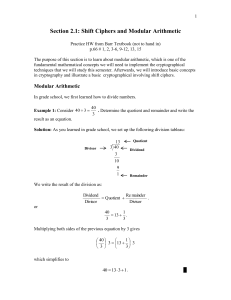
Section2.1notesall
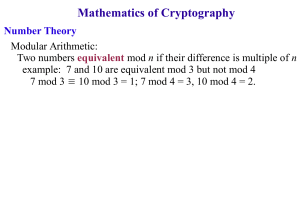
... deciphering a message. This leads to an important question. How can we decipher a message in a shift cipher if we do not know the key k ? Cryptanalysis is the process of trying to break a cipher by finding its key. Cryptanalysis in general is not an easy problem. The more secure a cipher is, the har ...
... deciphering a message. This leads to an important question. How can we decipher a message in a shift cipher if we do not know the key k ? Cryptanalysis is the process of trying to break a cipher by finding its key. Cryptanalysis in general is not an easy problem. The more secure a cipher is, the har ...
Fast Variants of RSA
... RSA [11] is the most widely deployed public key cryptosystem. It is used for securing web traffic, e-mail, and some wireless devices. Since RSA is based on arithmetic modulo large numbers it can be slow in constrained environments. For example, 1024-bit RSA decryption on a small handheld device such ...
... RSA [11] is the most widely deployed public key cryptosystem. It is used for securing web traffic, e-mail, and some wireless devices. Since RSA is based on arithmetic modulo large numbers it can be slow in constrained environments. For example, 1024-bit RSA decryption on a small handheld device such ...
22C:19 Discrete Math
... In general, for Caesar Cipher, let p = plain text c= cipher text, k = encryption key The encryption algorithm is c = p + k mod 26 The decryption algorithm is p = c - k mod 26 Both parties must share a common secret key. ...
... In general, for Caesar Cipher, let p = plain text c= cipher text, k = encryption key The encryption algorithm is c = p + k mod 26 The decryption algorithm is p = c - k mod 26 Both parties must share a common secret key. ...
Introduction to Number Theory 2
... large primes are not too rare, so it is not too time consuming to test random integers of the appropriate size until a prime is found. The prime number function π(n) specifies the number of primes that are less than or equal n. Examples: π(10) = 4. ...
... large primes are not too rare, so it is not too time consuming to test random integers of the appropriate size until a prime is found. The prime number function π(n) specifies the number of primes that are less than or equal n. Examples: π(10) = 4. ...
Analysis of Algorithms
... • Caesar’s cipher is an example of a monoalphabetic substitution cipher, which permutes the characters • Armed with simple statistical knowledge, one can easily break a monoalphabetic substitution cipher – most frequent letters in English: e, t, o, a, n, i, ... – most frequent digrams: th, in, er, r ...
... • Caesar’s cipher is an example of a monoalphabetic substitution cipher, which permutes the characters • Armed with simple statistical knowledge, one can easily break a monoalphabetic substitution cipher – most frequent letters in English: e, t, o, a, n, i, ... – most frequent digrams: th, in, er, r ...
Integers, Modular Arithmetic and Cryptography
... In general, for Caesar Cipher, let p = plain text c= cipher text, k = encryption key The encryption algorithm is c = p + k mod 26 The decryption algorithm is p = c - k mod 26 Both parties must share a common secret key. ...
... In general, for Caesar Cipher, let p = plain text c= cipher text, k = encryption key The encryption algorithm is c = p + k mod 26 The decryption algorithm is p = c - k mod 26 Both parties must share a common secret key. ...
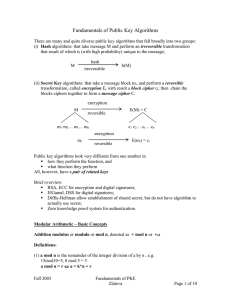
PKE Fundamentals
... How do these two sets differ from each other with respect to their relation to the number 10? Can we come up with some characteristics or pattern that allows to differentiate between the two sets? As operations mod n are all about divisibility properties of the number n it makes sense to look for th ...
... How do these two sets differ from each other with respect to their relation to the number 10? Can we come up with some characteristics or pattern that allows to differentiate between the two sets? As operations mod n are all about divisibility properties of the number n it makes sense to look for th ...
Document
... • Caesar’s cipher is an example of a monoalphabetic substitution cipher, which permutes the characters • Armed with simple statistical knowledge, one can easily break a monoalphabetic substitution cipher – most frequent letters in English: e, t, o, a, n, i, ... – most frequent digrams: th, in, er, r ...
