cisco 2-11
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
PPT
... rate higher than 1Mbps assumed above); • PRINCIPLE 2: provide protection (isolation) for one class from other classes • Require Policing Mechanisms to ensure sources adhere to bandwidth requirements; Marking and Policing need to be done at the edges: ...
... rate higher than 1Mbps assumed above); • PRINCIPLE 2: provide protection (isolation) for one class from other classes • Require Policing Mechanisms to ensure sources adhere to bandwidth requirements; Marking and Policing need to be done at the edges: ...
hostv_infocom - Applied Research Laboratory
... the LAN environment has the same concerns and goals as the core network. The primary difference is the prevalence of multi-access networks and virtual end-systems. As with the core network, substrate links emulate physical links (point-topoint or multi-access), interconnect adjacent substrate nodes ...
... the LAN environment has the same concerns and goals as the core network. The primary difference is the prevalence of multi-access networks and virtual end-systems. As with the core network, substrate links emulate physical links (point-topoint or multi-access), interconnect adjacent substrate nodes ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... The IP layer of abstraction is mainly charged with delivering Internet Protocol (IP) packets from source to destination. In order to perform this task, the source and destination IP addresses are identified by unique fixed length addresses. In IPv4, a 32 bit numeric identifier was deemed sufficient ...
... The IP layer of abstraction is mainly charged with delivering Internet Protocol (IP) packets from source to destination. In order to perform this task, the source and destination IP addresses are identified by unique fixed length addresses. In IPv4, a 32 bit numeric identifier was deemed sufficient ...
Datagram
... . يمكن ان يستخدم في طريقتينcodepoint subfield • A. When the 3 rightmost bits are Os, the 3 leftmost bits are interpreted the same as the precedence bits in the service type interpretation. In other words, it is compatible with the old ...
... . يمكن ان يستخدم في طريقتينcodepoint subfield • A. When the 3 rightmost bits are Os, the 3 leftmost bits are interpreted the same as the precedence bits in the service type interpretation. In other words, it is compatible with the old ...
Migration Strategies for Token Ring Users
... As part of its overall strategy for integrating LAN technologies — including Token Ring, Ethernet, Fast Ethernet, FDDI and ATM — in IBM networks, 3Com has developed a technology based on the upcoming VLAN tagging IEEE 802.1Q standard — Token Ringin-Fast Ethernet (TR-in-FE). TR-in-FE technology simpl ...
... As part of its overall strategy for integrating LAN technologies — including Token Ring, Ethernet, Fast Ethernet, FDDI and ATM — in IBM networks, 3Com has developed a technology based on the upcoming VLAN tagging IEEE 802.1Q standard — Token Ringin-Fast Ethernet (TR-in-FE). TR-in-FE technology simpl ...
point to point and point to multi point calls over IP
... cannot speak at the same time as speaker is speaking. => Receiver can use bigger jitter buffer to buffer packet sending speed variation than used in normal VOIP applications. 2. New way to communicate ...
... cannot speak at the same time as speaker is speaking. => Receiver can use bigger jitter buffer to buffer packet sending speed variation than used in normal VOIP applications. 2. New way to communicate ...
LNET Fine Grained Routing - paper
... Fig. 3 is a simple depiction of another possible path that a compute node might use when communicating with an OSS. In this case, the router node’s IB connection is not on the same IB switch as the OSS and, therefore, has a much greater amount of latency and will be restricted to the available bandw ...
... Fig. 3 is a simple depiction of another possible path that a compute node might use when communicating with an OSS. In this case, the router node’s IB connection is not on the same IB switch as the OSS and, therefore, has a much greater amount of latency and will be restricted to the available bandw ...
Timing is everything: Accurate, Minimum-cost, Available Bandwidth Estimation in High-speed Wired Network
... consequently, many existing bandwidth estimation tools report significant estimation error (large variation and low accuracy) [27]. In a similar fashion to measuring the space between packets, minProbe generates probe packets through high-fidelity pacing, by inserting an exact spacing between packet ...
... consequently, many existing bandwidth estimation tools report significant estimation error (large variation and low accuracy) [27]. In a similar fashion to measuring the space between packets, minProbe generates probe packets through high-fidelity pacing, by inserting an exact spacing between packet ...
Timing is Everything: Accurate, Minimum Overhead, Available Bandwidth Estimation in High-speed Wired Networks
... simply counting the number of /I/s between packets is what enables high-fidelity. However, before the SoNIC [26] platform was created, /I/ characters were typically inaccessible from higher layers (L2 or above), because they are discarded by hardware, and definitely were not accessible in software. ...
... simply counting the number of /I/s between packets is what enables high-fidelity. However, before the SoNIC [26] platform was created, /I/ characters were typically inaccessible from higher layers (L2 or above), because they are discarded by hardware, and definitely were not accessible in software. ...
Chapter 7: Label Distribution Protocols
... – This field is known as the request send targeted hellos. A value of 1 indicates that the receiver is requested to send periodic targeted hellos to the source of this hello. A value of 0 makes no such ...
... – This field is known as the request send targeted hellos. A value of 1 indicates that the receiver is requested to send periodic targeted hellos to the source of this hello. A value of 0 makes no such ...
Towards an Accurate AS-level Traceroute Tool
... CIDR: Classless Inter-domain Routing (RFC1519) No implicit mask based on the class of the network Explicit masks passed in the routing protocol Allow aggregation and hierarchical routing ...
... CIDR: Classless Inter-domain Routing (RFC1519) No implicit mask based on the class of the network Explicit masks passed in the routing protocol Allow aggregation and hierarchical routing ...
