Airmesh The Flying Mesh Network
... provided a mean to organize help on a local basis, one example being connecting people with boats with people in need of a transport possibility. It has to be kept in mind that all these self-organizing procedures worked before Internet connectivity was common and by no means are dependent on such ...
... provided a mean to organize help on a local basis, one example being connecting people with boats with people in need of a transport possibility. It has to be kept in mind that all these self-organizing procedures worked before Internet connectivity was common and by no means are dependent on such ...
10Logan
... Flow Label : Request for special handling by routers within a network Payload Length : Length of the remainder of the packet following the IPv6 header Next Header : Type of header following the IPv6 header Hop Limit : Limitation for the impact of routing loops ...
... Flow Label : Request for special handling by routers within a network Payload Length : Length of the remainder of the packet following the IPv6 header Next Header : Type of header following the IPv6 header Hop Limit : Limitation for the impact of routing loops ...
Chapter 6
... • These include Serial Line Interface Protocol (SLIP) and Point-to-Point Protocol (PPP) • These are communication protocols for serial data transmission by which IP packets can be sent over a modem ...
... • These include Serial Line Interface Protocol (SLIP) and Point-to-Point Protocol (PPP) • These are communication protocols for serial data transmission by which IP packets can be sent over a modem ...
NetVM: High Performance and Flexible Networking Using
... to properly route packets through VMs based on mechanisms such as shallow (header-based) or deep (databased) packet analysis. At the same time, NetVM’s switch may use state-dependent information such as VM load levels, time of day, or dynamically configured policies to control the switching algorith ...
... to properly route packets through VMs based on mechanisms such as shallow (header-based) or deep (databased) packet analysis. At the same time, NetVM’s switch may use state-dependent information such as VM load levels, time of day, or dynamically configured policies to control the switching algorith ...
Analyzing Router Responsiveness to Measurement Probes
... if another responsive node appears later on within the same trace output. We define several anonymity types for nodes/routers that we observed in our experiments. Note that, both Type 1 and Type 2 can be further classified into two types. However, as an observer there is no difference between them. ...
... if another responsive node appears later on within the same trace output. We define several anonymity types for nodes/routers that we observed in our experiments. Note that, both Type 1 and Type 2 can be further classified into two types. However, as an observer there is no difference between them. ...
Overview of Switches
... devices such as computers, printers and servers that are present within a particular boundary like a campus or building. The switch is responsible for enabling communication between the networking devices on a Local area network (LAN) so that they could efficiently talk to each other. The greater ad ...
... devices such as computers, printers and servers that are present within a particular boundary like a campus or building. The switch is responsible for enabling communication between the networking devices on a Local area network (LAN) so that they could efficiently talk to each other. The greater ad ...
PPT - Apnic
... – Provides stability and consistency of routing – Data may be used by anyone worldwide to help debug, configure, and engineer Internet routing and addressing ...
... – Provides stability and consistency of routing – Data may be used by anyone worldwide to help debug, configure, and engineer Internet routing and addressing ...
M051055
... attached networks. Routers must also discover when their neighbors becomeunreachable or inoperative. This process is achieved with low overhead by periodically sendingsmall hello packets. As long as a router receives hello packets from a neighboring router, itassumes that the neighbor is functioning ...
... attached networks. Routers must also discover when their neighbors becomeunreachable or inoperative. This process is achieved with low overhead by periodically sendingsmall hello packets. As long as a router receives hello packets from a neighboring router, itassumes that the neighbor is functioning ...
Ch05-2 - LINK@KoreaTech
... store and forward Ethernet frames examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment transparent hosts are unaware of presence of switches plug-and-play, self-learning switches ...
... store and forward Ethernet frames examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment transparent hosts are unaware of presence of switches plug-and-play, self-learning switches ...
Moving beyond TCP/IP
... The NCP ARPANET is not today’s Internet. It was closer to what the public packet-switched networks that were developed in the 1970s called X.25. These networks were optimized for terminal-to-host applications. It was a dead-end technology that dominated European markets in the 1980s. But it was a F ...
