the first type of technology directly related to learning, knowledge, and communication.2 Since it is our nervous system that supports the highly enhanced and flexible power of t ...
... human. There is a strong sense of connection and resonance with this machine. As Michael Dertouzos notes the computer is the first type of technology directly related to learning, knowledge, and communication.2 Since it is our nervous system that supports the highly enhanced and flexible power of t ...
Anytime A* Algorithm – An Extension to A* Algorithm
... A* is probably one of the most well known Artificial Intelligence Algorithms[1, 20]. Its objective is to find the shortest path in a graph from a node x-start to a node x-goal[13]. It combines the features of uniform-cost search and pure heuristic search to efficiently compute optimal solutions. As ...
... A* is probably one of the most well known Artificial Intelligence Algorithms[1, 20]. Its objective is to find the shortest path in a graph from a node x-start to a node x-goal[13]. It combines the features of uniform-cost search and pure heuristic search to efficiently compute optimal solutions. As ...
Towards a Programming Paradigm for Artificial Intelligence
... agents as in an agent-based approach. Other applications are hypothetical reasoning or realising different granularities of abstraction for efficiency (see Section 3). A world contains a set of named entities which are the primary artifacts of SBP and represent the subjects of the simulation. Entiti ...
... agents as in an agent-based approach. Other applications are hypothetical reasoning or realising different granularities of abstraction for efficiency (see Section 3). A world contains a set of named entities which are the primary artifacts of SBP and represent the subjects of the simulation. Entiti ...
IUI 2015: ACM International Conference on Intelligent User
... feel they would benefit from this kind of feedback on their research to apply for this unique opportunity to share their work with students in a similar situation as well as senior researchers in the field. The strongest candidates will be those who have a clear topic and research approach, and have ...
... feel they would benefit from this kind of feedback on their research to apply for this unique opportunity to share their work with students in a similar situation as well as senior researchers in the field. The strongest candidates will be those who have a clear topic and research approach, and have ...
Case Study for Information Management (資訊管理個案)
... reasoning, fuzzy logic – Knowledge discovery: Neural networks and data mining – Generating solutions to complex problems: Genetic algorithms – Automating tasks: Intelligent agents ...
... reasoning, fuzzy logic – Knowledge discovery: Neural networks and data mining – Generating solutions to complex problems: Genetic algorithms – Automating tasks: Intelligent agents ...
Heuristics, Planning and Cognition
... GPS, the first AI planner introduced by Newell, Shaw, and Simon, used a technique called means-ends analysis where differences between the current state and the goal situation were identified and mapped into operators that could decrease those differences [Newell and Simon 1963]. Since then, the ide ...
... GPS, the first AI planner introduced by Newell, Shaw, and Simon, used a technique called means-ends analysis where differences between the current state and the goal situation were identified and mapped into operators that could decrease those differences [Newell and Simon 1963]. Since then, the ide ...
An Analytical Study of the Remote Sensing Image Classification
... Firefly Algorithm etc. Swarm Intelligence is a global research area to improve the optimization of various soft computing and nature inspired techniques. In this paper, we are using these swarm intelligence based techniques for the accurately classification of land cover features. For this classific ...
... Firefly Algorithm etc. Swarm Intelligence is a global research area to improve the optimization of various soft computing and nature inspired techniques. In this paper, we are using these swarm intelligence based techniques for the accurately classification of land cover features. For this classific ...
Chapter 6 - Expert Systems and knowledge
... ES that performs tasks which no human expert has, using perhaps a very complex set of rules to control a chemical process at a speed and in circumstances (e.g. temperature, time, location) which no human could possibly match. Such a system will most surely outperform the best human expert. ...
... ES that performs tasks which no human expert has, using perhaps a very complex set of rules to control a chemical process at a speed and in circumstances (e.g. temperature, time, location) which no human could possibly match. Such a system will most surely outperform the best human expert. ...
Case-Based Plan Adaptation: An Analysis and Review
... changes where appropriate (Carbonell, 1983; van der Krogt & de Weerdt, 2005). Transformation operators are knowledge constructs prescribing how to transform existing plans into new ones. In the CBP system CHEF, for example, a transformational operator will indicate that raspberries will be a good su ...
... changes where appropriate (Carbonell, 1983; van der Krogt & de Weerdt, 2005). Transformation operators are knowledge constructs prescribing how to transform existing plans into new ones. In the CBP system CHEF, for example, a transformational operator will indicate that raspberries will be a good su ...
