manet-intro
... because users will have to load software or take additional steps to ensure interoperability. ...
... because users will have to load software or take additional steps to ensure interoperability. ...
Routing Information Protocol
... Update Timer (default 30 seconds) – indicates how often the router will send out a routing table update. Invalid Timer (default 180 seconds) – indicates how long a route will remain in a routing table before being marked as invalid, if no new updates are heard about this route. The invalid timer wil ...
... Update Timer (default 30 seconds) – indicates how often the router will send out a routing table update. Invalid Timer (default 180 seconds) – indicates how long a route will remain in a routing table before being marked as invalid, if no new updates are heard about this route. The invalid timer wil ...
CENT 305 Information Security
... ◦ Use Access Control Lists (ACLs) to examine and control packet flow based on source/destination IP addresses in the network ◦ Simple firewalls examine IP network layer headers source/destination IP address, protocol (udp, tcp), inbound or outbound traffic can reject (deny), discard, or forward ...
... ◦ Use Access Control Lists (ACLs) to examine and control packet flow based on source/destination IP addresses in the network ◦ Simple firewalls examine IP network layer headers source/destination IP address, protocol (udp, tcp), inbound or outbound traffic can reject (deny), discard, or forward ...
RuggedBackbone™ RX1500/1501
... OSPF (Open Shortest Path First) OSPF is a routing protocol that determines the best path for routing IP traffic over a TCP/IP network based on link states between nodes and several quality parameters. OSPF is an interior gateway protocol (IGP), which is designed to work within an autonomous system. ...
... OSPF (Open Shortest Path First) OSPF is a routing protocol that determines the best path for routing IP traffic over a TCP/IP network based on link states between nodes and several quality parameters. OSPF is an interior gateway protocol (IGP), which is designed to work within an autonomous system. ...
Carrier Ethernet: The next generation network and service
... By terminating TDM PDH circuits as close to subscriber as possible Through statistical multiplexing and local switching ...
... By terminating TDM PDH circuits as close to subscriber as possible Through statistical multiplexing and local switching ...
Networking Basics - Undergraduate Research in Consumer
... • Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. • Since packets are treated independently, it is possible to route around link and node failures. • Since every packet must carry the full address of the destination, the overh ...
... • Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. • Since packets are treated independently, it is possible to route around link and node failures. • Since every packet must carry the full address of the destination, the overh ...
Common WAN Components and Issues
... Split horizon is another potential issue. Split horizon is a technique used in routing to help prevent routing loops. With split horizon, a router will not advertise a route to another network out of the interface that it learned the route on. With a point-to-multipoint WAN connection, a router may ...
... Split horizon is another potential issue. Split horizon is a technique used in routing to help prevent routing loops. With split horizon, a router will not advertise a route to another network out of the interface that it learned the route on. With a point-to-multipoint WAN connection, a router may ...
Chapter5-LANs - ECE Users Pages
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host ...
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host ...
Slides - TERENA> Events> tnc2006
... – WAN interface gets an /64 prefix -instead of specific IPv6 address- by using IPCPv6. If there is a need for a static address assignment to the school router, the Frame-Interface-ID* should also be provided. – Internal LAN interfaces are automatically configured using DHCP-PD (prefix delegation). T ...
... – WAN interface gets an /64 prefix -instead of specific IPv6 address- by using IPCPv6. If there is a need for a static address assignment to the school router, the Frame-Interface-ID* should also be provided. – Internal LAN interfaces are automatically configured using DHCP-PD (prefix delegation). T ...
Exploration CCNA4 - Information Systems Technology
... •First, with Frame Relay, customers only pay for the local loop, and for the bandwidth they purchase from the network provider. –Distance between nodes is not important. –with dedicated lines, customers pay for an end-to-end connection. That includes the local loop and the network link. ...
... •First, with Frame Relay, customers only pay for the local loop, and for the bandwidth they purchase from the network provider. –Distance between nodes is not important. –with dedicated lines, customers pay for an end-to-end connection. That includes the local loop and the network link. ...
An Approach to Fixed/Mobile Converged Routing
... to fixed networks. Second generation cellular networks have been modified to provide limited data services, and third generation systems undergoing rollout now have been designed to deliver IP connectivity to the end user. Projecting technological trends, it is seen as inevitable that the future glo ...
... to fixed networks. Second generation cellular networks have been modified to provide limited data services, and third generation systems undergoing rollout now have been designed to deliver IP connectivity to the end user. Projecting technological trends, it is seen as inevitable that the future glo ...
Chapter6
... • Using subinterfaces for inter-VLAN routing results in a less complex physical configuration (less cables) than using separate physical interfaces. • On the other hand, using subinterfaces with a trunk port results in a more complex software configuration, which can be difficult to troubleshoot. • ...
... • Using subinterfaces for inter-VLAN routing results in a less complex physical configuration (less cables) than using separate physical interfaces. • On the other hand, using subinterfaces with a trunk port results in a more complex software configuration, which can be difficult to troubleshoot. • ...
