General Introduction to SPSS
... – A numeric variable whose values are displayed with periods delimiting every three places and with the comma as a decimal delimiter. – The Data Editor accepts numeric values for dot variables with or without periods, or in scientific ...
... – A numeric variable whose values are displayed with periods delimiting every three places and with the comma as a decimal delimiter. – The Data Editor accepts numeric values for dot variables with or without periods, or in scientific ...
Comparative Evaluation of Predictive Modeling Techniques on
... world data sets : Australian and German. He employed 10 fold cross validation for enhancing his predictive power. He reported both good credit and bad credit rates. He benchmarked the results against five other traditional methods including linear discriminant analysis, logistic regression, k neares ...
... world data sets : Australian and German. He employed 10 fold cross validation for enhancing his predictive power. He reported both good credit and bad credit rates. He benchmarked the results against five other traditional methods including linear discriminant analysis, logistic regression, k neares ...
Chapter 8: Dynamic Programming
... Several coins are placed in cells of an n×m board. A robot, located in the upper left cell of the board, needs to collect as many of the coins as possible and bring them to the bottom right cell. On each step, the robot can move either one cell to the right or one cell down from its current location ...
... Several coins are placed in cells of an n×m board. A robot, located in the upper left cell of the board, needs to collect as many of the coins as possible and bring them to the bottom right cell. On each step, the robot can move either one cell to the right or one cell down from its current location ...
Subgroup Discovery in Defect Prediction
... heuristic search (best first) to search for candidate feature subsets. • One of the most frequently used search techniques is hill-climbing (greedy). It starts with an empty set and evaluates each attribute individually to find the best single attribute. It then tries each of the remaining attribute ...
... heuristic search (best first) to search for candidate feature subsets. • One of the most frequently used search techniques is hill-climbing (greedy). It starts with an empty set and evaluates each attribute individually to find the best single attribute. It then tries each of the remaining attribute ...
Optimization of (s, S) Inventory Systems with Random Lead Times
... cost K = 36, and the per period holding cost h = 1, and if Q is computed using the EOQ formula, then their algorithm is valid only when the average demand per period is less than or equal to 32. Moreover, when orders are allowed to cross, our simulation results indicate that the approximation method ...
... cost K = 36, and the per period holding cost h = 1, and if Q is computed using the EOQ formula, then their algorithm is valid only when the average demand per period is less than or equal to 32. Moreover, when orders are allowed to cross, our simulation results indicate that the approximation method ...
Using Tree Augmented Naive Bayesian Classifiers to Improve Engine Fault Models
... these additional monitors fire, f mi without that monitor in S − DMi are removed from the AG. Over time as the monitors fire, AG reduces in size, and ideally, to a single f mi . Additional details about the reasoning algorithm is described in (Honeywell, 2010). The reasoning algorithm generates mult ...
... these additional monitors fire, f mi without that monitor in S − DMi are removed from the AG. Over time as the monitors fire, AG reduces in size, and ideally, to a single f mi . Additional details about the reasoning algorithm is described in (Honeywell, 2010). The reasoning algorithm generates mult ...
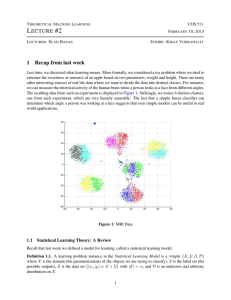
L #2 1 Recap from last week
... If we compare this result to Theorem 1.8, we note that |H| kind of behaves the way 1 does in this derivation. We also note that there is only one continuous parameter involved, r · · · Let us do another example to see if this intuition holds up. Example 3.3. Infinitely many rectangles. Let us revis ...
... If we compare this result to Theorem 1.8, we note that |H| kind of behaves the way 1 does in this derivation. We also note that there is only one continuous parameter involved, r · · · Let us do another example to see if this intuition holds up. Example 3.3. Infinitely many rectangles. Let us revis ...
End-to-end Estimation of Available Bandwidth Variation Range
... Applications of bandwidth estimation: Overlay routing and multihoming: path selection algorithms, avoidance of oscillations, provisioning ...
... Applications of bandwidth estimation: Overlay routing and multihoming: path selection algorithms, avoidance of oscillations, provisioning ...
Mining Quantitative Maximal Hyperclique Patterns: A
... algorithm for finding association rules in data with continuous attributes. Technical report, Department of Computer Science, University of Minnesota, 1997. 5. Y. Huang, H. Xiong, W. Wu, and Z. Zhang. A hybrid approach for mining maximal hyperclique patterns. In ICTAI, 2004. 6. J.Han, J.Pei, and Y. ...
... algorithm for finding association rules in data with continuous attributes. Technical report, Department of Computer Science, University of Minnesota, 1997. 5. Y. Huang, H. Xiong, W. Wu, and Z. Zhang. A hybrid approach for mining maximal hyperclique patterns. In ICTAI, 2004. 6. J.Han, J.Pei, and Y. ...
Constructing Statistical Tolerance Limits for Non
... • If X does not follow a normal distribution, it may be possible to find a power p such that Xp is normally distributed. • If so, normal tolerance limits may be constructed for Xp and then inverted to create limits for X. • The general method of Box and Cox may be used to find the best value of p. ...
... • If X does not follow a normal distribution, it may be possible to find a power p such that Xp is normally distributed. • If so, normal tolerance limits may be constructed for Xp and then inverted to create limits for X. • The general method of Box and Cox may be used to find the best value of p. ...
CHAPTER 8A: GLOBAL DESCRIPTIVE MODELS (DAVID AND
... chapters - for example, in Section 5.1XXX. As well as distinguishing between models and patterns, earlier chapters also noted the distinction between descriptive and predictive models. A descriptive model presents, in convenient form, the main features of the data. It is, essentially a summary of th ...
... chapters - for example, in Section 5.1XXX. As well as distinguishing between models and patterns, earlier chapters also noted the distinction between descriptive and predictive models. A descriptive model presents, in convenient form, the main features of the data. It is, essentially a summary of th ...
Expectation–maximization algorithm

In statistics, an expectation–maximization (EM) algorithm is an iterative method for finding maximum likelihood or maximum a posteriori (MAP) estimates of parameters in statistical models, where the model depends on unobserved latent variables. The EM iteration alternates between performing an expectation (E) step, which creates a function for the expectation of the log-likelihood evaluated using the current estimate for the parameters, and a maximization (M) step, which computes parameters maximizing the expected log-likelihood found on the E step. These parameter-estimates are then used to determine the distribution of the latent variables in the next E step.