... • Caesar’s cipher is an example of a monoalphabetic substitution cipher, which permutes the characters • Armed with simple statistical knowledge, one can easily break a monoalphabetic substitution cipher – most frequent letters in English: e, t, o, a, n, i, ... – most frequent digrams: th, in, er, r ...
Slides - FI MUNI
... For example, a 256-bit ECC public key should provide comparable security to a 3072-bit RSA public key. ECC is used for encryption, digital signatures and PRG. Security of ECC is based on infeasibility of computing discrete logarithms of random elliptic curves elements. In USA two of the most promine ...
... For example, a 256-bit ECC public key should provide comparable security to a 3072-bit RSA public key. ECC is used for encryption, digital signatures and PRG. Security of ECC is based on infeasibility of computing discrete logarithms of random elliptic curves elements. In USA two of the most promine ...
2×2 handouts
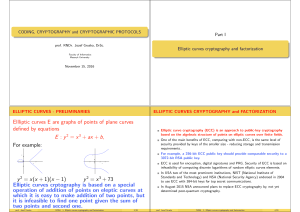
... All that holds for the case that λ 6= ∞; otherwise P3 = ∞. Example: For curve y 2 = x 3 + 73 and P1 = (2, 9), P2 = (3, 10) we have λ = 1, P1 + P2 = P3 = (−4, −3) and P3 + P3 = (72, 611). – {λ = −8} prof. Jozef Gruska ...
... All that holds for the case that λ 6= ∞; otherwise P3 = ∞. Example: For curve y 2 = x 3 + 73 and P1 = (2, 9), P2 = (3, 10) we have λ = 1, P1 + P2 = P3 = (−4, −3) and P3 + P3 = (72, 611). – {λ = −8} prof. Jozef Gruska ...
View File
... Any NP-complete problem can be used. In graph theory, if you know Hamiltonian cycle of a ...
... Any NP-complete problem can be used. In graph theory, if you know Hamiltonian cycle of a ...
TS 133 102 - V4.2.0 - Universal Mobile Telecommunications System
... Scope ........................................................................................................................................................7 ...
... Scope ........................................................................................................................................................7 ...
Part VIII Elliptic curves cryptography and factorization
... For j ∈ {0, . . . , K } verify whether for x = mK + j, x 3 + ax + b (mod p) is a square (mod p) of an integer y. If such an j is found, encoding is done; if not the algorithm fails (with probability because x 3 + ax + b is a square approximately half of the time). ...
... For j ∈ {0, . . . , K } verify whether for x = mK + j, x 3 + ax + b (mod p) is a square (mod p) of an integer y. If such an j is found, encoding is done; if not the algorithm fails (with probability because x 3 + ax + b is a square approximately half of the time). ...
is n
... 1- Firstly, if I were to encode the letter ‘A’ as a 0 then the encrypted result would be 0 whatever the key. Similarly, if ‘A’ were coded as a 1 and then encrypted by raising 1 to some power (that is, 1 multiplied by itself a number of times) the result would always be 1 so ‘A’ would, whatever key w ...
... 1- Firstly, if I were to encode the letter ‘A’ as a 0 then the encrypted result would be 0 whatever the key. Similarly, if ‘A’ were coded as a 1 and then encrypted by raising 1 to some power (that is, 1 multiplied by itself a number of times) the result would always be 1 so ‘A’ would, whatever key w ...
Chapter 10 Number Theory and Cryptography
... 10.1.5 Modular Multiplicative Inverses . . . . . . . . . . . . 10.1.6 Primality Testing . . . . . . . . . . . . . . . . . . . 10.2 Cryptographic Computations . . . . . . . . . . . . . . 10.2.1 Symmetric Encryption Schemes . . . . . . . . . . . . 10.2.2 Public-Key Cryptosystems . . . . . . . . . . . ...
... 10.1.5 Modular Multiplicative Inverses . . . . . . . . . . . . 10.1.6 Primality Testing . . . . . . . . . . . . . . . . . . . 10.2 Cryptographic Computations . . . . . . . . . . . . . . 10.2.1 Symmetric Encryption Schemes . . . . . . . . . . . . 10.2.2 Public-Key Cryptosystems . . . . . . . . . . . ...
Osma prednaska: Cryptography of eliptic curves, factorization
... verified by Bob: Alice chooses p and an elliptic curve E (mod p), a point P on E and calculates the number of points n on E (mod p) – what can be done, and we assume that 0 < m < n. Alice then chooses a secret a and computes Q = aP. Alice makes public p, E, P, Q and keeps secret a. To sign m Alice d ...