Routing - La Salle University
... IP(v4) address consists of 32 bits and only the first part must be looked at by a router until a match is found and after that only the second part must be considered. ...
... IP(v4) address consists of 32 bits and only the first part must be looked at by a router until a match is found and after that only the second part must be considered. ...
TCP, IGP, EGP etc. - La Salle University
... Routing Information Protocol is a set of rules defined by RFC (Request for Comments) 1058 that specifies how routers exchange information. RIP uses a “distance vector algorithm” in which routers periodically exchange their entire routing tables. A router compares the entries of the table it receives ...
... Routing Information Protocol is a set of rules defined by RFC (Request for Comments) 1058 that specifies how routers exchange information. RIP uses a “distance vector algorithm” in which routers periodically exchange their entire routing tables. A router compares the entries of the table it receives ...
CN2-Unit-1-Packet-switching-networks-by-Deepa
... Link State Routing Each router will flood information to the state of the links that connects to neighbors Allows routers to construct map of entire network and then uses Djikstra s algorithm. If state is changed the router detects the change and floods the new information to network ...
... Link State Routing Each router will flood information to the state of the links that connects to neighbors Allows routers to construct map of entire network and then uses Djikstra s algorithm. If state is changed the router detects the change and floods the new information to network ...
hostv - Applied Research Laboratory
... routers and virtual interfaces. In its simplest form a virtual link models a unidirectional, fixed bandwidth link interconnecting adjacent virtual routers belonging to the same vNet. Virtual links originate and terminate at virtual interfaces. A virtual router implements a specific vNet protocol, fo ...
... routers and virtual interfaces. In its simplest form a virtual link models a unidirectional, fixed bandwidth link interconnecting adjacent virtual routers belonging to the same vNet. Virtual links originate and terminate at virtual interfaces. A virtual router implements a specific vNet protocol, fo ...
100% Accurate Answers !!!
... C. All ports on both the switches must be set as access ports. D. One of the two switches must be configured as a VTP server. E. A rollover cable is required to connect the two switches together. F. A router must be used to forward VTP traffic between VLANs. Answer: BD 15. What are three IPv6 transi ...
... C. All ports on both the switches must be set as access ports. D. One of the two switches must be configured as a VTP server. E. A rollover cable is required to connect the two switches together. F. A router must be used to forward VTP traffic between VLANs. Answer: BD 15. What are three IPv6 transi ...
THE OPTIMIZATION OF STEPPING STONE DETECTION: PACKET CAPTURING STEPS MOHD NIZAM OMAR
... allow such tools to be constructed, a kernel must have some facilities that give a userlevel program access to raw, unprocessed network traffic. There are facilities such as NIT [20] in SunOS, the Ultrix Packet Filter [21] in DEC’s Ultrix and Snoop in SGI’s IRIX, and BSD Packet Filter [22]. All of t ...
... allow such tools to be constructed, a kernel must have some facilities that give a userlevel program access to raw, unprocessed network traffic. There are facilities such as NIT [20] in SunOS, the Ultrix Packet Filter [21] in DEC’s Ultrix and Snoop in SGI’s IRIX, and BSD Packet Filter [22]. All of t ...
NetVanta 3200 Tolly Group Report
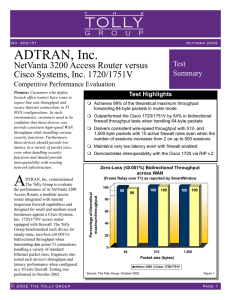
... NetVanta 3200 Access Router versus Cisco Systems, Inc. 1720/1751V Competitive Performance Evaluation Premise: Customers who deploy branch office routers have come to expect line rate throughput and secure Internet connections in T1 WAN configurations. In such environments, customers need to be confi ...
... NetVanta 3200 Access Router versus Cisco Systems, Inc. 1720/1751V Competitive Performance Evaluation Premise: Customers who deploy branch office routers have come to expect line rate throughput and secure Internet connections in T1 WAN configurations. In such environments, customers need to be confi ...
Demystifying Layer 2 and Layer 3 VPNs
... 3.1.1 Layer 2 Virtual Circuits and Virtual Paths ............................................................................................................................................................................. 11 Layer 2 Virtual Circuits ................................................. ...
... 3.1.1 Layer 2 Virtual Circuits and Virtual Paths ............................................................................................................................................................................. 11 Layer 2 Virtual Circuits ................................................. ...
1-network
... – If the packet is meant for a device on the local host IP gets the MAC address for the device and sends it directly to the host – For a remote packet it first looks up the routing table for an explicit route to the network. – If an explicit route is not available it sends it to a default ...
... – If the packet is meant for a device on the local host IP gets the MAC address for the device and sends it directly to the host – For a remote packet it first looks up the routing table for an explicit route to the network. – If an explicit route is not available it sends it to a default ...
Lecture 1: Course Introduction and Overview
... • Telephone: operator sets up connection between the caller and the receiver – Once the connection is established, conversation can continue for hours ...
... • Telephone: operator sets up connection between the caller and the receiver – Once the connection is established, conversation can continue for hours ...
ppt
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...