Specifying and Verifying Distributed Intelligent Systems
... they are often called). Over the past decade, many frameworks for building and experimenting with DAI systems have been reported. Probably the best-known is MACE, a LISP-based fully instrumented testbed for building DAI systems at a range of sizes and complexity [19]. Other testbeds include Georgeff ...
... they are often called). Over the past decade, many frameworks for building and experimenting with DAI systems have been reported. Probably the best-known is MACE, a LISP-based fully instrumented testbed for building DAI systems at a range of sizes and complexity [19]. Other testbeds include Georgeff ...
PDF - (FAI) Group
... is true. Therefore, {(q ∧ f1 ), . . . , (q ∧ fn )} are mutexes too and whenever (¬p ∧ q) is true, at least one of those mutexes is violated. In SAS+ , fluents that do not belong to an “exactly-1” invariant group will be grouped with a hnone of thosei fluent. Therefore, the negation of the fluents of ...
... is true. Therefore, {(q ∧ f1 ), . . . , (q ∧ fn )} are mutexes too and whenever (¬p ∧ q) is true, at least one of those mutexes is violated. In SAS+ , fluents that do not belong to an “exactly-1” invariant group will be grouped with a hnone of thosei fluent. Therefore, the negation of the fluents of ...
Lecture 1 - Computer Science
... • Branch of computer science which • is the science of making machines do things that would require intelligence if done by men (Minsky) • is the exciting new effort to make computers think (Haugeland) • is the study of the computations that make it possible to perceive, reason, and act (Winston) • ...
... • Branch of computer science which • is the science of making machines do things that would require intelligence if done by men (Minsky) • is the exciting new effort to make computers think (Haugeland) • is the study of the computations that make it possible to perceive, reason, and act (Winston) • ...
Negative Introspection Is Mysterious
... you will immediately know that γ does not follow from α (given your other beliefs as well)! As we ordinary humans also have false beliefs this does not amount to a decision procedure, but if some cognitive agent had no contingent beliefs at all, but fulfilled both the closure principles and the intr ...
... you will immediately know that γ does not follow from α (given your other beliefs as well)! As we ordinary humans also have false beliefs this does not amount to a decision procedure, but if some cognitive agent had no contingent beliefs at all, but fulfilled both the closure principles and the intr ...
Welcome to IJCAI 2015!
... media. Researchers across the globe report huge interest in AI, particularly in areas like machine learning. But of course, this excitement has been tempered by concern from well-known scientists about the potential dangers posed by AI. We look forward to discussing all these issues with you through ...
... media. Researchers across the globe report huge interest in AI, particularly in areas like machine learning. But of course, this excitement has been tempered by concern from well-known scientists about the potential dangers posed by AI. We look forward to discussing all these issues with you through ...
Relational Learning as Search in a Critical Region
... of a phase transition in the covering test has much deeper and far reaching effects on the feasibility of relational learning than just this increase in computational cost. Preliminary results in this new direction have been presented by Giordana, Saitta, Sebag, and Botta (2000). The emergence of a ...
... of a phase transition in the covering test has much deeper and far reaching effects on the feasibility of relational learning than just this increase in computational cost. Preliminary results in this new direction have been presented by Giordana, Saitta, Sebag, and Botta (2000). The emergence of a ...
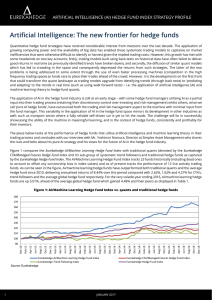
Artificial Intelligence: The new frontier for hedge funds
... Quantitative hedge fund strategies have received considerable interest from investors over the last decade. The application of growing computing power and the availability of big data has enabled these systematic trading models to capitalise on market inefficiencies that were otherwise difficult to ...
... Quantitative hedge fund strategies have received considerable interest from investors over the last decade. The application of growing computing power and the availability of big data has enabled these systematic trading models to capitalise on market inefficiencies that were otherwise difficult to ...
Dr. Mark Silbert
... • Intelligence is those tasks that only a human can do • But once we figure out how to make a computer do that task, it is no longer considered AI • Thus, AI is that which we have not yet figured out how to program a computer to do… ...
... • Intelligence is those tasks that only a human can do • But once we figure out how to make a computer do that task, it is no longer considered AI • Thus, AI is that which we have not yet figured out how to program a computer to do… ...
Seminar Slides - CSE, IIT Bombay
... Patterns need not be ordered alphabetically The matching is word-by-word, not category-bycategory Highly restricted form of depth-first search ...
... Patterns need not be ordered alphabetically The matching is word-by-word, not category-bycategory Highly restricted form of depth-first search ...