... The NCP ARPANET is not today’s Internet. It was closer to what the public packet-switched networks that were developed in the 1970s called X.25. These networks were optimized for terminal-to-host applications. It was a dead-end technology that dominated European markets in the 1980s. But it was a F ...
Introduction to Classless Routing CCNA 3/Module 1 1
... 1.2.1 RIP History Internet is a collection of autonomous systems (AS) • Each AS is administered by a single entity • Each AS has its own routing technology Routing protocol used within AS is Interior Gateway Protocol Routing protocol used between Autonomous Systems is an Exterior Gateway Protocol R ...
... 1.2.1 RIP History Internet is a collection of autonomous systems (AS) • Each AS is administered by a single entity • Each AS has its own routing technology Routing protocol used within AS is Interior Gateway Protocol Routing protocol used between Autonomous Systems is an Exterior Gateway Protocol R ...
MN_12_Routing_Protocols_For_AdHoc_Networks
... A bandwidth efficient routing protocol for ad hoc networks A variation of table-driven routing protocols, with the Least Overhead Routing Approach (LORA) as the key concept rather than the Optimum Routing Approach (ORA) that was employed by the most of the table-driven routing protocols LORA p ...
... A bandwidth efficient routing protocol for ad hoc networks A variation of table-driven routing protocols, with the Least Overhead Routing Approach (LORA) as the key concept rather than the Optimum Routing Approach (ORA) that was employed by the most of the table-driven routing protocols LORA p ...
ppt
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet Upstream satellite communication 802.11 wireless LAN ...
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet Upstream satellite communication 802.11 wireless LAN ...
Chapter 4 Network Layer Network Layer Network layer functions
... packet belonging to VC carries VC number (rather than dest address) ❒ VC number can be changed on each link. ...
... packet belonging to VC carries VC number (rather than dest address) ❒ VC number can be changed on each link. ...
Advances in Natural and Applied Sciences
... operation, multi-hop communications, and mixed application-specific requirements. The huge majority of this revision applies to conservative WSN request which needs dependable and skilled message of scalar event kind and sensor information such as heat, force, moisture. With the ease of access of lo ...
... operation, multi-hop communications, and mixed application-specific requirements. The huge majority of this revision applies to conservative WSN request which needs dependable and skilled message of scalar event kind and sensor information such as heat, force, moisture. With the ease of access of lo ...
Part I: Introduction
... 17 else if (update received from V wrt destination Y) 18 /* shortest path from V to some Y has changed */ 19 /* V has sent a new value for its minw DV(Y,w) */ 20 /* call this received new value is "newval" */ 21 for the single destination y: D X(Y,V) = c(X,V) + newval ...
... 17 else if (update received from V wrt destination Y) 18 /* shortest path from V to some Y has changed */ 19 /* V has sent a new value for its minw DV(Y,w) */ 20 /* call this received new value is "newval" */ 21 for the single destination y: D X(Y,V) = c(X,V) + newval ...
Emulation of RDRN on an ATM-Testbed and a Comparative
... In the above case the segmentation of the packet passed by CLIP needs to be done. This is the reason why the ATM-like header is added by the “glue_layer” ...
... In the above case the segmentation of the packet passed by CLIP needs to be done. This is the reason why the ATM-like header is added by the “glue_layer” ...
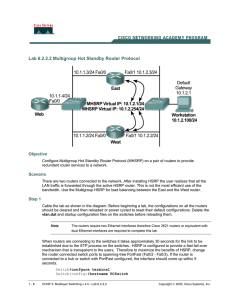
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
- 高速通訊與計算實驗室
... Vendor-specific interface Only vendors can develop for its constrained environments Various and complex protocols: OSPF, BGP, DiffServ, NAT, MPLS, and so on. No uniform standardization ...
... Vendor-specific interface Only vendors can develop for its constrained environments Various and complex protocols: OSPF, BGP, DiffServ, NAT, MPLS, and so on. No uniform standardization ...