... verified by Bob: Alice chooses p and an elliptic curve E (mod p), a point P on E and calculates the number of points n on E (mod p) – what can be done, and we assume that 0 < m < n. Alice then chooses a secret a and computes Q = aP. Alice makes public p, E, P, Q and keeps secret a. To sign m Alice d ...
Osma prednaska: Cryptography of eliptic curves, factorization
... IV054 Factoring with Elliptic Curves Basis idea: To factorize an integer n choose an elliptic curve E, a point P on E and compute (modulo n) either iP for i=2,3,4,… or 2j P for j=1,2,…. The point is that in doing that one needs to compute gcd(k,n) for various k. If one of these values is between 1 ...
... IV054 Factoring with Elliptic Curves Basis idea: To factorize an integer n choose an elliptic curve E, a point P on E and compute (modulo n) either iP for i=2,3,4,… or 2j P for j=1,2,…. The point is that in doing that one needs to compute gcd(k,n) for various k. If one of these values is between 1 ...
Microsoft PowerPoint - file [jen pro \350ten\355]
... IV054 Factoring with Elliptic Curves Basis idea: To factorize an integer n choose an elliptic curve E, a point P on E and compute (modulo n) either iP for i=2,3,4,… or 2j P for j=1,2,…. The point is that in doing that one needs to compute gcd(k,n) for various k. If one of these values is between 1 ...
... IV054 Factoring with Elliptic Curves Basis idea: To factorize an integer n choose an elliptic curve E, a point P on E and compute (modulo n) either iP for i=2,3,4,… or 2j P for j=1,2,…. The point is that in doing that one needs to compute gcd(k,n) for various k. If one of these values is between 1 ...
X - FI MUNI
... IV054 Factoring with Elliptic Curves Basis idea: To factorize an integer n choose an elliptic curve E, a point P on E and compute (modulo n) either iP for i=2,3,4,… or 2j P for j=1,2,…. The point is that in doing that one needs to compute gcd(k,n) for various k. If one of these values is between 1 ...
... IV054 Factoring with Elliptic Curves Basis idea: To factorize an integer n choose an elliptic curve E, a point P on E and compute (modulo n) either iP for i=2,3,4,… or 2j P for j=1,2,…. The point is that in doing that one needs to compute gcd(k,n) for various k. If one of these values is between 1 ...
CMPE-552 Database and File Security
... 15.What are the main sources of security vulnerabilities of software? 16. How asymmetric encryption can be used for secure communication? 17. How asymmetric encryption can be used for establishing session key? 18. What is digital signature? What is hash (digest) function? What is one-way function? W ...
... 15.What are the main sources of security vulnerabilities of software? 16. How asymmetric encryption can be used for secure communication? 17. How asymmetric encryption can be used for establishing session key? 18. What is digital signature? What is hash (digest) function? What is one-way function? W ...
CMPE-552 Database and File Security
... 15.What are the main sources of security vulnerabilities of software? 16. How asymmetric encryption can be used for secure communication? 17. How asymmetric encryption can be used for establishing session key? 18. What is digital signature? What is hash (digest) function? What is one-way function? W ...
... 15.What are the main sources of security vulnerabilities of software? 16. How asymmetric encryption can be used for secure communication? 17. How asymmetric encryption can be used for establishing session key? 18. What is digital signature? What is hash (digest) function? What is one-way function? W ...
CMPE552 Problem Session
... If gcd(m,b)=1, then b has a multiplicative inverse modulo m. That is, for positive integer b
... If gcd(m,b)=1, then b has a multiplicative inverse modulo m. That is, for positive integer b
(pdf)
... Here, it is easy and possible to unmask 6601 as a composite number, unlike with the primality test using Fermat’s Little Theorem. In fact, this test was most widely used to find out if a large number was prime until 1999, with the advent of the AKS Test. This test was the first completely efficient ...
... Here, it is easy and possible to unmask 6601 as a composite number, unlike with the primality test using Fermat’s Little Theorem. In fact, this test was most widely used to find out if a large number was prime until 1999, with the advent of the AKS Test. This test was the first completely efficient ...









![Microsoft PowerPoint - file [jen pro \350ten\355]](http://s1.studyres.com/store/data/013242156_1-6d27a8b2fd52728ab8cdcdca733b5a2d-300x300.png)