WorldNet Data Warehouse Albert Greenberg albert@research
... improvement Initial IP-to-AS mapping derived from BGP routing tables Identify a small number of modifications that significantly improve the match rate. 95% match ratio, less than 3% changes, very robust ...
... improvement Initial IP-to-AS mapping derived from BGP routing tables Identify a small number of modifications that significantly improve the match rate. 95% match ratio, less than 3% changes, very robust ...
L8-routing - University of California, Berkeley
... • IP routing allows hosts in one network (IP Link) to communicate with hosts in another • Topology Formation: determining the connectivity graph, i.e., the network. • Routing: Protocols and Process for establishing what paths are used in communicating over that graph and setting up tables. • Forward ...
... • IP routing allows hosts in one network (IP Link) to communicate with hosts in another • Topology Formation: determining the connectivity graph, i.e., the network. • Routing: Protocols and Process for establishing what paths are used in communicating over that graph and setting up tables. • Forward ...
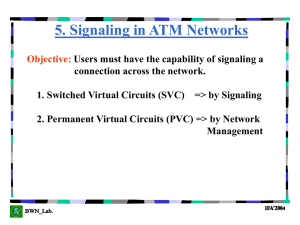
ATM End User
... Remark: Signaling between the end-system and the ATM switch usually takes place over VPI=0 and VCI=5, although this is not always the case. If we implement a feature such as SVC tunneling, the signaling channel will often be over a VPI =/ 0. Also, some proprietary UNI and NNI protocols use VCI =/5 f ...
... Remark: Signaling between the end-system and the ATM switch usually takes place over VPI=0 and VCI=5, although this is not always the case. If we implement a feature such as SVC tunneling, the signaling channel will often be over a VPI =/ 0. Also, some proprietary UNI and NNI protocols use VCI =/5 f ...
Campus Network Design
... Why do we need an EGP? • Scaling to large network Hierarchy Limit scope of failure Fast convergence No manual reconfig (static routes) - high maintenance ...
... Why do we need an EGP? • Scaling to large network Hierarchy Limit scope of failure Fast convergence No manual reconfig (static routes) - high maintenance ...
tcp/ip routing protocols, rip., etc
... similar too (surprise) – BSD 4.2 on VAX (1982 or so) done first and RFC 1058 (1988) later created in widespread use for at least two reasons – widely available, came with that there Sun WS – # routed & is (mostly) all you need to do BSD routed and Cornell gated support it (free) Cisco evolve ...
... similar too (surprise) – BSD 4.2 on VAX (1982 or so) done first and RFC 1058 (1988) later created in widespread use for at least two reasons – widely available, came with that there Sun WS – # routed & is (mostly) all you need to do BSD routed and Cornell gated support it (free) Cisco evolve ...
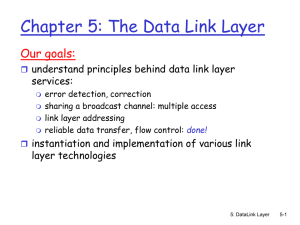
Chapter5_4th - Computer Science Division
... passes data in frame to network layer protocol otherwise, adapter discards frame Type: indicates higher layer protocol (mostly IP ...
... passes data in frame to network layer protocol otherwise, adapter discards frame Type: indicates higher layer protocol (mostly IP ...
Simplifying Manageability, Scalability and Host Mobility in Large-Scale Enterprise Networks using VEIL-click
... Shortest path routing using link state routing protocol on Ethernet switches ID Location separation for better mobility Seattle uses DHT style lookup, VL2 uses a directory service for flooding free lookup No flooding on data plane However, control plane still uses flooding! DHT style routing for sca ...
... Shortest path routing using link state routing protocol on Ethernet switches ID Location separation for better mobility Seattle uses DHT style lookup, VL2 uses a directory service for flooding free lookup No flooding on data plane However, control plane still uses flooding! DHT style routing for sca ...
Internetworking Technology Overview
... OSI Model and Communication Between Systems Information being transferred from a software application in one computer system to a software application in another must pass through each of the OSI layers. If, for example, a software application in System A has information to transmit to a software ap ...
... OSI Model and Communication Between Systems Information being transferred from a software application in one computer system to a software application in another must pass through each of the OSI layers. If, for example, a software application in System A has information to transmit to a software ap ...
Self Organizing Wireless Mesh Networks
... 802.11 ARQ mechanism may have to retransmit the probe or the probe-ack packet several times to get it delivered correctly. This increases the RTT along that hop. Finally, if despite the ARQ mechanism, a probe or a probe-ack packet is lost, the sender node detect the loss, and increases the moving av ...
... 802.11 ARQ mechanism may have to retransmit the probe or the probe-ack packet several times to get it delivered correctly. This increases the RTT along that hop. Finally, if despite the ARQ mechanism, a probe or a probe-ack packet is lost, the sender node detect the loss, and increases the moving av ...
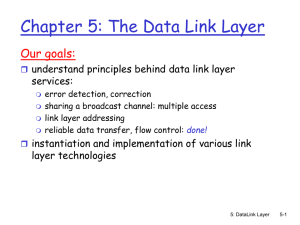
Chapter5
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
RIP V1
... of the sending router. If the field is set to all zeros (0.0.0.0), the address of the sending router is the best next-hop address. The purpose of the Next Hop field is to eliminate packets being routed through extra hops in the system. ...
... of the sending router. If the field is set to all zeros (0.0.0.0), the address of the sending router is the best next-hop address. The purpose of the Next Hop field is to eliminate packets being routed through extra hops in the system. ...